Windows event log analysis is an important skill in threat hunting. These logs silently record system events, security incidents, and user interactions, providing crucial insights into system health and security. In this blog, we will explore the art of Windows Event Log analysis
Im going to discuss log analysis of windows events in linux, we will be utilizing a tool called chainsaw, you can get it » here.
In this tutorial i will be analysing the files from cybertalents blue scholarship.
1. chainsaw search
an attacker after compromising the machine added a new account as admin. can you find the name of the new account? flag format : flag{md5 of string}
file »» ex1
In windows, each event has a unique event id. So we have to find event id for account creation , a quick google search
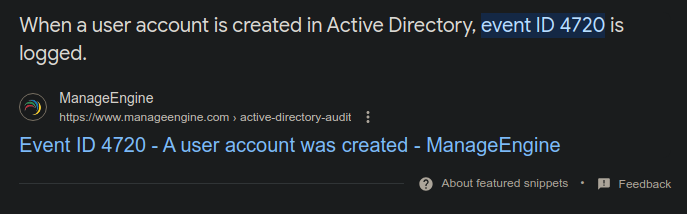
Then in chainsaw
|
|
Here we can filter events with the event id 4720.
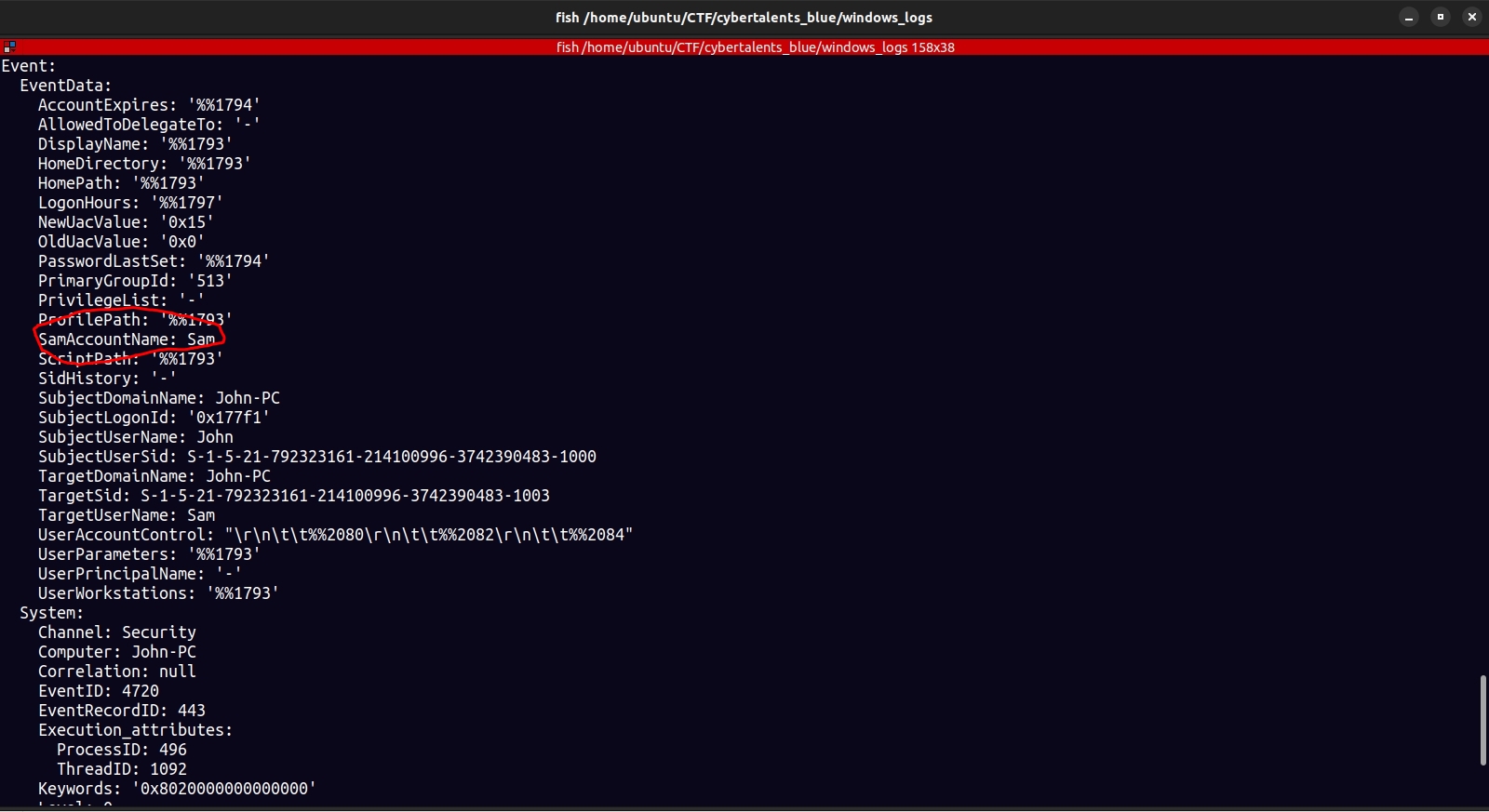
SAM means security account manager , it is a database that stores accounts on windows systems. Usename is sam md5hash ba0e0cde1bf72c28d435c89a66afc61a.
