Shehacks intervasity ctf 2023
This ctf onsite at usiu , nairobi . I particpated online.
web category
Graph1
This was an easy chalenge that tested knowledge in graphql queries
the graphql endpoint was located at /graphql.
for more info on how to enumerate graphql » here
So basicaly if we send the query below we get introspection on the grapql endpoint
|
|
You can then use » here to visualize the schema
remember to set the content-type to “appication/graphql” when sending the request
From this we find out that there is a field known as getFlag. We can then run the query below to get the flag . It was base64 encoded , so we decode it to get the flag
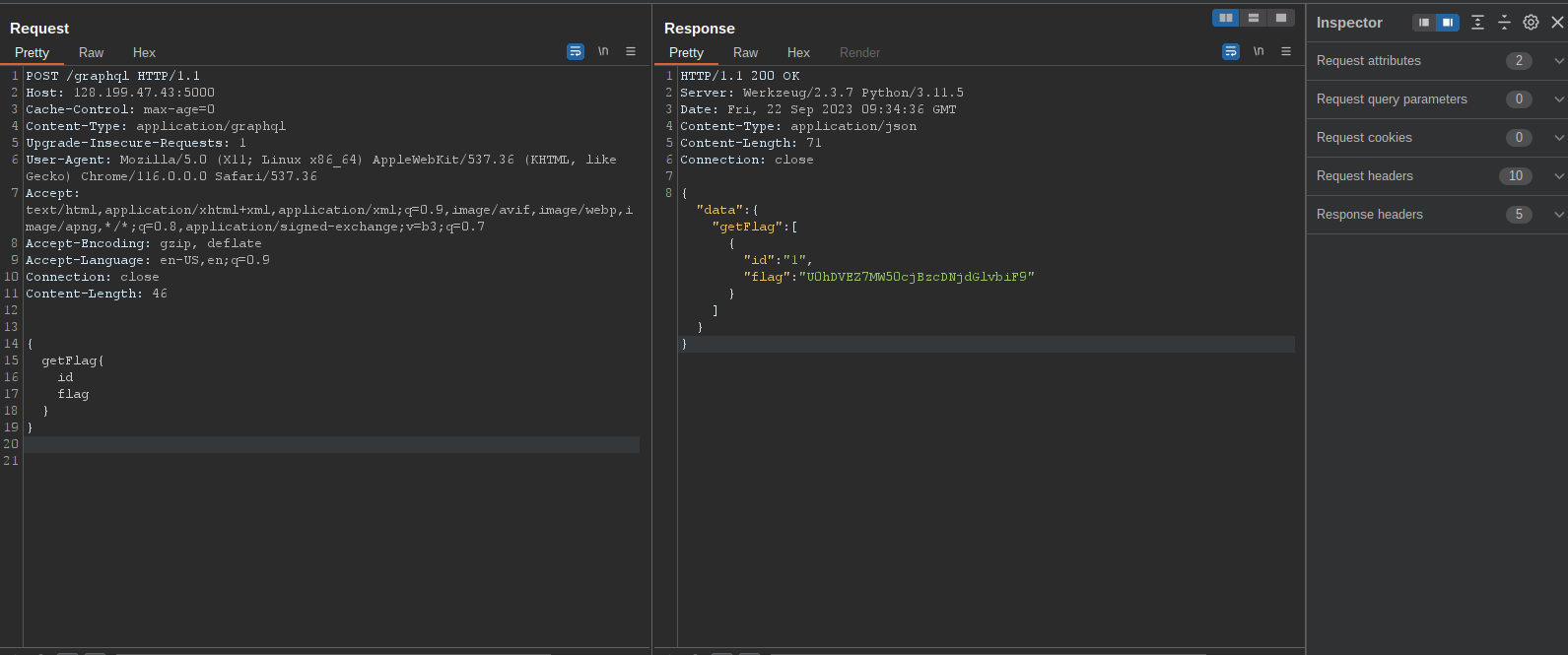
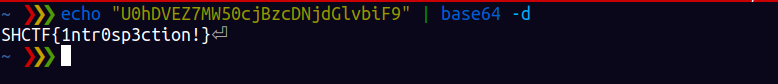
X marks the spot
In this challenge we are given a web application login field , i tried sql injection at first an an error was thrown
|
|
This indicated that the appication is vulnerable to xpath injection
you can check the payloads » hacktricks xpath
i tried the payload
|
|
this is able to bypass login and i get the result
|
|
to move laterally through accounts i used the following payload , i achieved this after after trying lots of payloads
|
|
by changing the number above we can basically login as different users , in this case 3 gets us the flag.
