SOC Lab Setup
Introduction
This is my documentation of a lab setup for a SOC (Security operation center) environment. I decided to pursue this project with the aim of learning about endpoint detection and response. SOC analysis is more about blue teaming and detecting threats in an environment.
As is did this i followed steps from this blog post » here . Credits!!
Summary
- Setup
- Intrusion
- Blocking attacks
- Tuning False Positives
Setup
- Setup of vms(ubuntu server and windows)
NOTE: im using a computer with the following specs:
- 8gb RAM
- intel i5
- 500gb hard disk
You might want to allocate different amount of resources for your vms depending on the specs of your hardware. As for me my specs constrained me , my vms were slow esp the windows vm. I allocated 2gb for the windows vm and 1gb for the ubuntu server.
- Installing of limacharlie sensor
LimaCharlie is a very powerful “SecOps Cloud Platform” . Check it out » here
For the C2 i used sliver-server by bishop fox
1
|
Sliver is an open source cross-platform adversary emulation/red team framework, it can be used by organizations of all sizes to perform security testing
|
I created a C2 payload and dropped it in the windows vm.
Using the implant we can access the windows vm from the ubuntu server attack machine.
Below is a list of running processes
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
|
.
├── [0] [System Process]
│ └── [4] System
│ ├── [1444] Memory Compression
│ ├── [72] Registry
│ └── [528] smss.exe
├── [632] csrss.exe
├── [732] csrss.exe
├── [776] wininit.exe
│ ├── [864] services.exe
│ │ ├── [2160] Sysmon64.exe
│ │ ├── [3708] svchost.exe
│ │ ├── [1348] svchost.exe
│ │ ├── [1508] svchost.exe
│ │ ├── [1668] svchost.exe
│ │ │ └── [5768] audiodg.exe
│ │ ├── [2152] vm3dservice.exe
│ │ │ └── [2284] vm3dservice.exe
│ │ ├── [1128] svchost.exe
│ │ │ ├── [648] taskhostw.exe
│ │ │ ├── [1960] sihost.exe
│ │ │ ├── [2436] CompatTelRunner.exe
│ │ │ │ ├── [2488] conhost.exe
│ │ │ │ └── [1236] CompatTelRunner.exe
│ │ │ ├── [2520] MicrosoftEdgeUpdate.exe
│ │ │ └── [3460] taskhostw.exe
│ │ ├── [2124] vmtoolsd.exe
│ │ ├── [4368] svchost.exe
│ │ ├── [3500] SecurityHealthService.exe
│ │ ├── [6548] svchost.exe
│ │ ├── [1636] svchost.exe
│ │ ├── [1772] svchost.exe
│ │ ├── [1788] svchost.exe
│ │ ├── [3100] SgrmBroker.exe
│ │ ├── [1304] svchost.exe
│ │ ├── [2168] VGAuthService.exe
│ │ ├── [2132] rphcp.exe
│ │ ├── [628] svchost.exe
│ │ ├── [896] spoolsv.exe
│ │ ├── [992] svchost.exe
│ │ │ ├── [1284] ShellExperienceHost.exe
│ │ │ ├── [1580] RuntimeBroker.exe
│ │ │ ├── [3240] BackgroundTransferHost.exe
│ │ │ ├── [4376] backgroundTaskHost.exe
│ │ │ ├── [5572] RuntimeBroker.exe
│ │ │ ├── [740] unsecapp.exe
│ │ │ ├── [1156] dllhost.exe
│ │ │ ├── [5608] SearchApp.exe
│ │ │ ├── [6004] RuntimeBroker.exe
│ │ │ ├── [4352] RuntimeBroker.exe
│ │ │ ├── [2476] WmiPrvSE.exe
│ │ │ ├── [3680] WmiPrvSE.exe
│ │ │ ├── [3892] TextInputHost.exe
│ │ │ ├── [3932] StartMenuExperienceHost.exe
│ │ │ ├── [4488] MoUsoCoreWorker.exe
│ │ │ ├── [1256] RuntimeBroker.exe
│ │ │ ├── [3552] smartscreen.exe
│ │ │ ├── [5064] SearchApp.exe
│ │ │ └── [1216] TiWorker.exe
│ │ ├── [2984] dllhost.exe
│ │ ├── [2092] TrustedInstaller.exe
│ │ ├── [2376] svchost.exe
│ │ ├── [3912] SearchIndexer.exe
│ │ ├── [5652] svchost.exe
│ │ ├── [1172] svchost.exe
│ │ │ ├── [3152] ctfmon.exe
│ │ │ └── [4800] CompatTelRunner.exe
│ │ │ └── [2944] conhost.exe
│ │ ├── [1520] svchost.exe
│ │ ├── [1532] svchost.exe
│ │ ├── [1832] msdtc.exe
│ │ ├── [736] svchost.exe
│ │ ├── [4852] sppsvc.exe
│ │ ├── [5172] svchost.exe
│ │ ├── [1292] svchost.exe
│ │ ├── [1628] svchost.exe
│ │ ├── [1640] svchost.exe
│ │ └── [2120] svchost.exe
│ ├── [876] lsass.exe
│ └── [1016] fontdrvhost.exe
├── [784] winlogon.exe
│ ├── [1008] fontdrvhost.exe
│ └── [1040] dwm.exe
├── [3328] explorer.exe
│ ├── [3512] SecurityHealthSystray.exe
│ ├── [3880] vmtoolsd.exe
│ ├── [4272] OneDrive.exe
│ └── [6984] cmd.exe
│ ├── [1696] CONTINUED_CARRY.exe
│ └── [3612] conhost.exe
├── [6808] setup.exe
│ ├── [7032] setup.exe
│ └── [3008] MicrosoftEdgeUpdate.exe
└── [6952] Microsoft.SharePoint.exe
⚠️ Security Product(s): Sysmon64, Windows Smart Screen
|
Inturn we can observe the malware in the limacharlie telementery. We can detect our maliciuos process apart from the the legitimate processes. we can also view it network connections.