flag{ba0e0cde1bf72c28d435c89a66afc61a}
2. chainsaw hunt
file »» here
|
|
Since this is account failed login it has event id 4776 for failed login from domain controller. The domain controller in this case is HYDRA-DC.MARVEL.local.
Since chainsaw has rules to detect certain events , you can use the folowing command to hunt for events
|
|
This returns alot of output , but retuns events in a format we can easily comprehend.
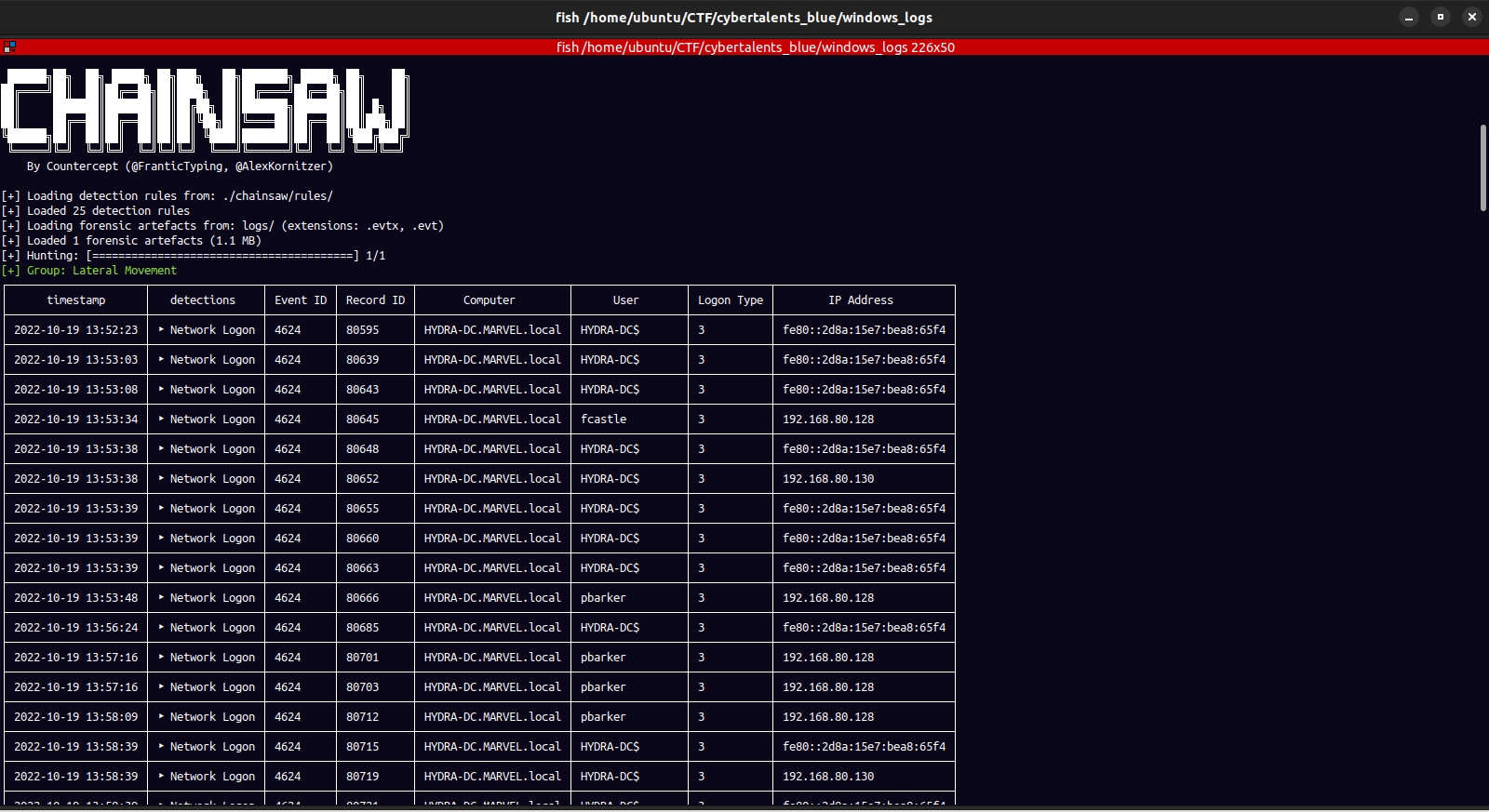
|
|
You can use the command above to get more info. Now here is where the fun begins.