PS i got first blood on this challenge :)
|
|
secrets
For this challenge you are provided with a signin page and you can also register.
We have to manipulate the cookie to become the admin user. For this i used the tool flask-unsign , you can get it » here
|
|
We then have to change the uid to 1 and username to admin and then sign the cookie with secretkey ‘SheHacks’
|
|
Using this cookie we can get the flag : flag{s3c3ts_4re_n0_l0ng3r_s4f3}
forensics category
SnifferDog1
How many packets in total passed through port 445 shctf{Ans}
For this we just use the filter “tcp.port == 445” then check the bottom right of wireshrk for number of packets shctf{10223}
Sniffer Dog2
What is the 6th disallowed item listed in http://192.168.56.103:8081/robots.txt?
For this we just use the filter “ip.addr == 192.168.56.103 && tcp.port == 8081 && http” then find “robots.txt”
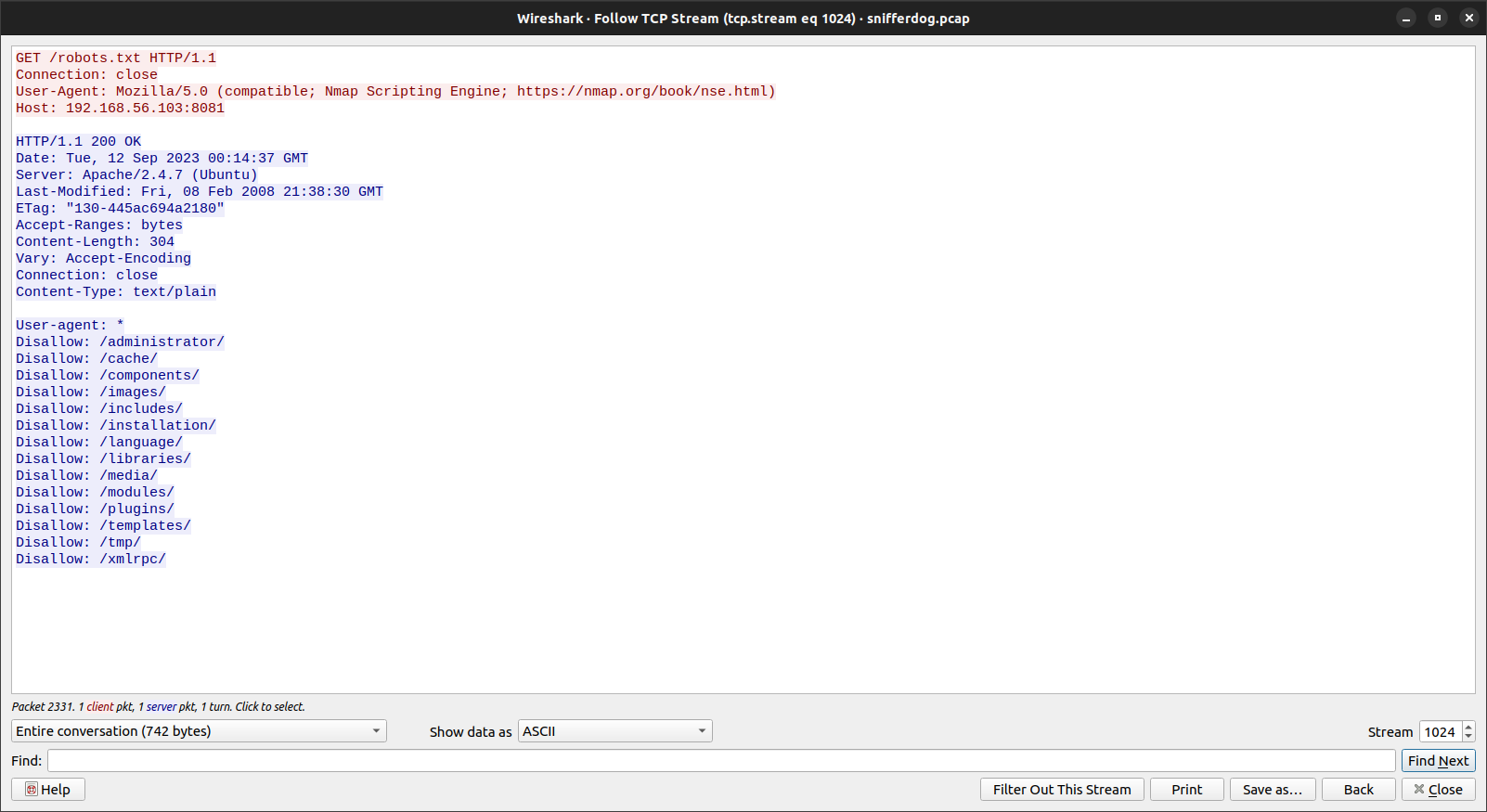
shctf{installation}
SnifferDog3