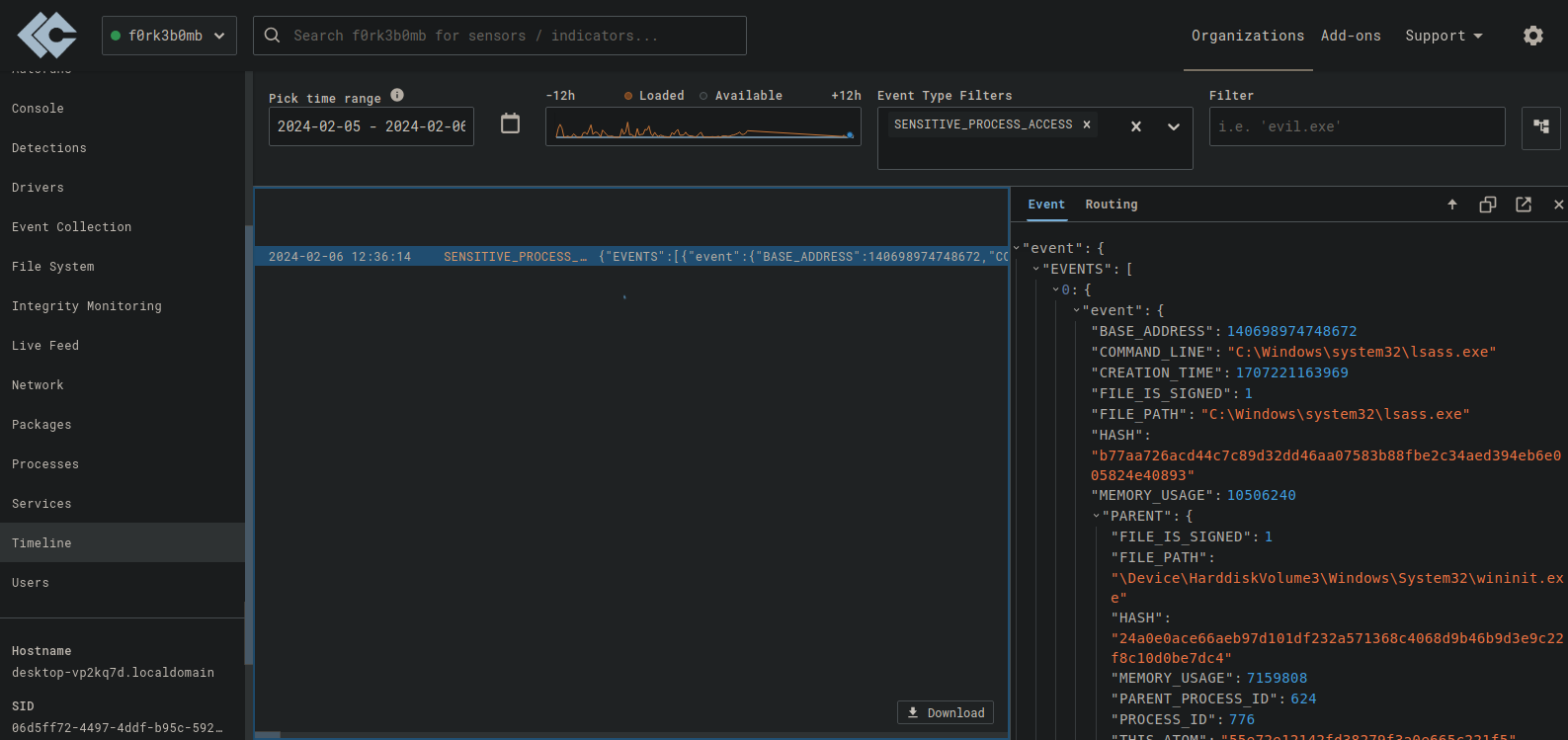
Intrusion
I can steal creds by dumping lsass.exe from the windows box memory to my attack machine
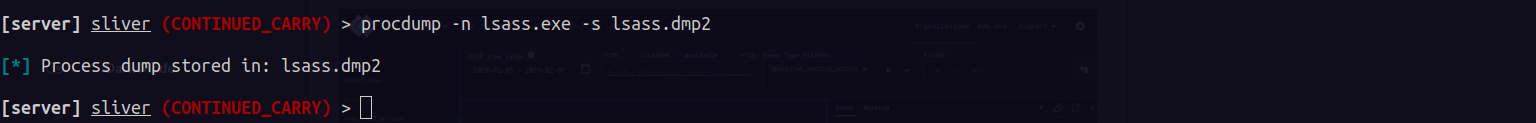
This will generate telementery in limacharkie that we can search with “SENSITIVE_PROCESS_ACCESS”

We can create an edr rule to alert once this type of activity occurs