From the logs we can see that there are several users lke pbarker,fcasle, Administrator and these avents are have a common ipaddress “192.168.80.128”
If we search for the following users in the sigma output , we can find the sid
pbarker : S-1-5-21-271597537-2992796785-3713134209-1105
fcastle: S-1-5-21-271597537-2992796785-3713134209-1103
Adminitrator : S-1-5-21-271597537-2992796785-3713134209-500
The structure of an sid is as follows :
S-1-5-21-
Where:
S: A constant prefix indicating that it is a Security Identifier.
1: Revision number (currently always 1).
5: Identifier authority value (the identifier authority for Windows is always 5).
21: The identifier authority’s top-level domain identifier. The actual number may vary depending on the Windows version or configuration but is typically 21 for Windows domains.
<relative_id>: A relative identifier that uniquely identifies a specific security principal within the domain. For users and groups, this relative ID is usually the RID (Relative Identifier) assigned by the domain controller.
so in this case domain sid is “S-1-5-21-271597537-2992796785-3713134209”
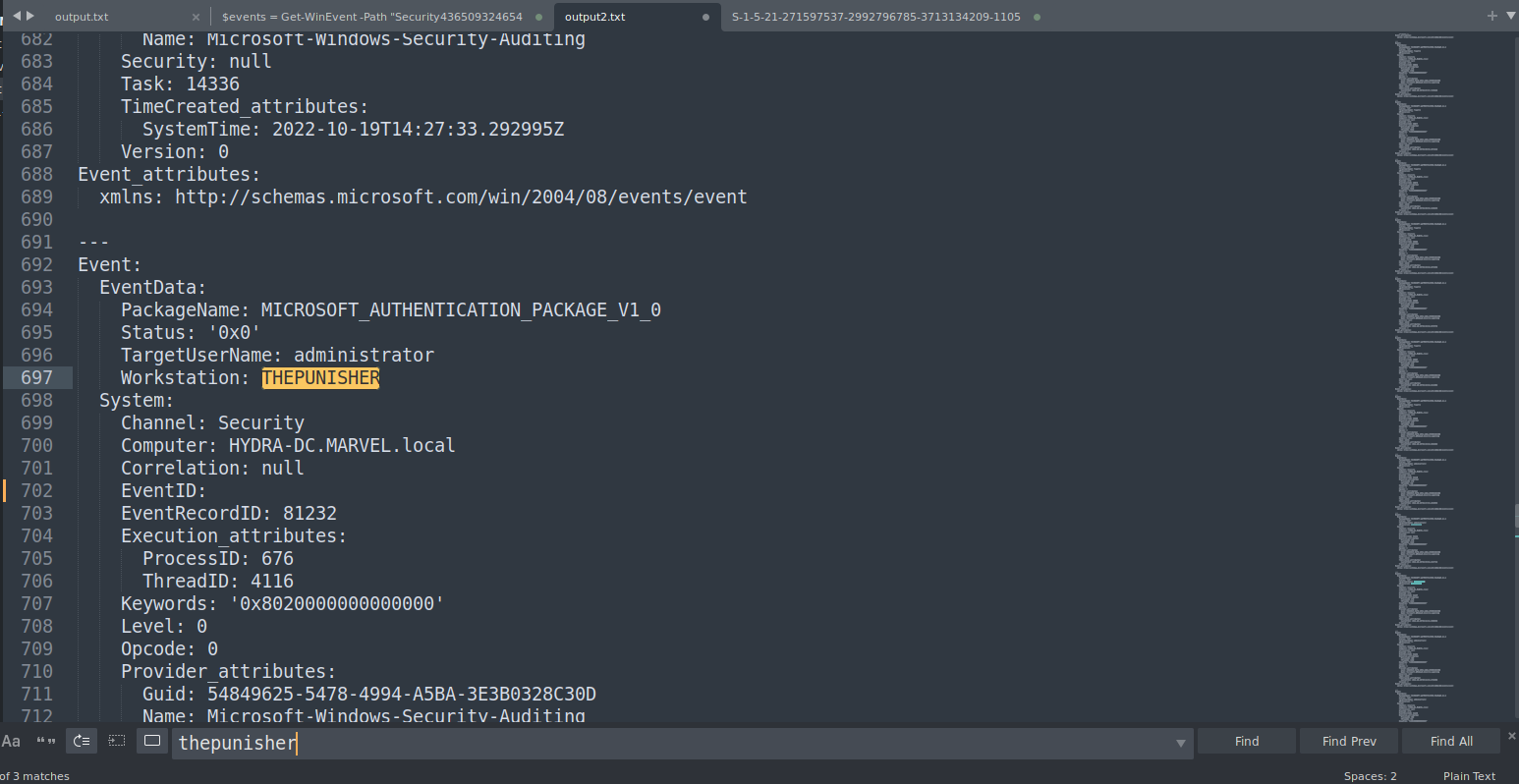
To get the workstation you can ue the command we used earlier to filter events using event id
|
|
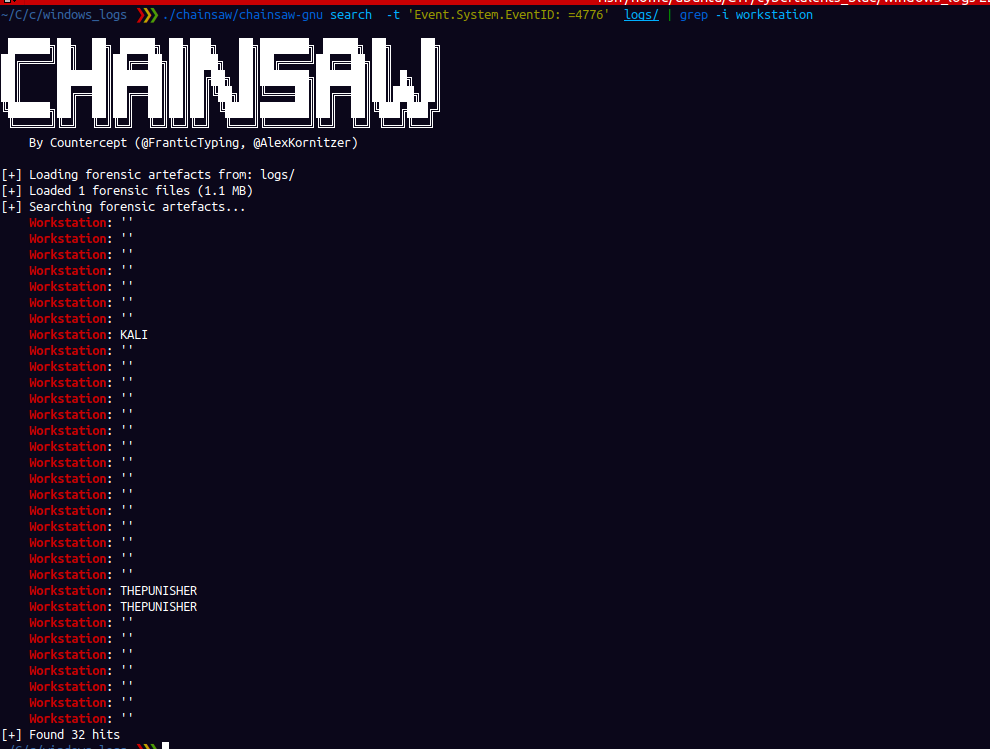
workstation: THEPUNISHER
flag is Flag{S-1-5-21-271597537-2992796785-3713134209_192.168.80.128_THEPUNISHER}