What version of Jenkins is running on 192.168.56.103? shctf{VersionOnly}
For this we just use the filter “ip.addr == 192.168.56.103” then find “jenkins”
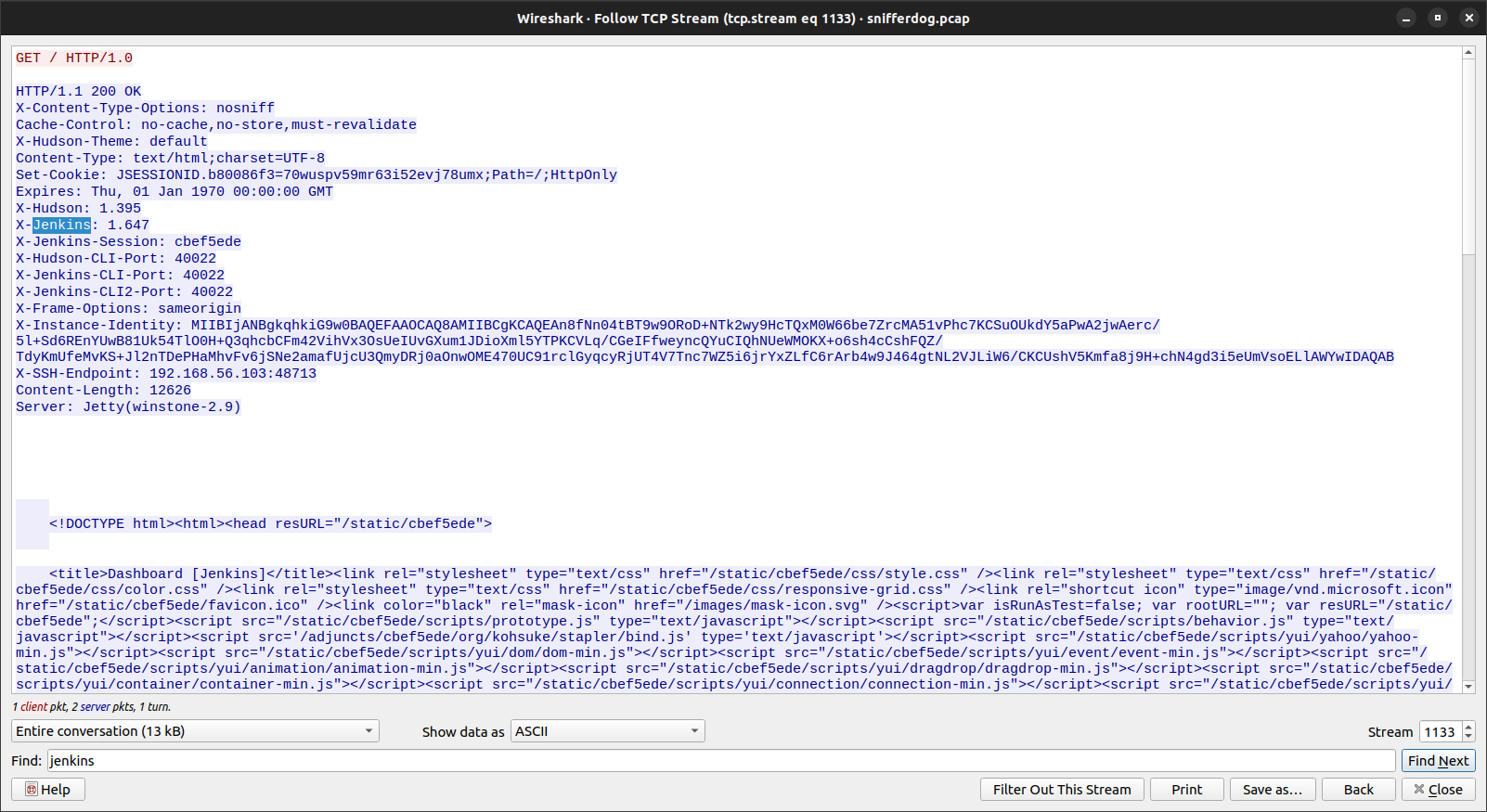
shctf{1.647}
SnifferDog4
What is the domain SID for 192.168.56.103 shctf{S…}
For this we just use the filter “ip.addr == 192.168.56.103” then find “S-1-5” this is the format for sid you can learn more » here
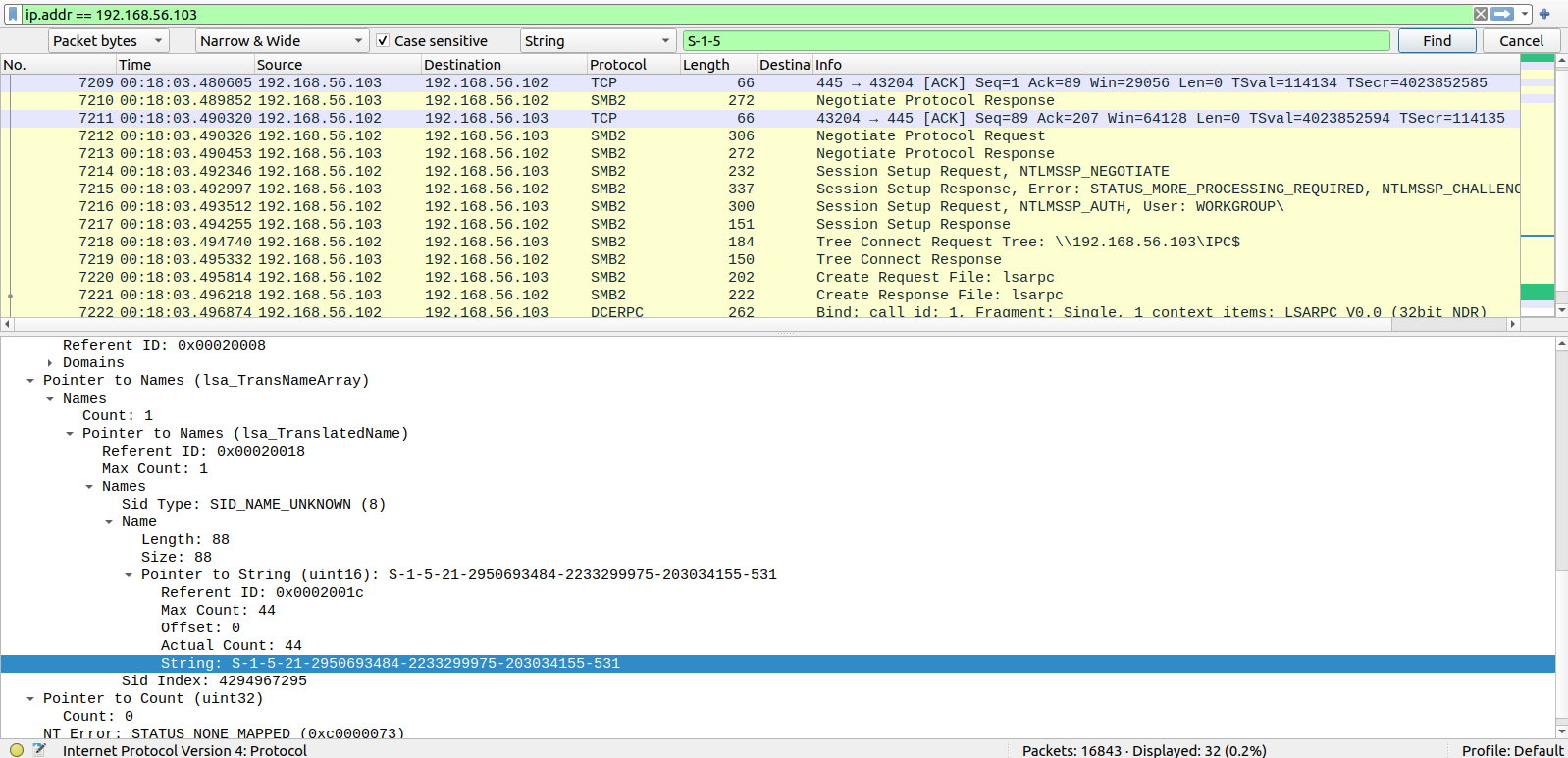
shctf{S-1-5-21-2950693484-2233299975-203034155}