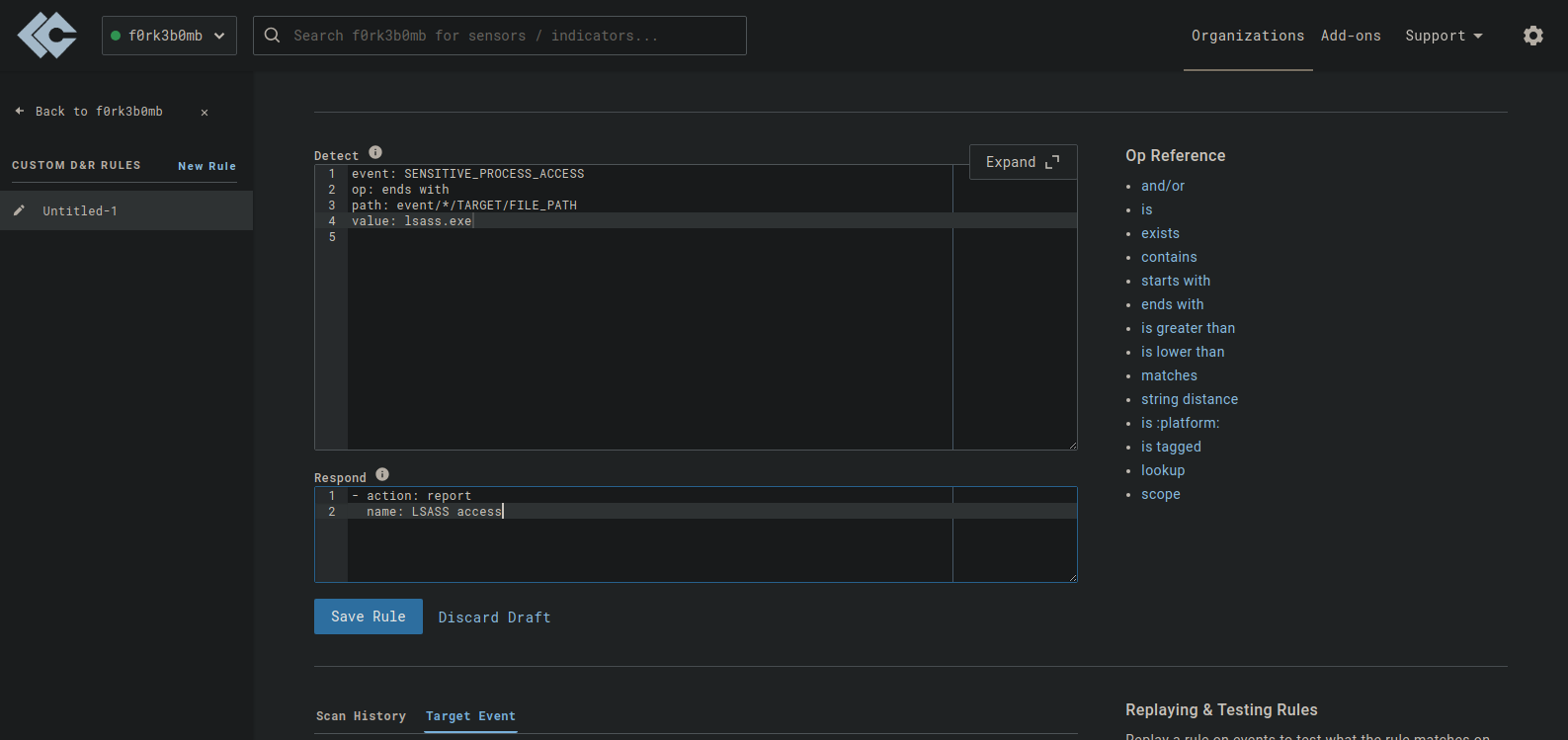
1
2
3
4
|
event: SENSITIVE_PROCESS_ACCESS
op: ends with
path: event/*/TARGET/FILE_PATH
value: lsass.exe
|
This rule will detect “SENSITIVE_PROCEE_ACCESS” with process being “lsass.exe”
To respond we use:
1
2
|
- action: report
name: LSASS access
|
This will generate a detection report that we can view in the detections menu.
Blocking attacks
Here we are going to craft rules to take action when detections are made
in thbis i ran thsi command :
1
|
vssadmin delete shadows /all
|
Which will delete volume shadow copies. This is just an example of a process that may indicate suspicious activity on a system
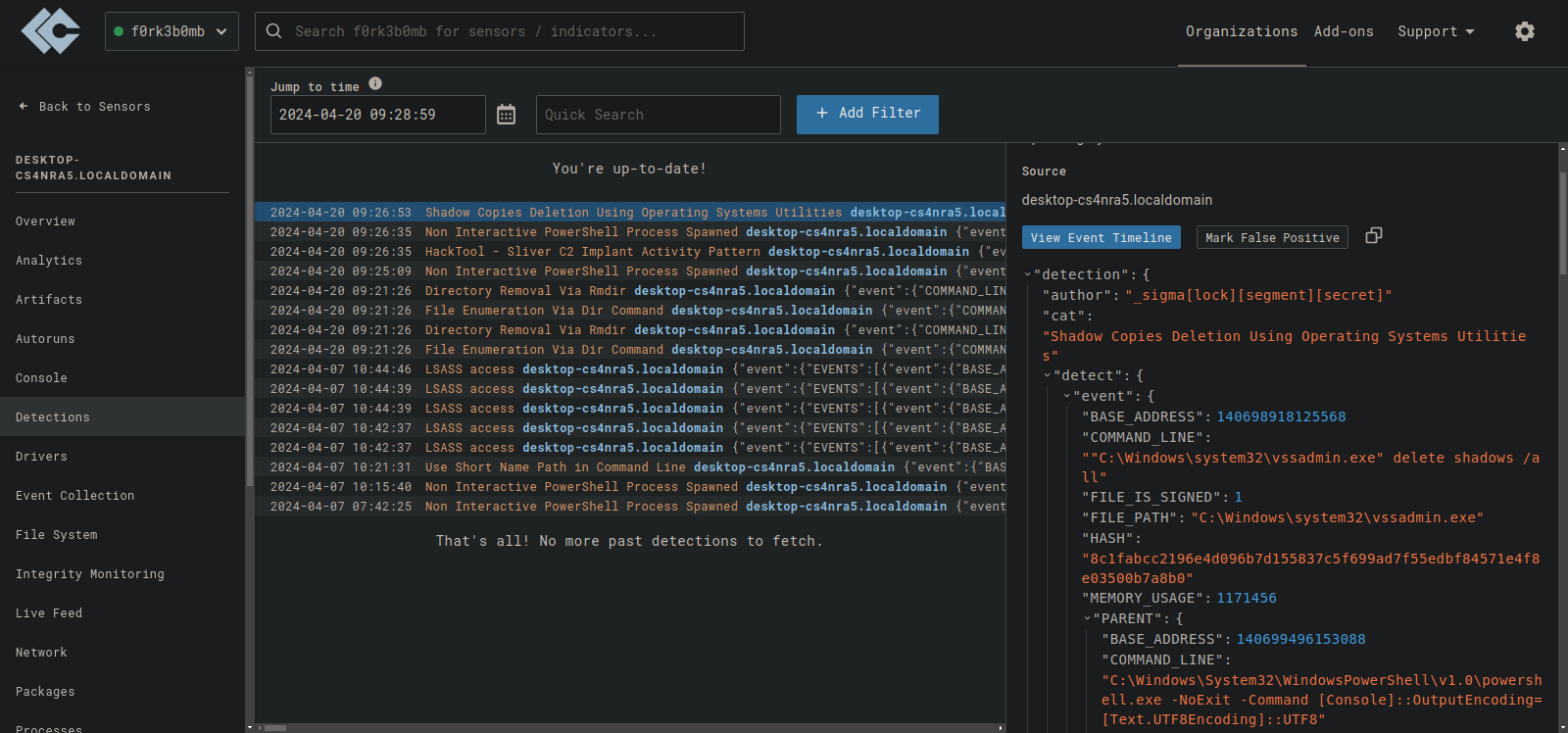
Then we craft an Response rule:
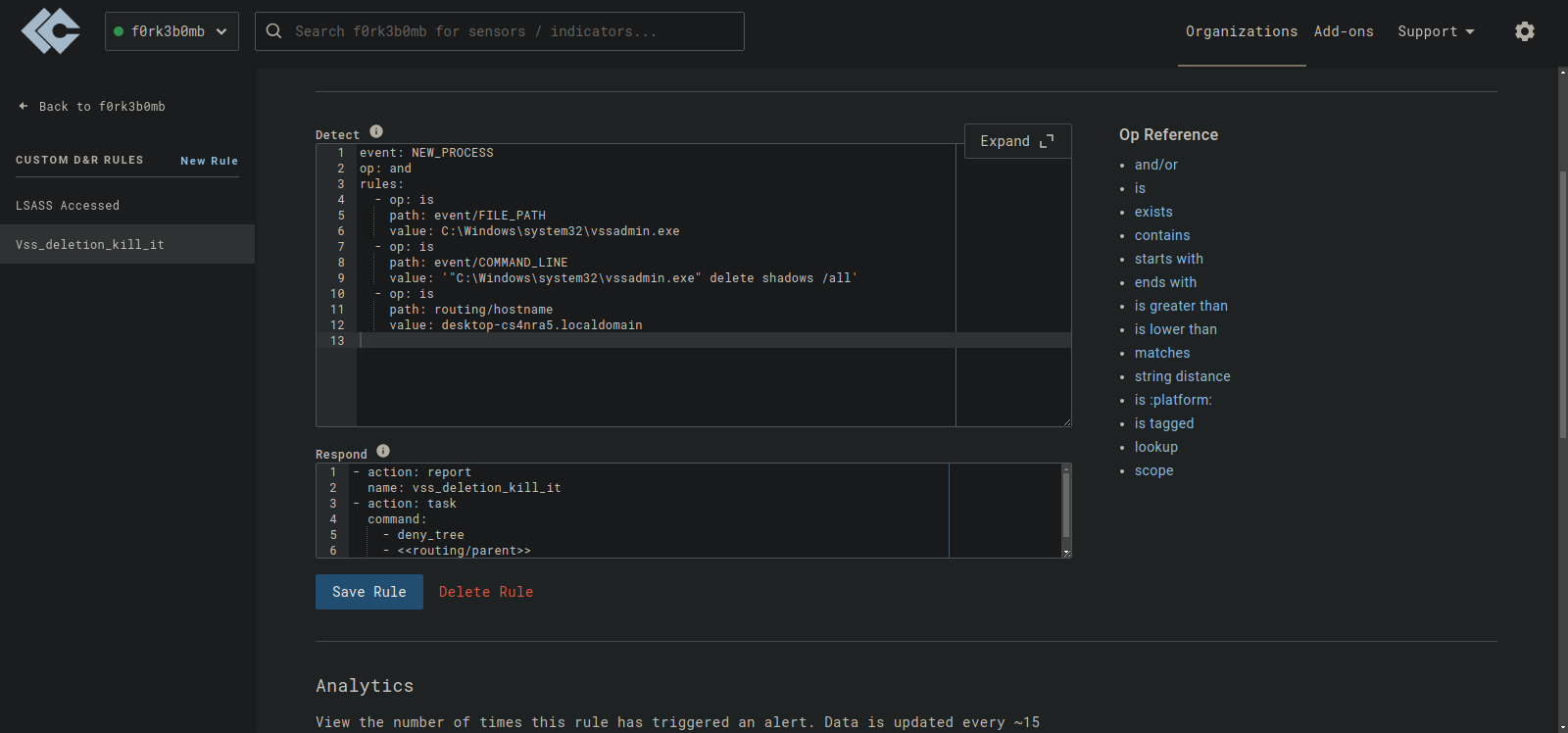
This rule will terminate the parent process when it is detected.
1
2
3
4
5
6
|
- action: report
name: vss_deletion_kill_it
- action: task
command:
- deny_tree
- <<routing/parent>>
|
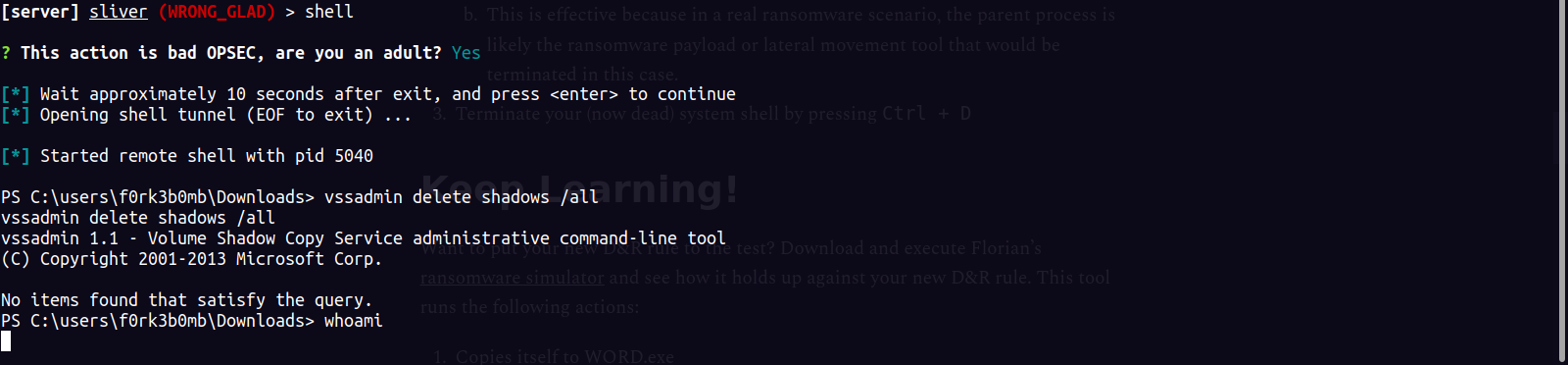
This hung shell is an indication that it worked succesfully
Tuning False Positives
Here we craft a false positive detection rule. This is whereby we can prevent alerts when normal system processes are run, thus causing alot of noise.
I crafted to detect when whoami.exe is run. This is just an example.
1
2
3
4
5
6
7
8
9
10
11
|
op: and
rules:
- op : is
path: cat
value: Whoami Utility Execution
- op: is
path: detect/event/FILE_PATH
value: C:\Windows\system32\whoami.exe
- op: is
path: detect/event/COMMAND_LINE
value: '"C:\Windows\system32\whoami.exe"'
|
After testing it:
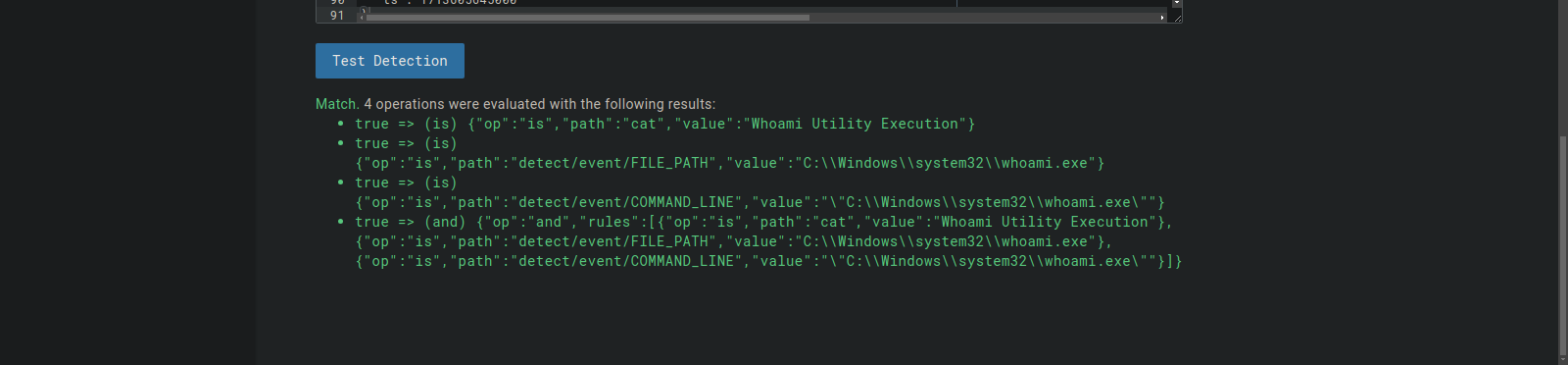
It works!!
If i run whoami when the rule is enabled i get no alaert, however whn i disable it i get an alert.
Automated Yara Scanning
1
2
|
YARA is a tool primarily used for identifying and classifying malware based on textual or binary patterns. It allows researchers and security professionals to craft rules that describe unique characteristics of specific malware families or malicious behaviors.
|
There are well crafted rules for sliver (our c2 server) on the internet. We will use this » here
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
ule sliver_github_file_paths_function_names {
meta:
author = "NCSC UK"
description = "Detects Sliver Windows and Linux implants based on paths and function names within the binary"
strings:
$p1 = "/sliver/"
$p2 = "sliverpb."
$fn1 = "RevToSelfReq"
$fn2 = "ScreenshotReq"
$fn3 = "IfconfigReq"
$fn4 = "SideloadReq"
$fn5 = "InvokeMigrateReq"
$fn6 = "KillSessionReq"
$fn7 = "ImpersonateReq"
$fn8 = "NamedPipesReq"
condition:
(uint32(0) == 0x464C457F or (uint16(0) == 0x5A4D and uint16(uint32(0x3c)) == 0x4550)) and (all of ($p*) or 3 of ($fn*))
}
rule sliver_proxy_isNotFound_retn_cmp_uniq {
meta:
author = "NCSC UK"
description = "Detects Sliver implant framework based on some unique CMPs within the Proxy isNotFound function. False positives may occur"
strings:
$ = {C644241800C381F9B3B5E9B2}
$ = {8B481081F90CAED682}
condition:
(uint32(0) == 0x464C457F or (uint16(0) == 0x5A4D and uint16(uint32(0x3c)) == 0x4550)) and all of them
}
rule sliver_nextCCServer_calcs {
meta:
author = "NCSC UK"
description = "Detects Sliver implant framework based on instructions from the nextCCServer function. False positives may occur"
strings:
$ = {4889D3489948F7F94839CA????48C1E204488B0413488B4C1308}
condition:
(uint32(0) == 0x464C457F or (uint16(0) == 0x5A4D and uint16(uint32(0x3c)) == 0x4550)) and all of them
}
|
We will also need a rule to detect when yara is matched.
1
2
3
4
5
6
7
8
|
event: YARA_DETECTION
op: and
rules:
- not: true
op: exists
path: event/PROCESS/*
- op: exists
path: event/RULE_NAME
|
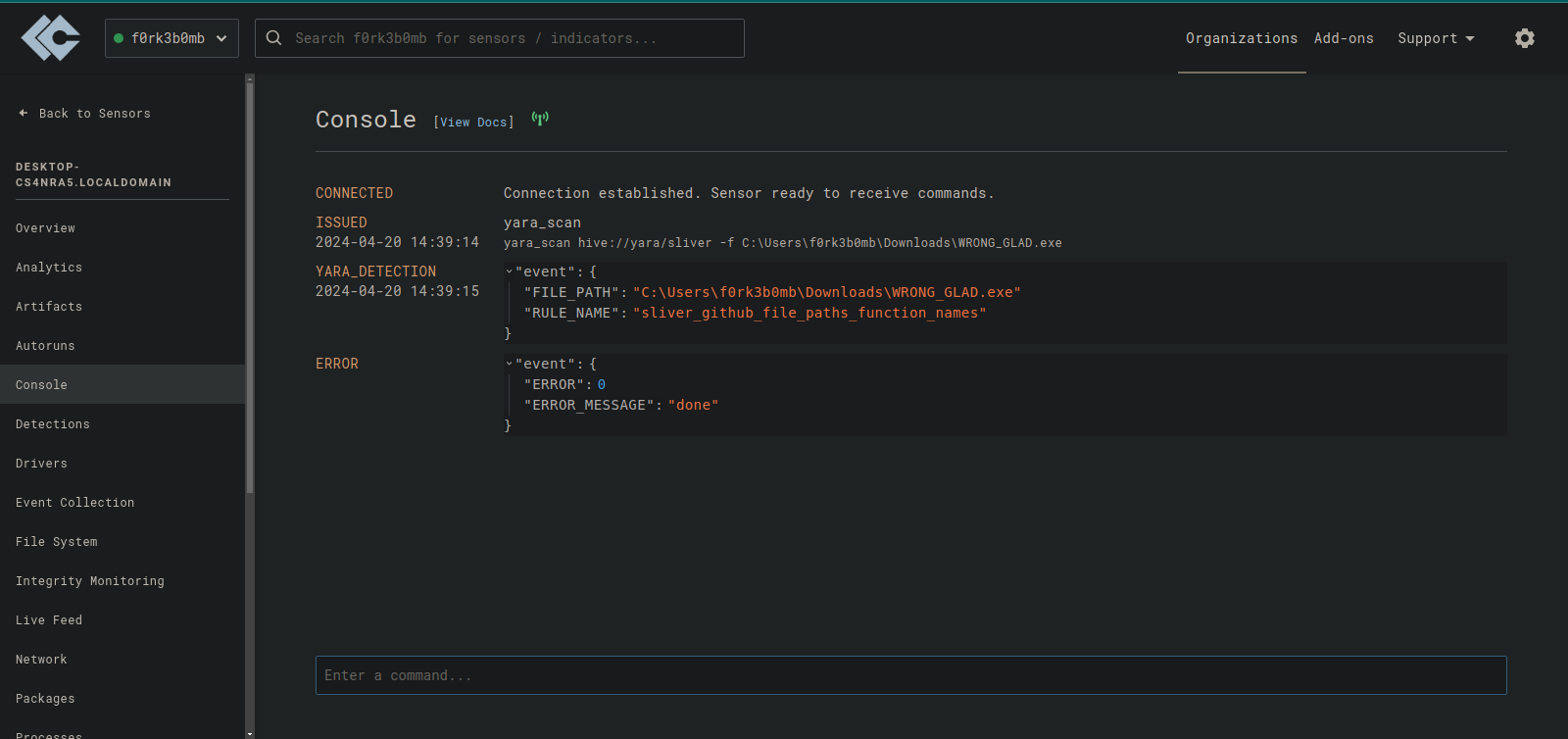
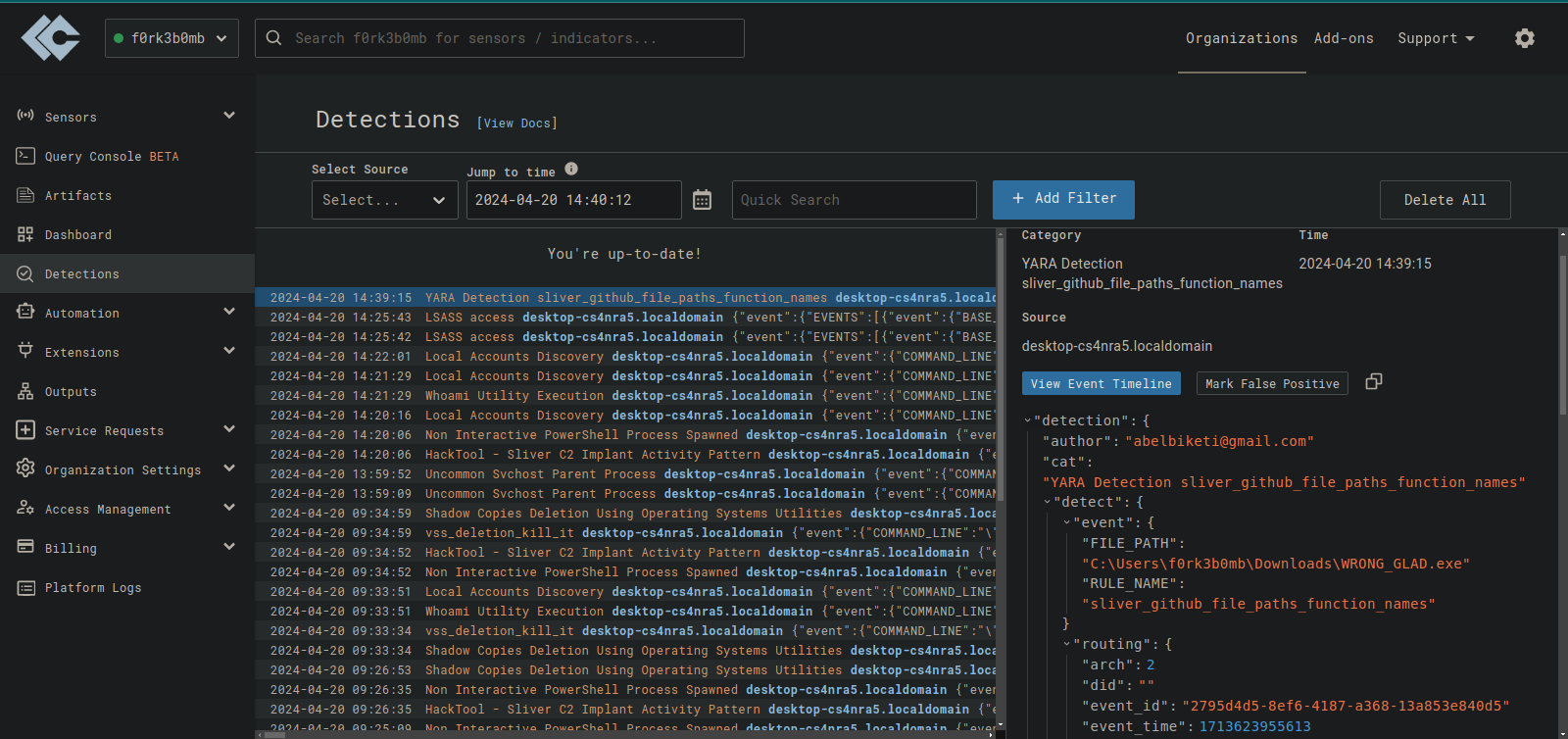
From here we can create rules to automatically scan new executables and those in the downloads directory.
With this we can uleash the full power of the EDR to scan and detect malicious processes and files
Until next time!! HACK THE PLANET















